Contents:
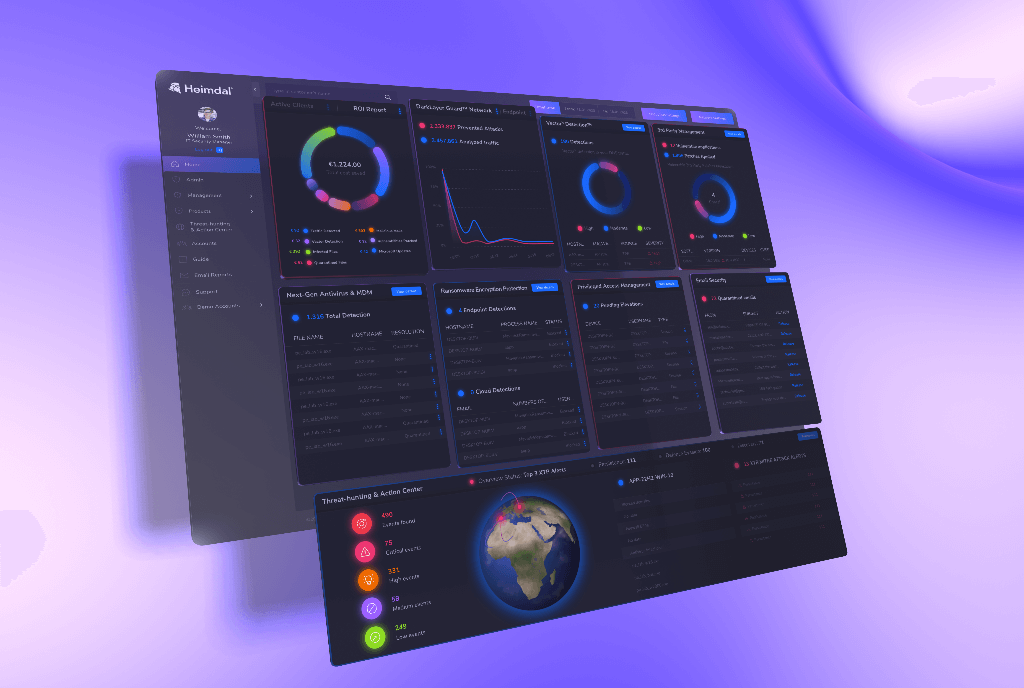
With Heimdal XDR, you gain complete visibility into XDR alerts, network traffic, user behavior, and endpoint activity.
It makes investigating threats much easier, showing you how threats happened and when they occurred. This lets you to swiftly identify the cause behind each XDR alert trigger.
Plus, you can take immediate action right from our Unified Platform.
With Heimdal XDR, businesses can tighten their defense strategy with little effort. This way, security teams can focus on proactive threat hunting and response
– Nabil Nistar, Head of Product Marketing
By the end of this article, you will know:
- When does Heimdal generate XDR alerts;
- What is the Heimdal XDR Agent, and how does it work;
- The best methods for effectively managing XDR alerts using our Award-Winning Heimdal XDR Dashboard.
Want to learn about XDR. Read our guide to XDR.
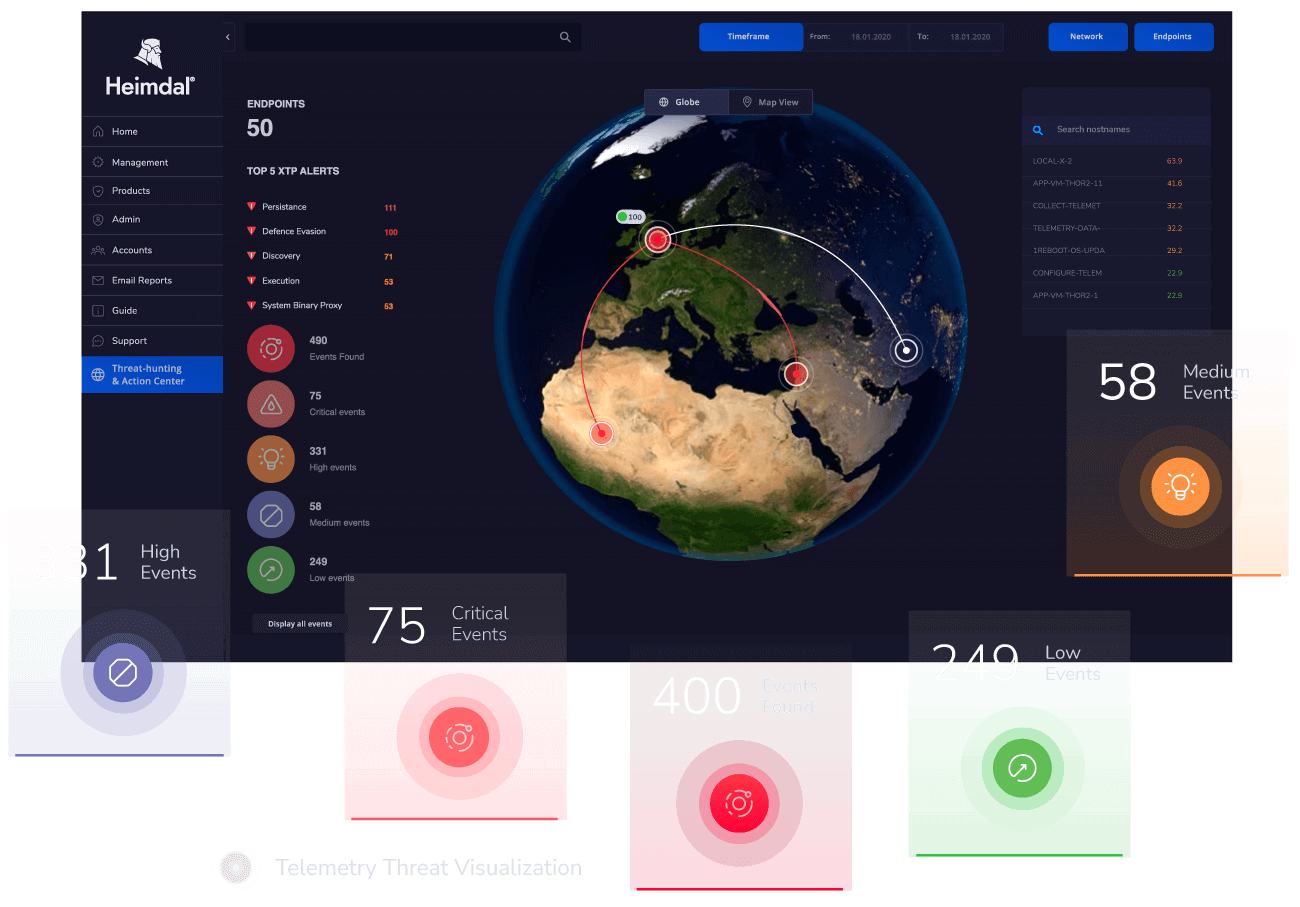
When does Heimdal Generate XDR Alerts?
Heimdal XDR generates alerts whenever it finds possible threats on your network, endpoints, or cloud setup. These XDR alerts give you information about the threats such as type, impacted system or device, severity level, and much more.
Heimdal XDR Agent
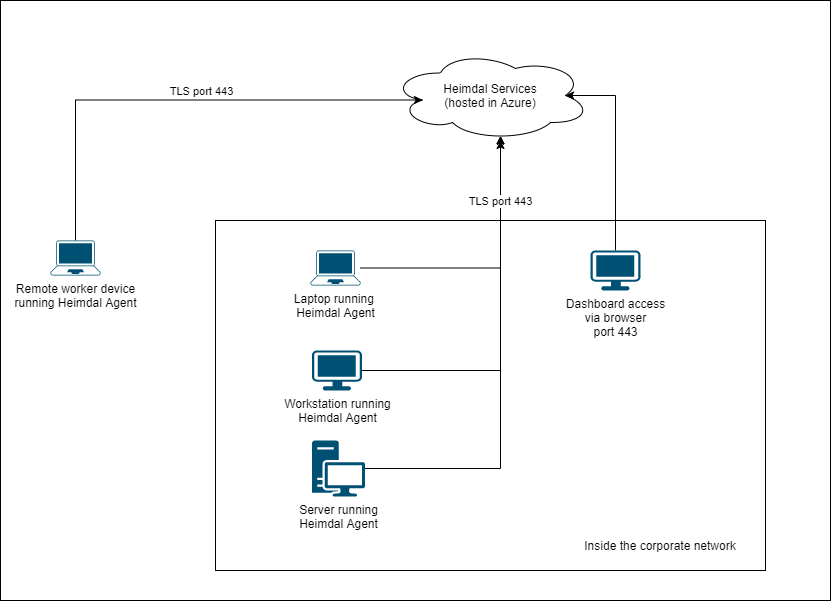
The Heimdal XDR Agent safeguards each individual device, whether it’s on-site or remote. This agent installs on the device and remains active continuously. It ensures compliance with your security rules and promptly sends XDR alerts or reports if it detects a threat.
Secure communication between the Heimdal Agent and the Heimdal Dashboard occurs through Transport Layer Security (TLS).
Threat Prevention
In the Threat Prevention view, you get an up-close perspective of how your computer’s file system is being kept safe and secure. The module includes the following views:
DarkLayer Guard
In the DarkLayer Guard section, you will find information about the Alazyed Traffic Requests, Prevented Attacks, and Prevented Attacks %.
Pressing the See Details button takes you to the following details: Blocked Traffic, Malware Blocked, TTPC, Date, and Action.
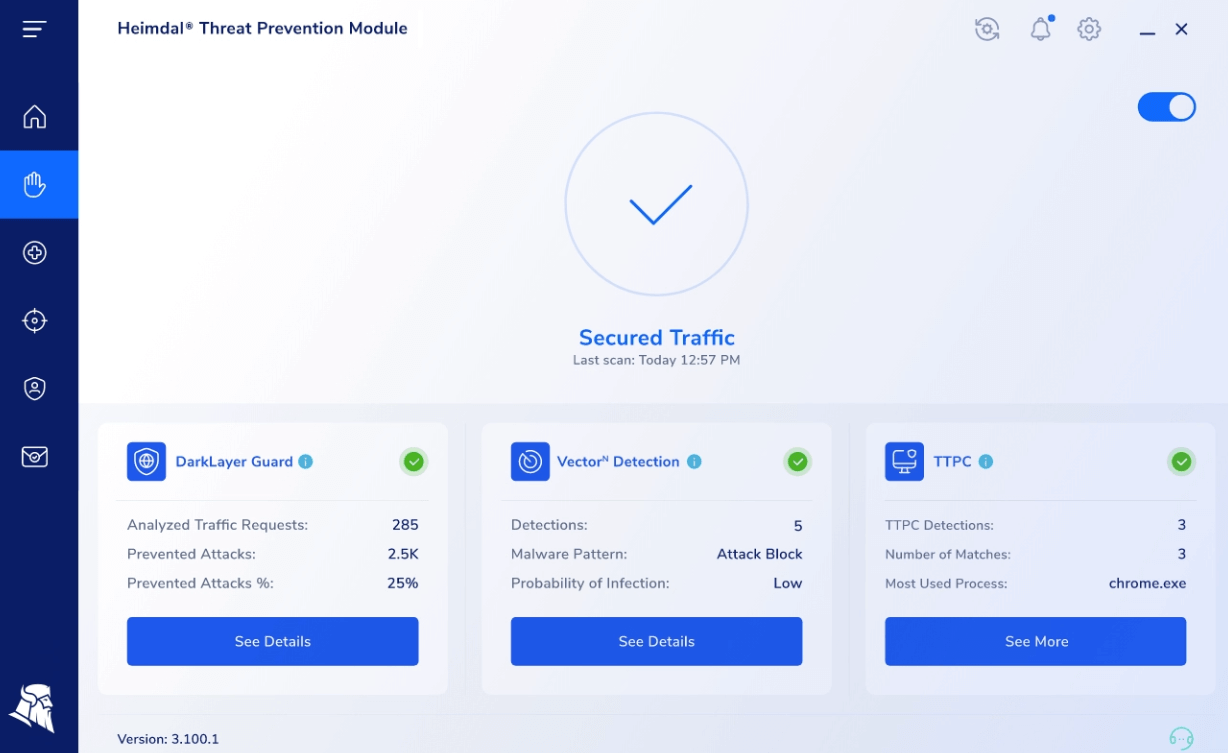
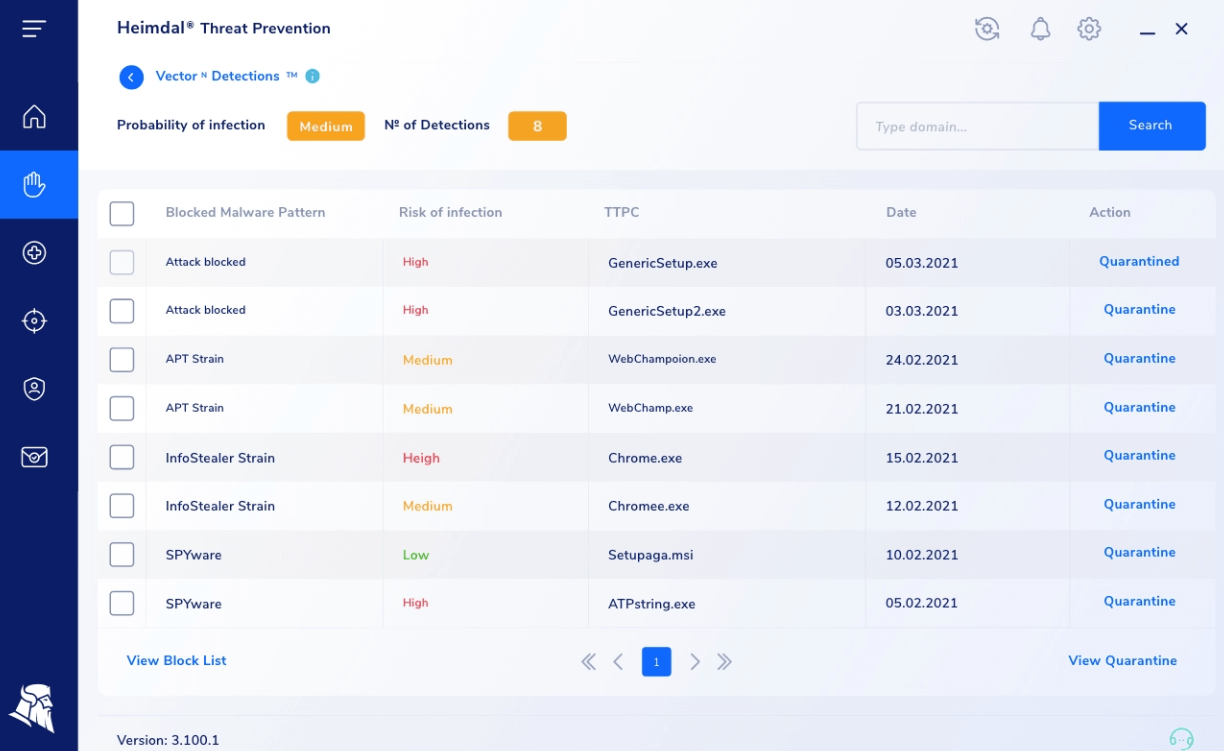
VectorN Detection
In the VectorN Detections section, you can see the VectorN Detections, Malware Pattern, and Probability of Infection.
Pressing the See Details button takes you to the following details: Probability of infection, Number of Detections, Blocked Malware Pattern, Risk of infection, TTPC, Date, and Action.
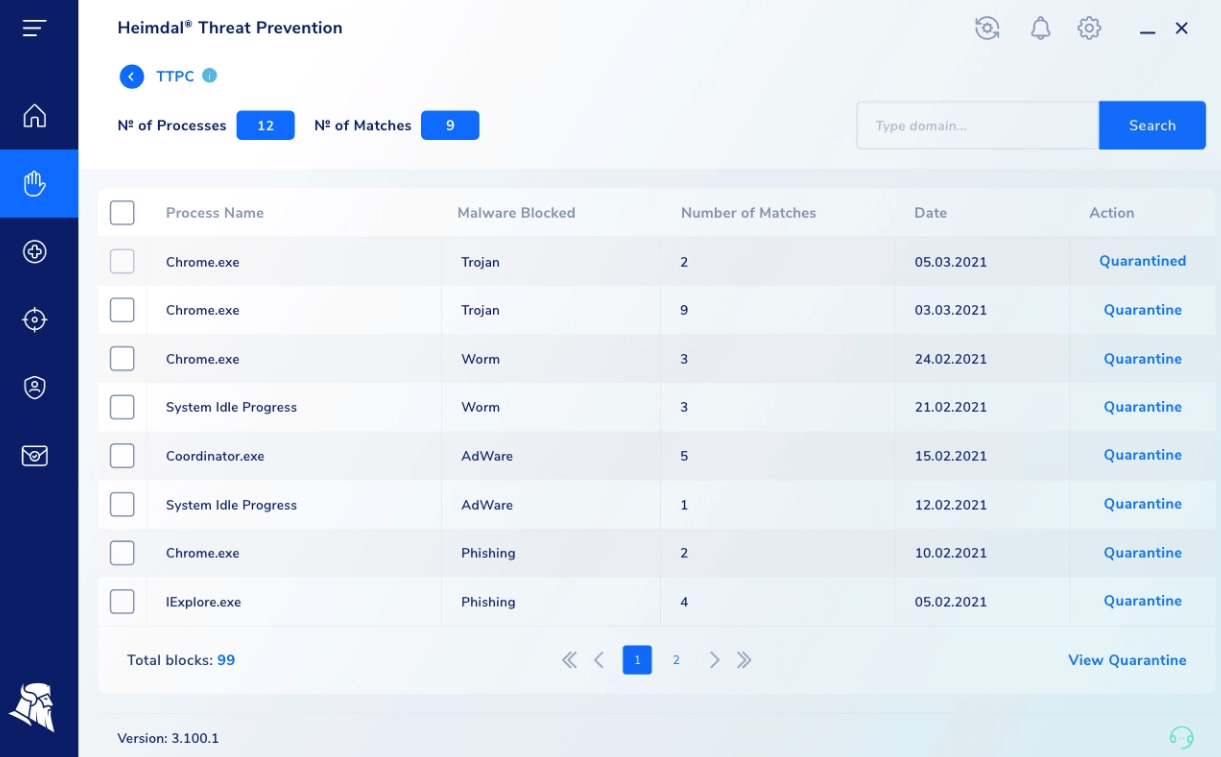
TTPC
In the TTPC section, you will find details like TTPC Detections, Number of Matches, and Most Used Processes.
Pressing the See Details button takes you to the following details: Number of Processes, Number of Matches, Process Name, Malware Blocked, Number of Matches, Date, and Action.
When enabled, whenever a malicious domain is queried, a pop-up window will appear on your screen.
While you, as a user, can handle XDR alerts from the Heimdal Agent, IT Admins require a more in-depth grasp of device activities. This is why exploring how to manage XDR alerts from our Dashboard is essential. Keep reading to discover the details.
Endpoint Detection
In the Endpoint Detection view, you get a comprehensive perspective of how your machine’s file system is being protected. You’ll observe useful statistics such as the number of quarantined or infected files, Firewall alerts, and even detections of ransomware.
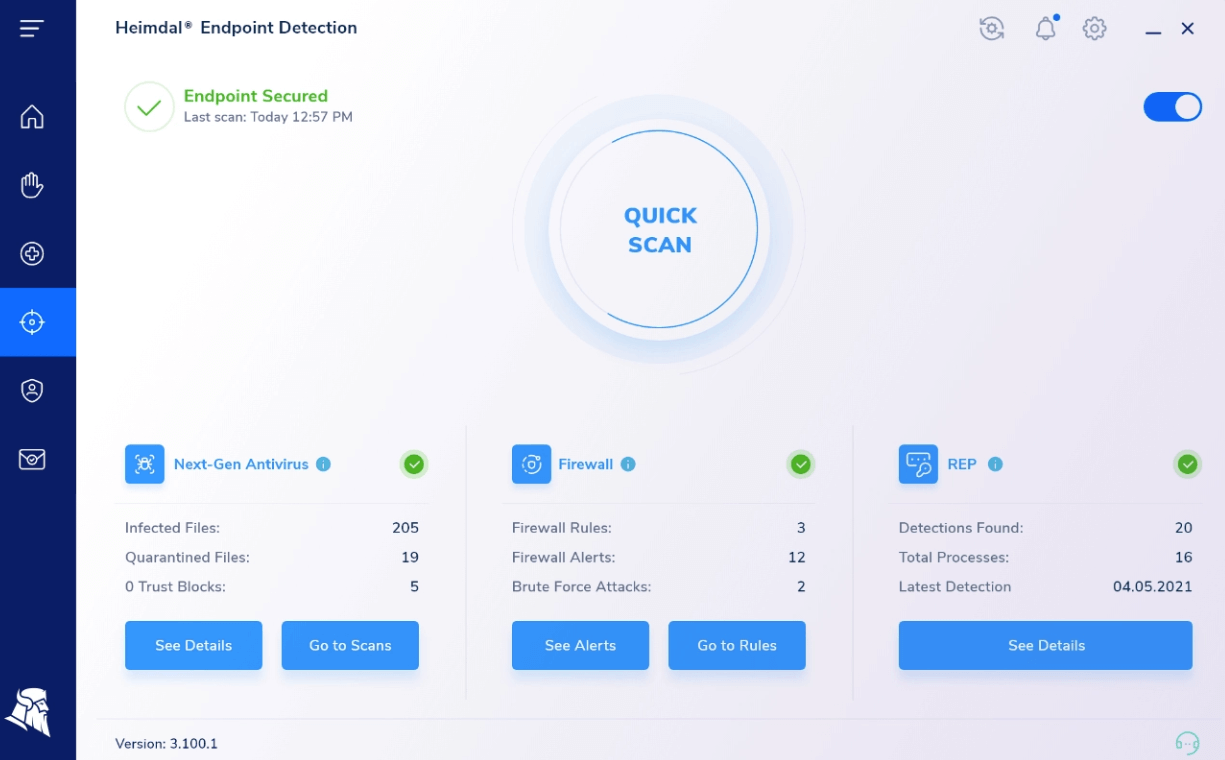
Next-Gen Antivirus (NGAV)
Next-Gen Antivirus section allows you to run a scan or to stop a scan operation (if allowed in the Group Policy settings), and it also displays information about the detected infections and the quarantined files.
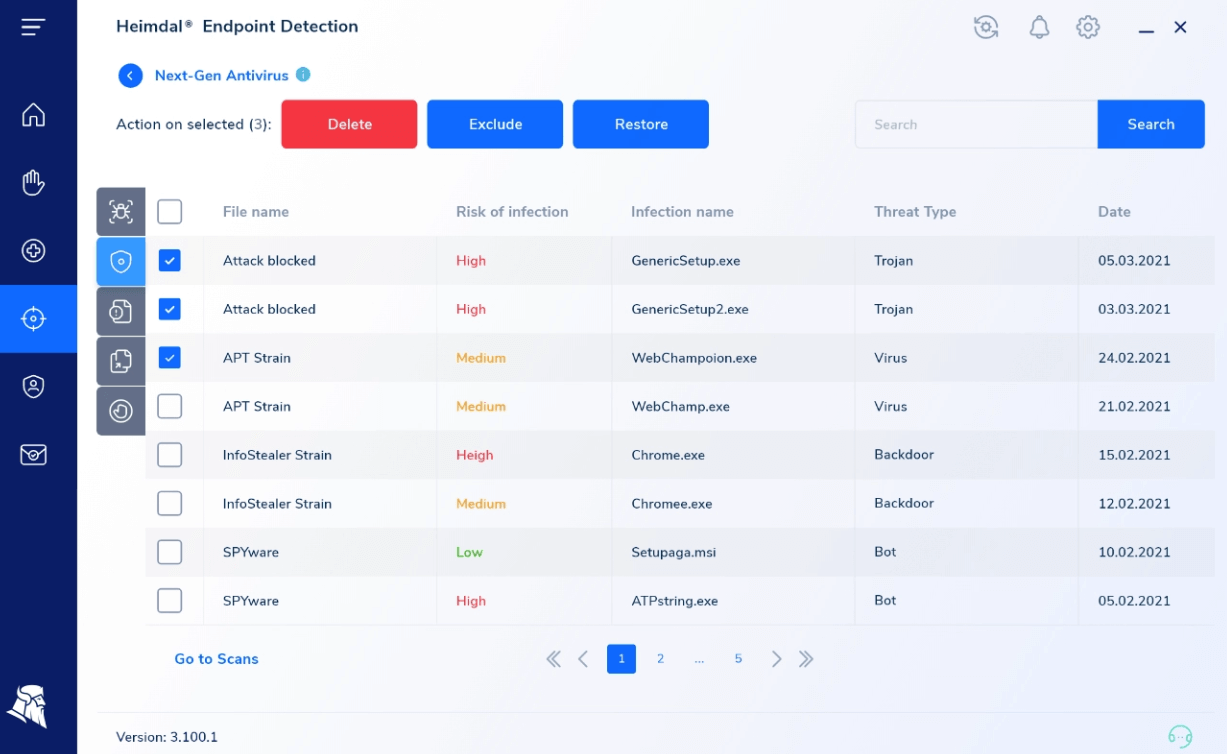
Pressing the See Details button takes you to five other subsections in which among other stats, you will find the following details: File Name, Risk of Infection, Infection Name, Threat Type, and Date. You can also Delete, Exclude, or Restore multiple files at once.
Firewall
This section offers XDR alerts regarding recorded network activities, such as incoming or outgoing data transfers, potential attacks, or various types of requests. Continue reading to discover how to effectively manage this category of XDR alerts utilizing our fully integrated platform.
Ransomware Encryption Protection (REP)
This feature plays a crucial role in identifying and preventing any recognized ransomware from locking up your data in a way that makes recovery impossible.
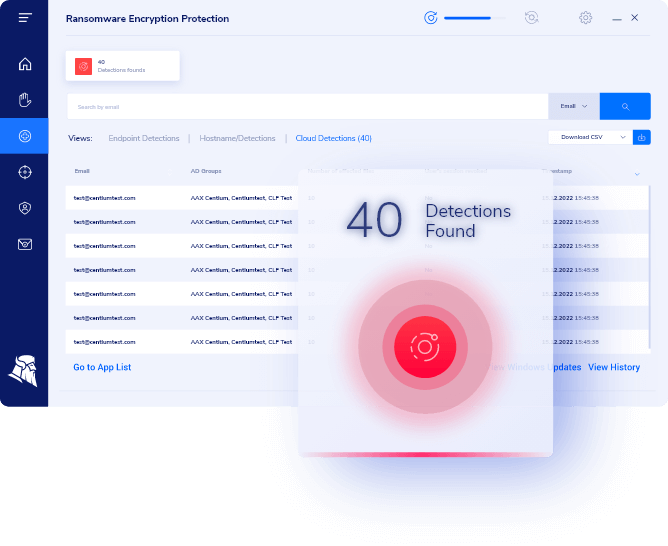 Ransomware Encryption Protection view allows you to review incident details such as timestamps, diagrams with process callbacks, PowerShell scripts, assess read or write operations performed during encryption attempts, command-line arguments, malicious process signatures, and many more.
Ransomware Encryption Protection view allows you to review incident details such as timestamps, diagrams with process callbacks, PowerShell scripts, assess read or write operations performed during encryption attempts, command-line arguments, malicious process signatures, and many more.
Heimdal Agent effortlessly transmits its findings to the Heimdal Dashboard. By exploring the next reading, you will learn the best methods for effectively managing XDR alerts with our unrivaled 10-in-1 suite, that raises the standard for cybersecurity.
Heimdal XDR Dashboard
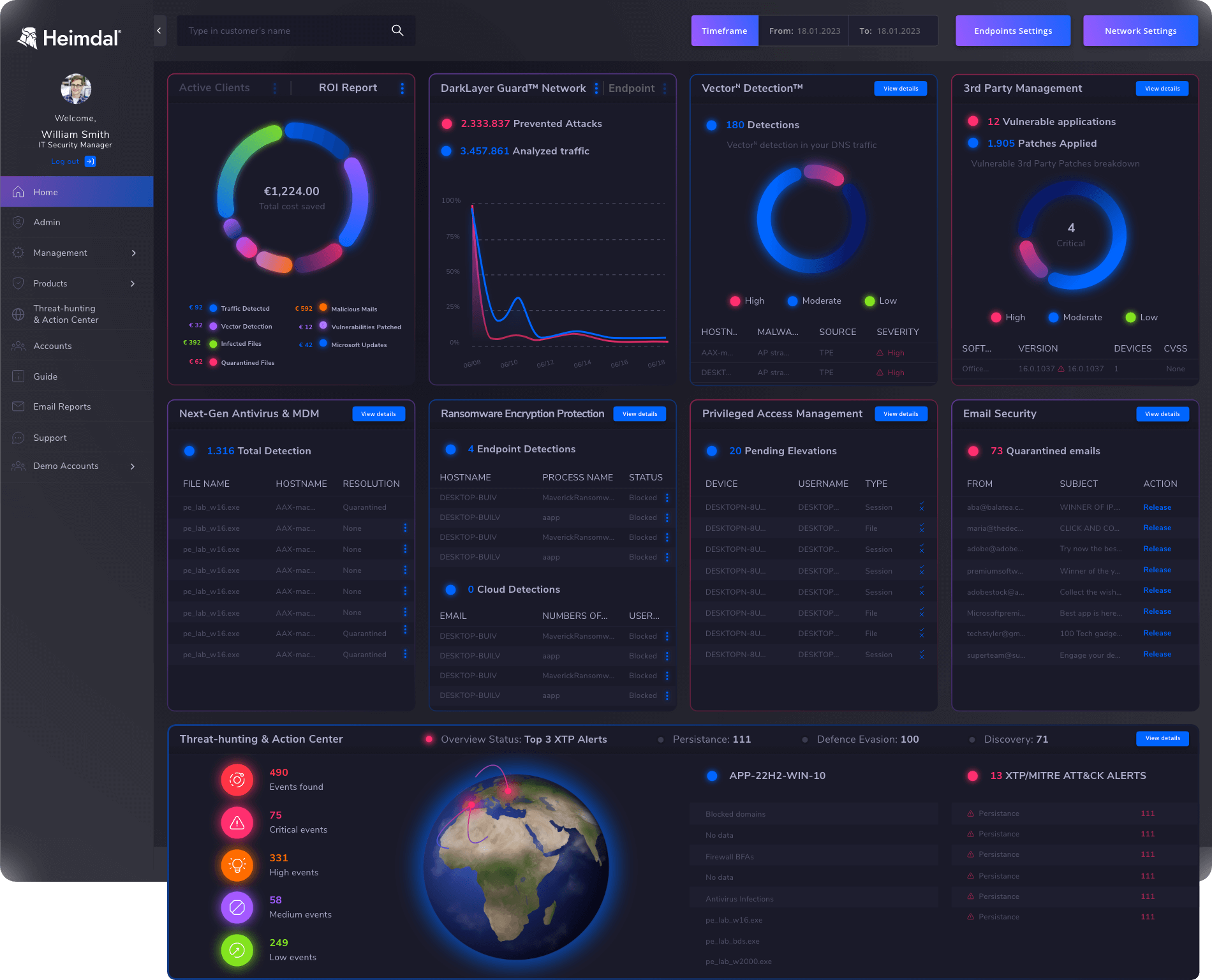
With the Heimdal Consolidated Platform, you can easily see the data gathered from your setup and identify the threats that have been caught in your environment, enabling you to mitigate and act against them.
Threat Prevention – Network
This section displays all the information collected by the Heimdal XDR Agent/ Heimdal Log Agent that is running on the DNS Server(s) in your organization.

On the top, you see a statistic regarding the number of Analyzed Traffic Requests, Prevented Attacks, Prevented Attacks %, and the number of Category Blocks
We placed the above-mentioned data in the following views:
Standard
Displays the following details: Hostname, IP Address, Approved Requests, Prevented attacks, and Risk Level (Low, Medium, or High.)
Threat Type
Contains the following details: Threat Type and number of Hits.
Latest Threats
Shows a table with the following details: Hostname, IP Address, Domain, Threat Type, Date, and Time. You can filter the data using the Latest Threats and Forensics options.
Category Blocks
Displays the following details: Hostname Domain, and Date
Most Used Domains
Displays a table with the following details: Domain and Total Hits. The data in this section is updated every hour.
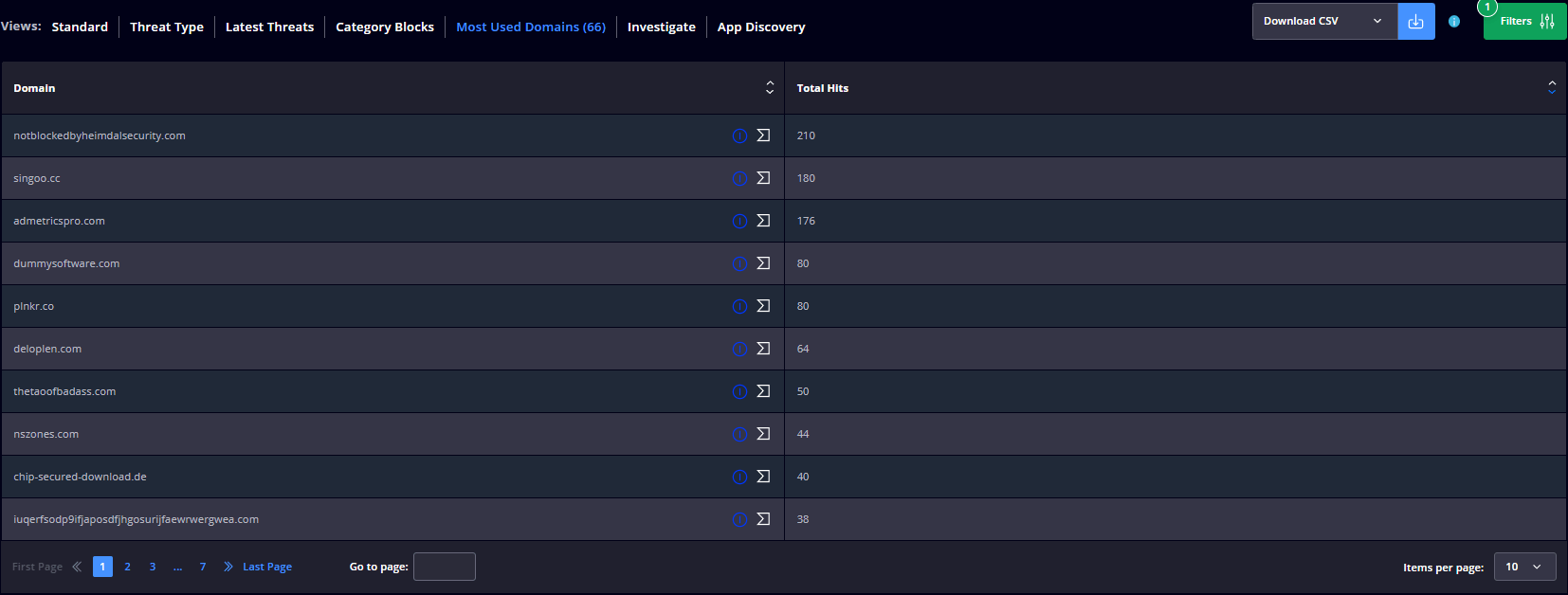
You can easily manage your Network XDR alerts by:
- Turning ON/OFF the intercepted logs, allowing or blocking a domain/sub-domain for the users in your network;
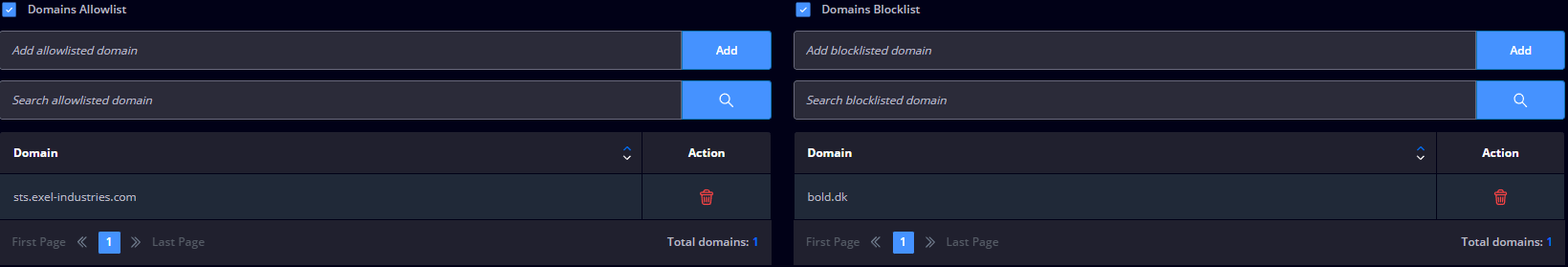
- Blocking groups of domains that you can include in a category (for example Social, Sports, Gambling, Finance, Health, and others);
- Adding a custom HTML block page that will replace the default Heimdal block page when Threat Prevention – Network intercepts and blocks access to a malicious domain (or blocklisted domain);
- Adding your Public IP Address(es) to filter traffic through our DNS Servers, and much more.
Threat Prevention – Endpoint
The collected information covers the DNS queries that the Heimdal Agent’s DarkLayer Guard engine filters, as described at the beginning of this article.
On the top, you see a statistic regarding the number of Analyzed Traffic Requests, the number of Prevented Attacks, the percentage of Prevented Attacks, and the number of Category Blocks.

We place the collected information in the following views:
Standard
This shows the following details: Hostname, Username, IP Address, Analyzed Requests, Prevented Attacks, and Risk Level.
Threat Type
Displays the following details: Threat Type, Number of matches, Most Targeted Hostname, and Username.
Hostname/Threats
Contains the following details: Hostname, Username, Domain Blocked, Threat Type, and Number of matches.
Latest Threats
Presents a table with the following details: Hostname, Username, Threat Type, Threat Type, Threat Source, TTPC, and Date.
TTPC
Displays the following details: TTPC Detections, Number of matches, Most Targeted Hostname, Username, Most Frequently Detected Infected Domain, and Last Match.
Category Blocks
Shows the following details: Hostname, Username, IP Address, and Category Blocked Domains.
Full Logging
The Hostname section contains a table with the following details:
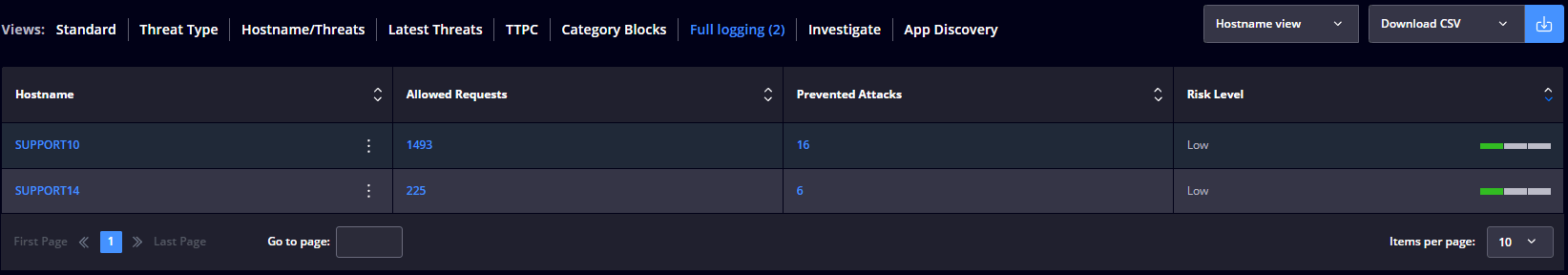
You can effortlessly handle XDR alerts within the Endpoint view through the following features:
- Full logging – Enriched information on the DNS requests made from the endpoints is available (we log all the DNS requests made in your environment).;
- Domains allowlist – You can permit allowing a domain that Heimdal Threat Prevention has blocked through the domains allowlist. Domains, subdomains, top-level domains (.com, .co.uk, etc.), or even multiple domains can be allowlisted at once by uploading a CSV file;
- Block by Category – This enables the blocking of groups of domains that fall within a category (e.g., Social, Sports, Gambling, Finance, Health, and others).
Threat Prevention – VectorN Detection view
The collected information refers to the patterns identified within the DarkLayer Guard domain blocks.

On the top, you see a statistic regarding the number of VectorN Detections.
The collected information is placed in the following views:
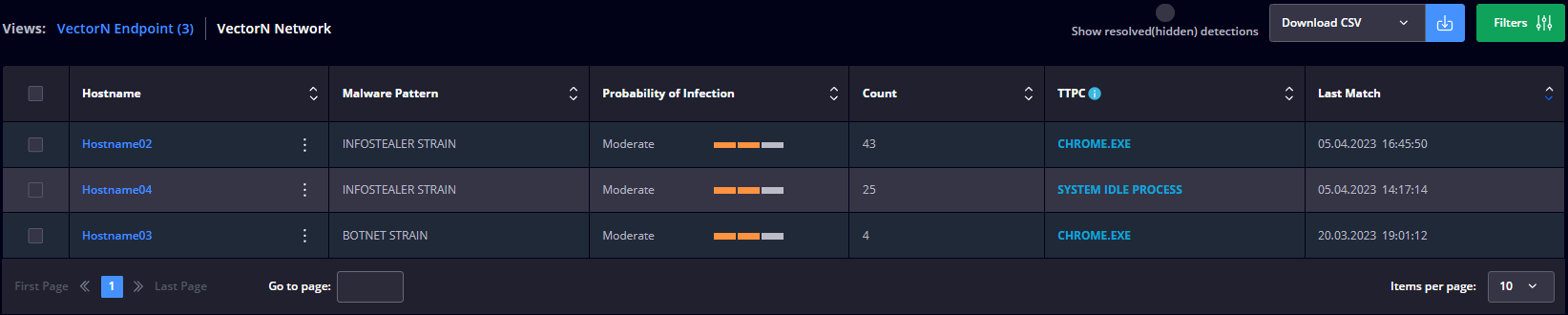
VectorN Endpoint view
This module presents a table with the following details:
VectorN Network view
This section contains the following details:
The following features make it simple to manage XDR alerts inside the VectorN Detection view:
- Block by category – Exercise control over clusters of domains grouped under specific categories such as Social, Sports, Gambling, Finance, Health, and more, effectively blocking entire categories in one go.
- Domains allowlist – Grant permission for domains that were initially blocked by Heimdal Threat Prevention. This versatile feature lets you allowlist domains, subdomains, top-level domains (like .com, .co.uk, etc.), and even multiple domains simultaneously by importing a CSV file.
Endpoint Detection – Next-Gen Antivirus & MDM
The Next-Gen Antivirus & MDM module presents a comprehensive overview of data gathered by the Heimdal XDR Agent on the devices within your organization.
The collected information is placed in the following views:
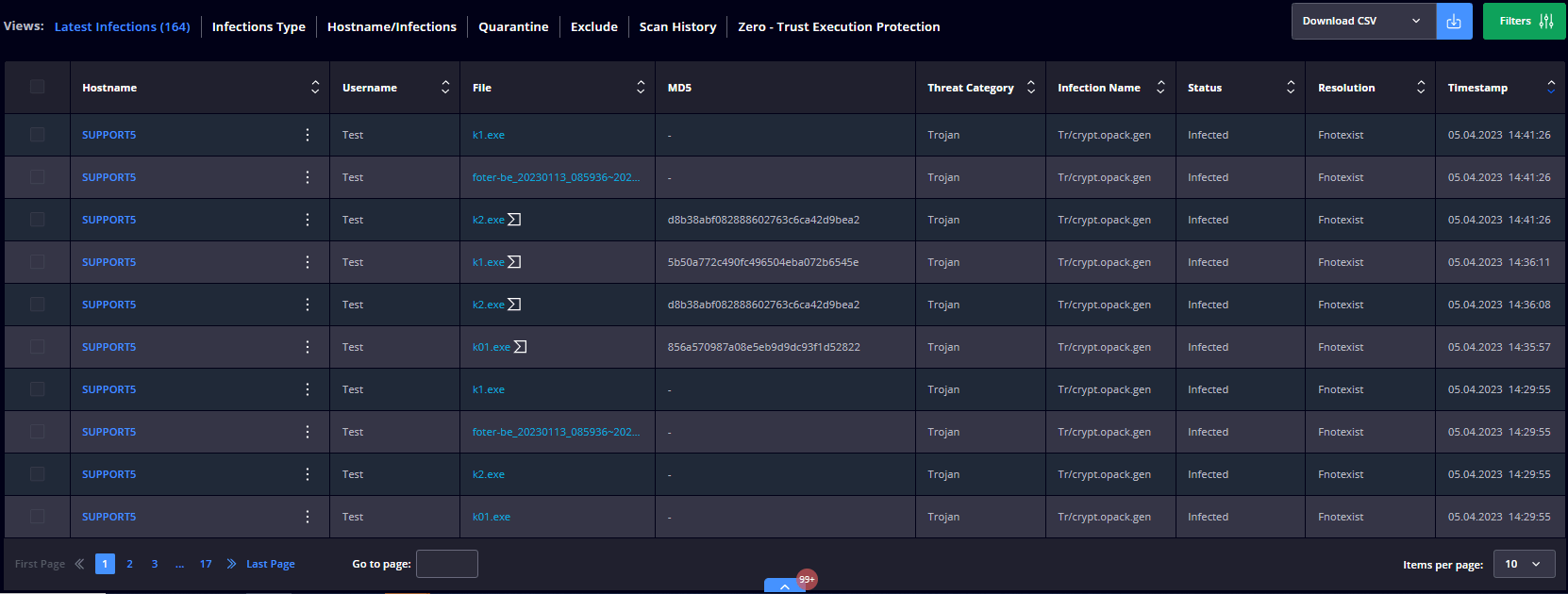
Latest Infections
Allows you to select one or multiple infected files and add them to quarantine, delete, or add to storage.
Infections Type
Displays a table with the infection type and the following details: Threat Category, Number of Matches, Most Targeted Hostname, Username, and Last match.
Hostname/Infections
Contains a table with the hostname/infections and the following details: Hostname, Username, Highest Threat Category, Number of Matches, and Last match.
Quarantine
Presents all quarantined files and the following details: Hostname, Username, File, MD5, Threat Category, Infection Name, Status, Resolution, and Timestamp. This view allows you to select one or multiple quarantined files and Remove them from quarantine or Add them to storage.
Exclude
Shows a table of all exclusions and the following details: Hostname, Username, File, MD5, Threat Category, Infection Name, Status, Resolution, and Timestamp.
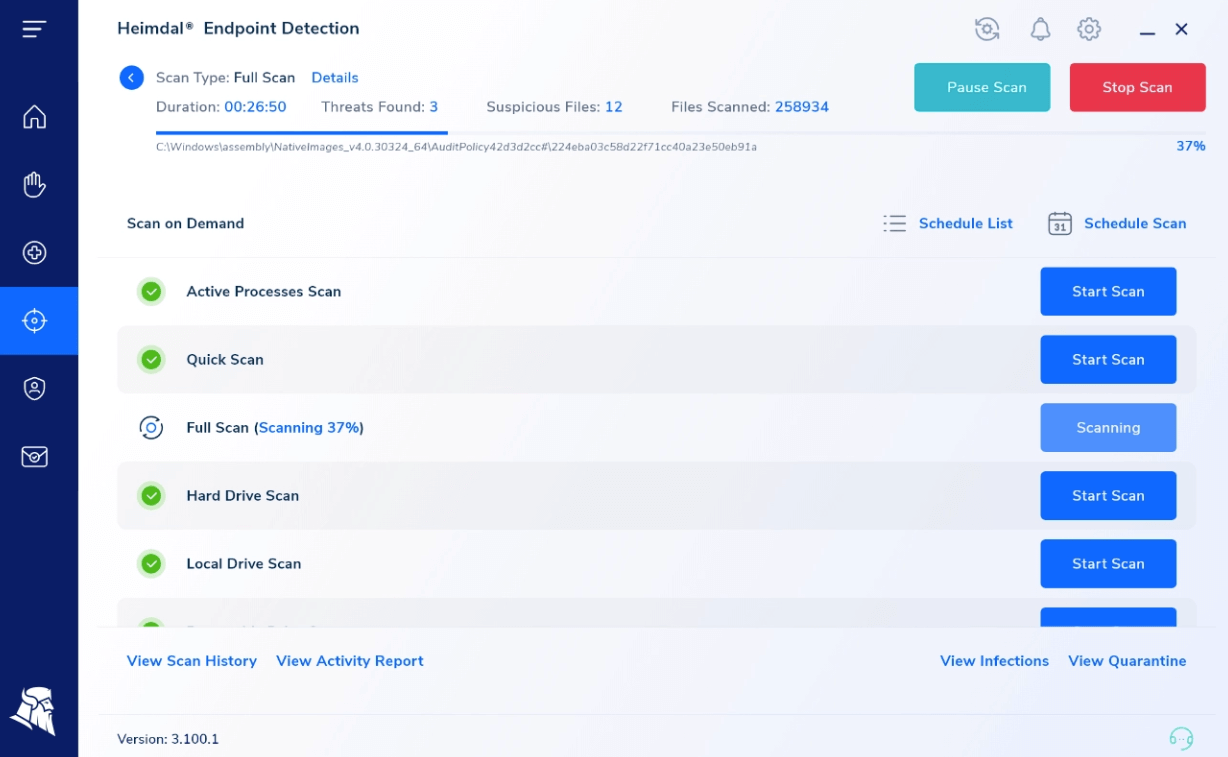
Scan History
Contains details about the computers that were performing scan operations and the following details: Hostname, Username, Group Policy, Timestamp, New Infections Found, and Resolution. This view allows you to select one or multiple endpoints and select a scan type (Quick Scan, Full Scan, Active Processes Scan, Hard Drive Scan, Local Drive Scan, Removable Drive Scan, System Scan, Network Drive Scan).
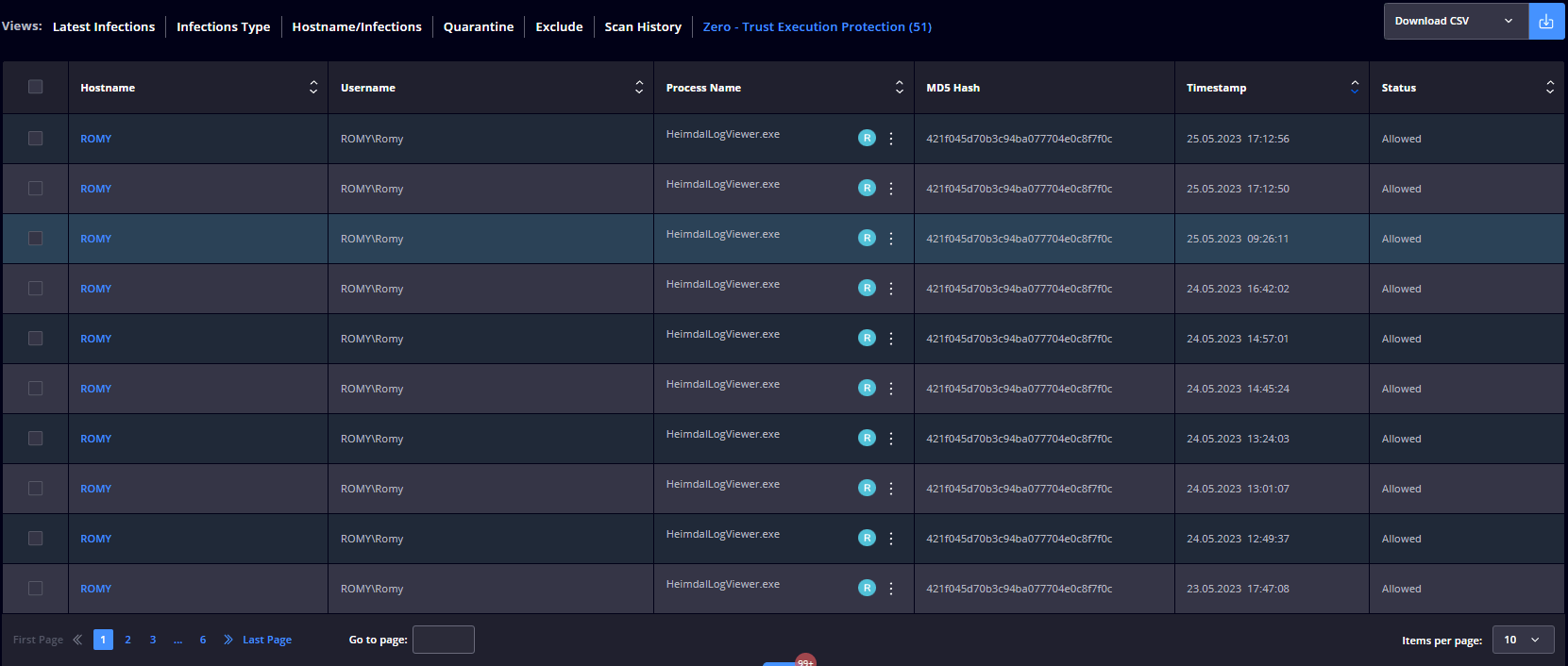
Zero – Trust Execution Protection
Presents a table with the processes (non-signed executable files) intercepted by the Zero-Trust Execution Protection engine and the following details Hostname, Username, Process Name, MD5 Hash, Timestamp, and Status.
You can easily handle Next-Gen Antivirus XDR alerts through the following features:
- Isolate on Tamper Detection – Allows you to isolate a computer from the Internet if the Heimdal Security services are tampered with;
- Disable USB Ports – allows you to disable Removable Media Devices from being connected to a computer;
- Zero – Trust Execution Protection – checks the unsigned executable files and blocks their execution if deemed untrusted. You can also choose the reporting mode only, meaning that Zero-Trust Execution Protection will only scan and report the processes, without taking any action (allow or block). Also, selecting a file from the list allows you to add it to the exclusion list or upload it to the storage.
- Global Quarantine List – allows you to add a file to quarantine if it is detected by the Antivirus engine (the file will be marked as Suspicious or Infected). Based on the detection, you can also choose to delete, exclude, or remove a file from quarantine.
Endpoint Detection Extended Threat Protection (XTP)
The Extended Threat Protection (XTP) engine provides solid evidence-based insights into complex cybersecurity risks and offers a comprehensive perspective of vulnerabilities, neatly organized based on MITRE ATT&CK tactics and techniques. This cutting-edge engine relies on information from over 1400 Sigma rules. The collected information is placed in the following views:
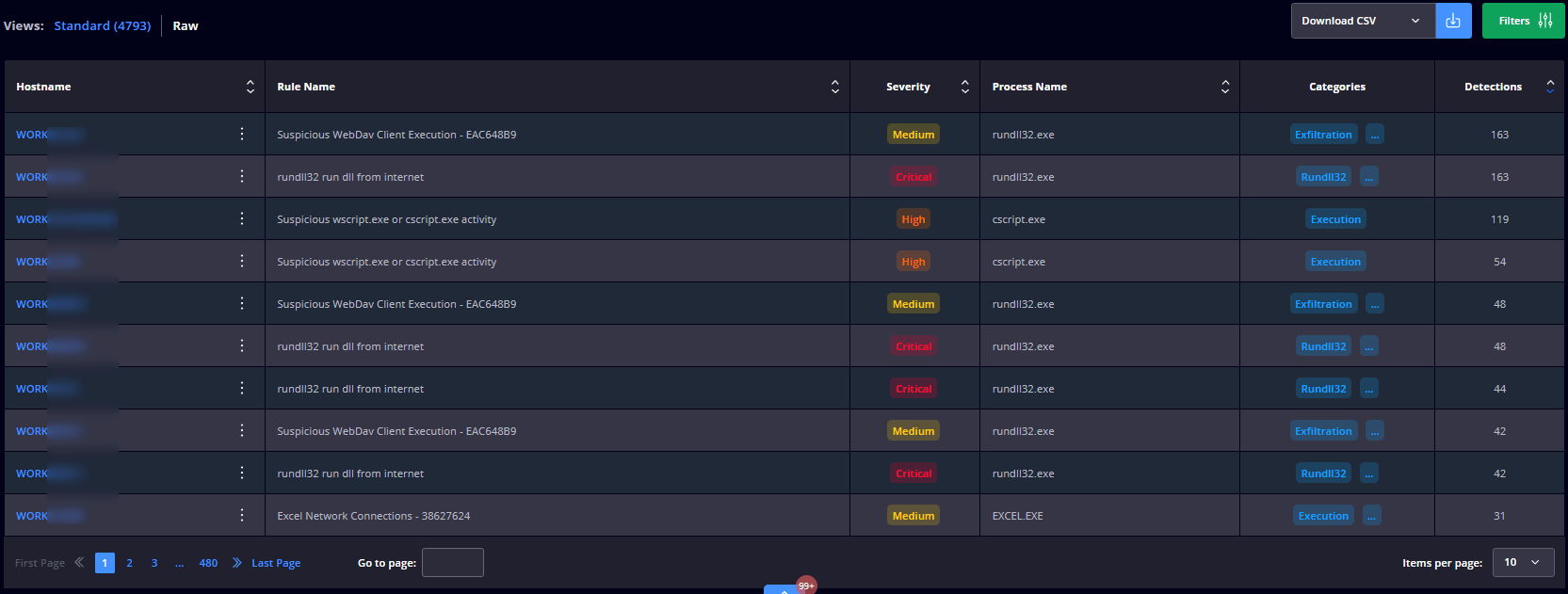
Standard
This section displays a table with the following details:
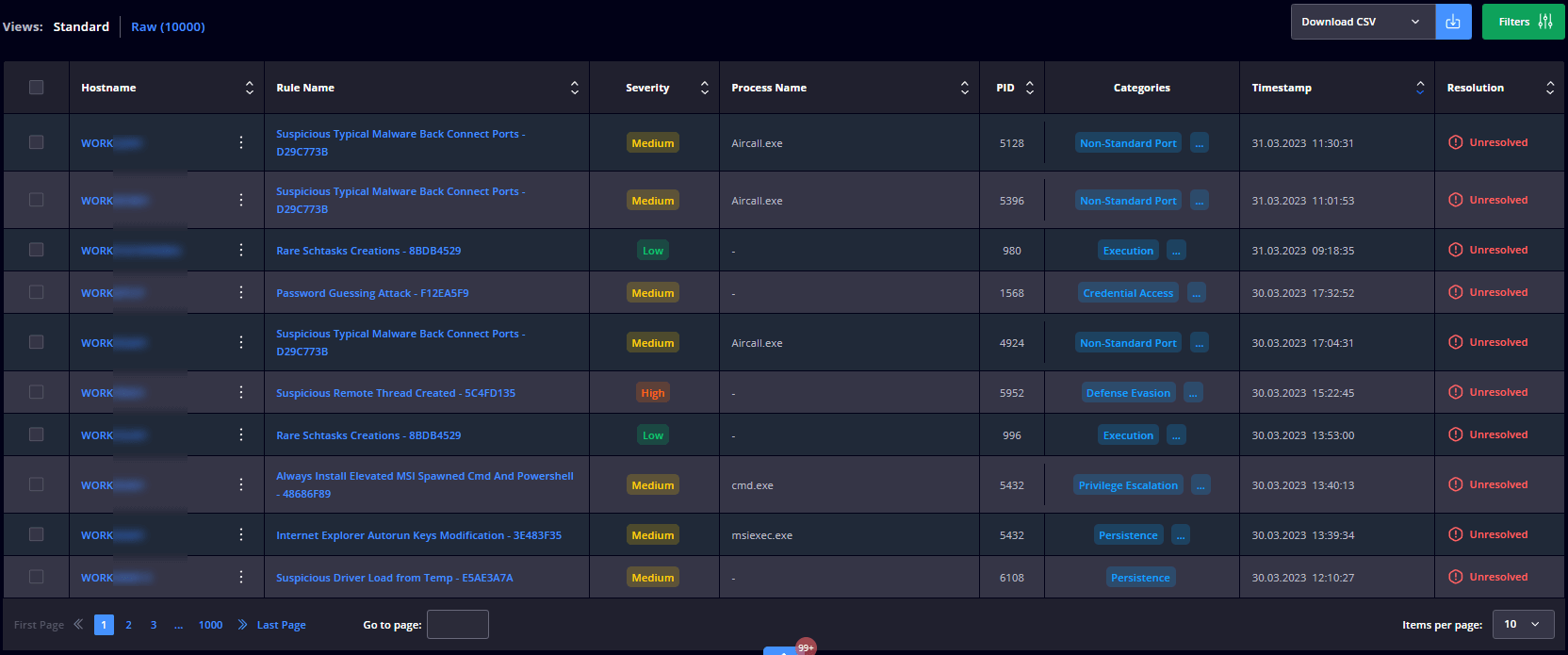
Raw
This module contains the following details:
Next-Gen Antivirus with XTP
The addition of the XTP engine will supercharge the current Next-Gen Antivirus with Extended Threat Protection (XTP) capabilities, thus supplying you with evidence-based information about sophisticated cybersecurity risks, offering a holistic view of weaknesses, categorized on MITRE ATT&CK tactics and techniques and, ultimately, providing boundless levels of state-of-the-art protection.
Extended Threat Protection (XTP) stores information based on the system’s audit policies. These events are analyzed by the XTP engine, which can tell when a suspicious event occurred.
- Signature-based detection
Signature-based detection compares files coming into devices to known malware, looking for signature matches;
- Heuristic-based detection
Heuristic-based detection is similar to signature-based detection, however, while signature detection looks for exact matches, heuristic detection looks for similar tendencies or patterns in a file’s code;
- Behavior-based detection:
This form of detection examines how files and programs act, looking for anything out of the ordinary.
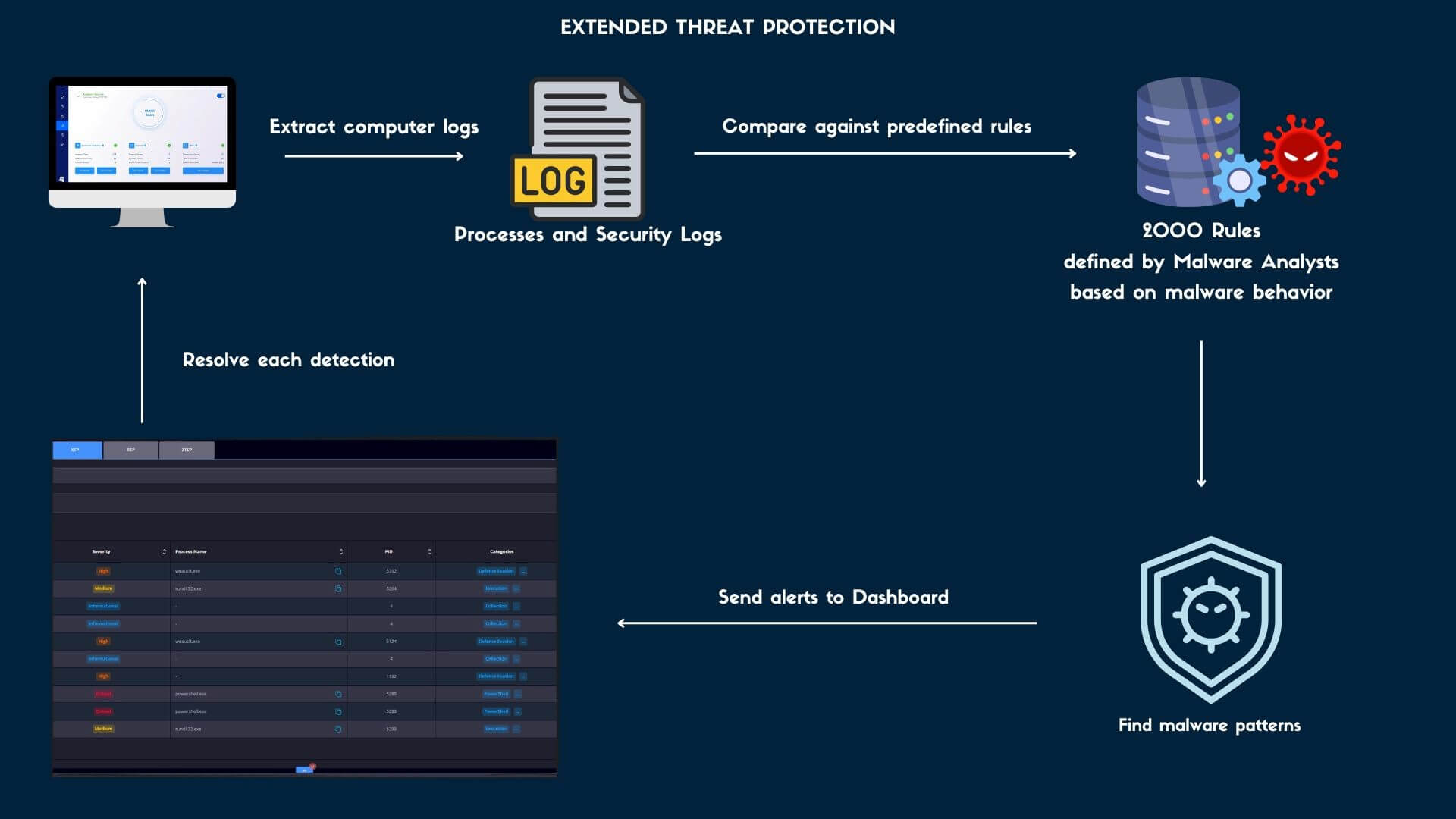
Whether attackers use exploits defense evasion, credential access, or exfiltration, the XTP engine has your back. It gives you an in-depth breakdown of the attack process, how the attack works, and the tactics employed.
You can easily manage XTP alerts through the following features:
- Exclusions – Allows you to exclude a process by filename, file path, directory path, or MD5 by matching it with a rule found in the XTP engine.
- Rules – You can manually disable any of the rules listed under the XTP engine by unticking the Enabled tick box.
- Raw view – The checkbox allows you to select an entry and Resolve or Unresolve the event.
Endpoint Detection – Firewall Alerts
This module displays the following details:
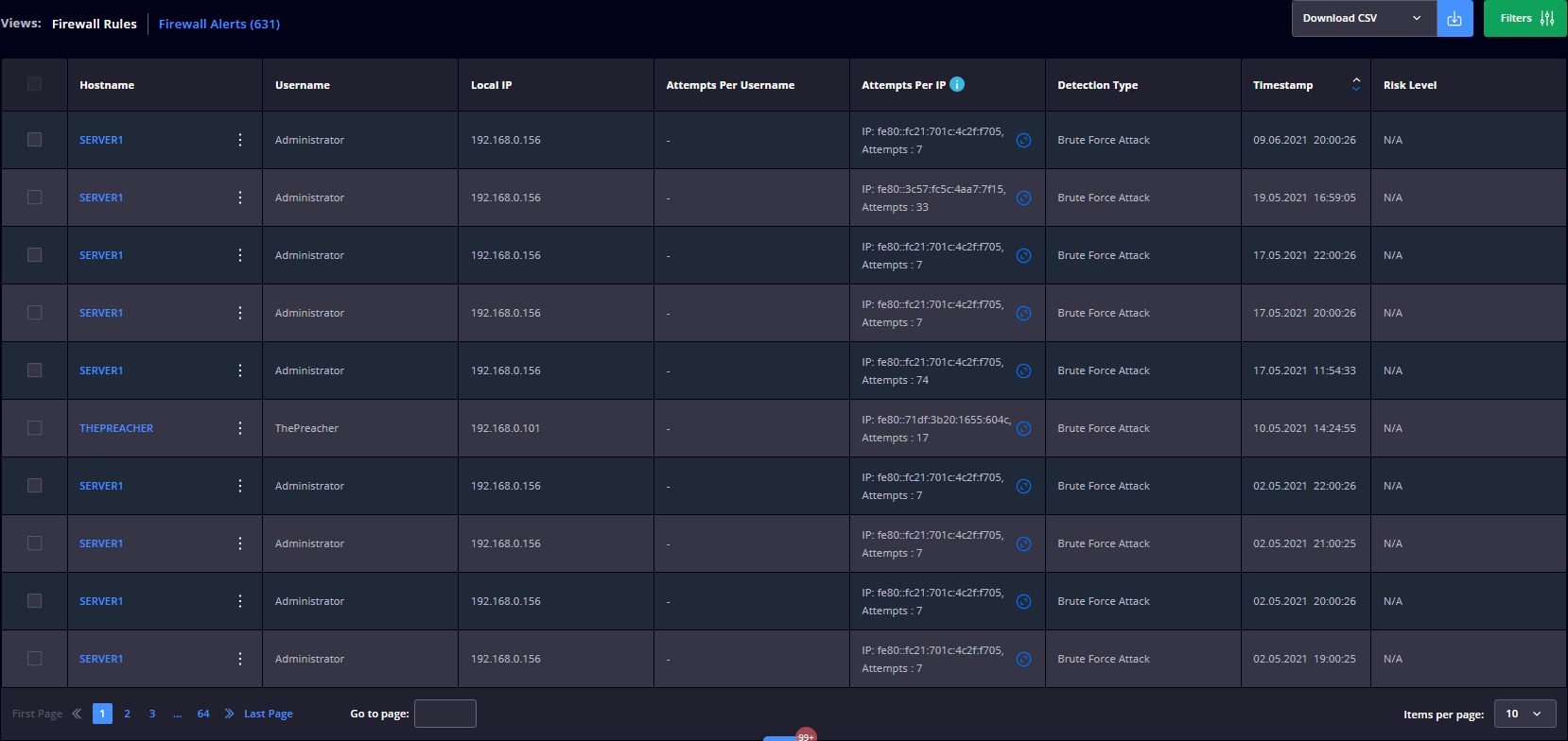
The entries that you see in this view include a list of all the unwanted connections that are interpreted as Brute Force Attacks.
You can effortlessly handle brute force attacks by:
- Adding the IP Address to the Brute Force Attack Allowlist.
- Blocking RDP port on brute force detection – automatically blocks the default RDP Port (3389) on the endpoint where an audit breach is detected for both TCP and UDP.
- Changing the default RDP Port (3389) to another port number
- Using automatic rules – allows you to select any of the profiles to enable/disable the Inbound/Outbound connections;
- Allowing isolation -allows you to isolate an endpoint in your network from the rest of the endpoints.
Endpoint Detection – Ransomware Encryption Protection (REP)
This module displays all the information referring to the detected processes intercepted by the Heimdal Agent that is running on the endpoints in your organization.
The Ransomware Encryption Protection module detects processes that perform encryption operations on files on the endpoint with malicious intent. The module is processing kernel events for IO reads, writes, directory enumeration, and file execution.
The collected information is placed in the following views:
Latest Detections
Displays a table with the following details:
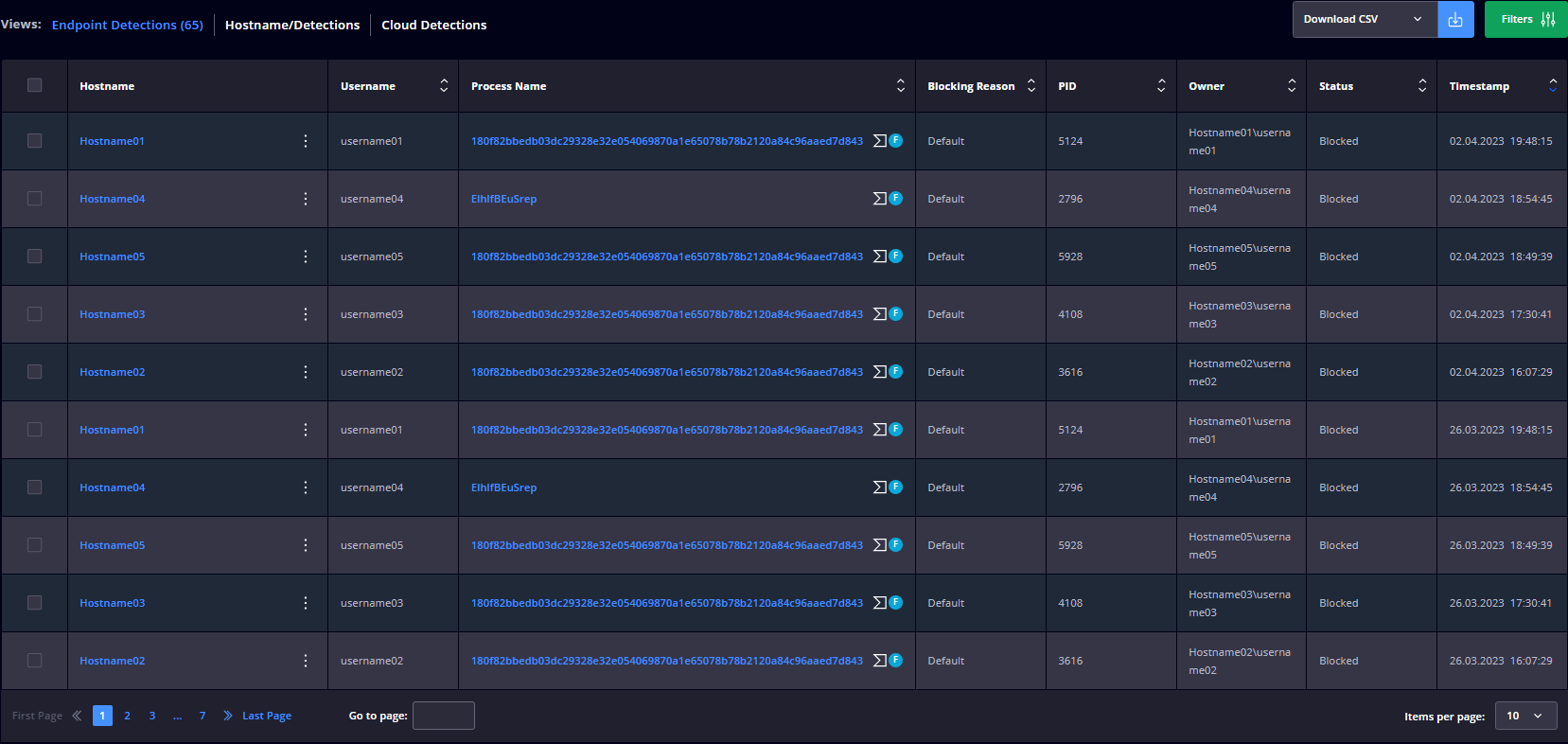
Hostname/Detections
Displays a table with the following details:
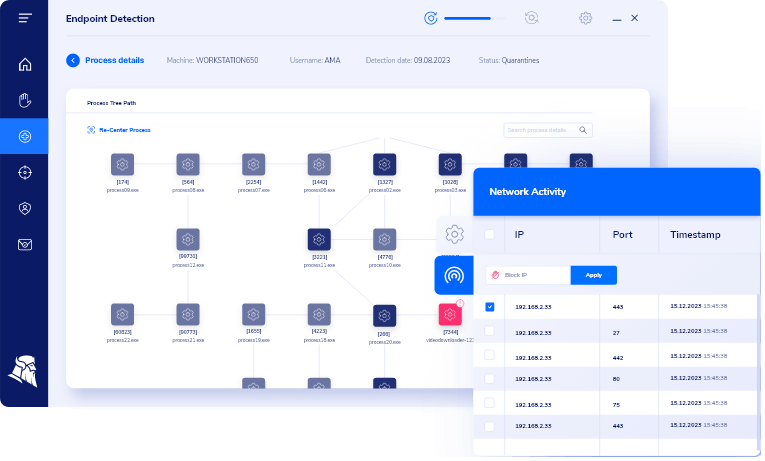
The Process Details gives you information on the parent process and the spawned processes, their PIDs, username, File Name, Path, Command-Line, Thread Count, top 3 encrypted files, Write Operations, Read Operations, MD5, Signature, and Owner.
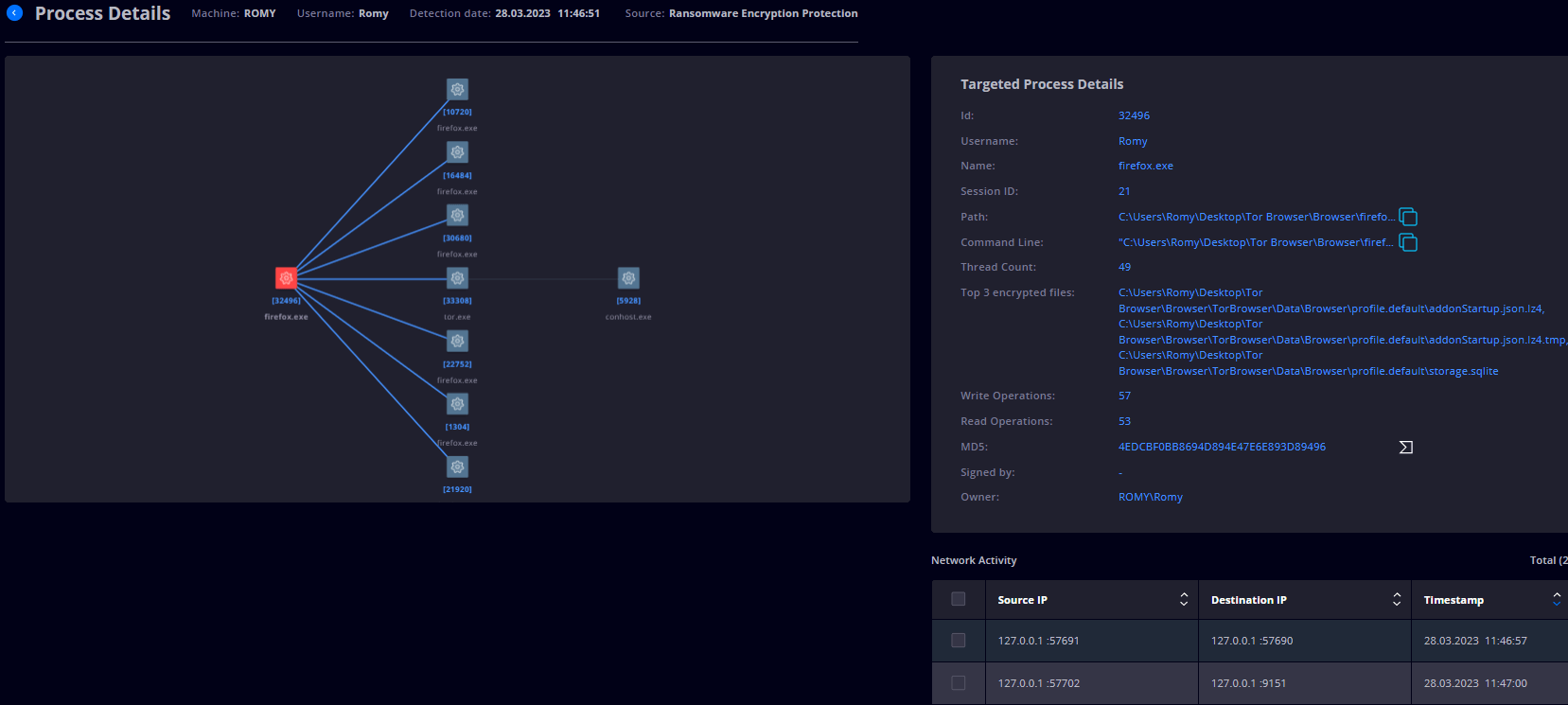
Managing REP XDR alerts requires a comprehensive approach. That’s why, in this section, you will find vital details and action steps that you can take in order to minimize the impact on your environment.
How to manage Ransomware Encryption Protection XDR alerts like a Pro with Heimdal:
- The REP view allows you to select one or multiple infected files and exclude it/them or add it/them to storage for a further in-depth investigation;
- In the Process Name column, you can click on the process (or on the Forensics ‘F’ icon) to see the process details or you can click on the VirusTotal icon to get a detailed VirusTotal analysis.
- Get information on the Network Activity of the detected process, where you can select one or multiple IP Addresses to block them in the Firewall (on one, multiple, or all Group Policies).
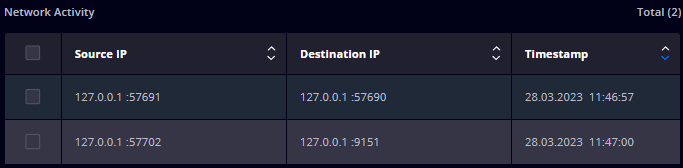
- Make exclusions by selecting one or more detections and by pressing the Exclude and Apply buttons from the dropdown menu.
- Isolate on Tamper Detection – allows you to turn ON/OFF the isolation feature when a Tamper Detection is being made.
Conclusion
By following the insights and strategies outlined in this comprehensive user guide, you’re equipped to navigate the dynamic world of threat detection and response. From gaining full visibility into network activities to pinpointing the root causes of XDR alerts, the Heimdal XDR solution empowers you to proactively protect your systems, devices, and sensitive data.


- End-to-end consolidated cybersecurity;
- Complete visibility across your entire IT infrastructure;
- Faster and more accurate threat detection and response;
- Efficient one-click automated and assisted actioning


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security












