Contents:
A new ransomware strain called Somnia has affected multiple Ukrainian organizations lately, encrypting their systems and causing operational problems.
The Computer Emergency Response Team of Ukraine aka CERT-UA has recently confirmed the outbreak with an announcement on its website. According to CERT-UA, the threat group “From Russia with Love” (FRwL), also known as the “Z-Team” are responsible for the ransomware attacks. The group disclosed in a previous post on Telegram that they are responsible for creating the ransomware, and even posted proof of conducting attacks against tank producers in Ukraine.
Details on the Attack
According to the statement posted by CERT-UA, FRwL is using fake sites to mimic the “Advanced IP Scanner”, thus tricking Ukrainian organization employees into downloading an installer.
When triggered, the installers would in fact infect the system with the Vidar stealer, which steals the victim’s Telegram session data to take control of their account.
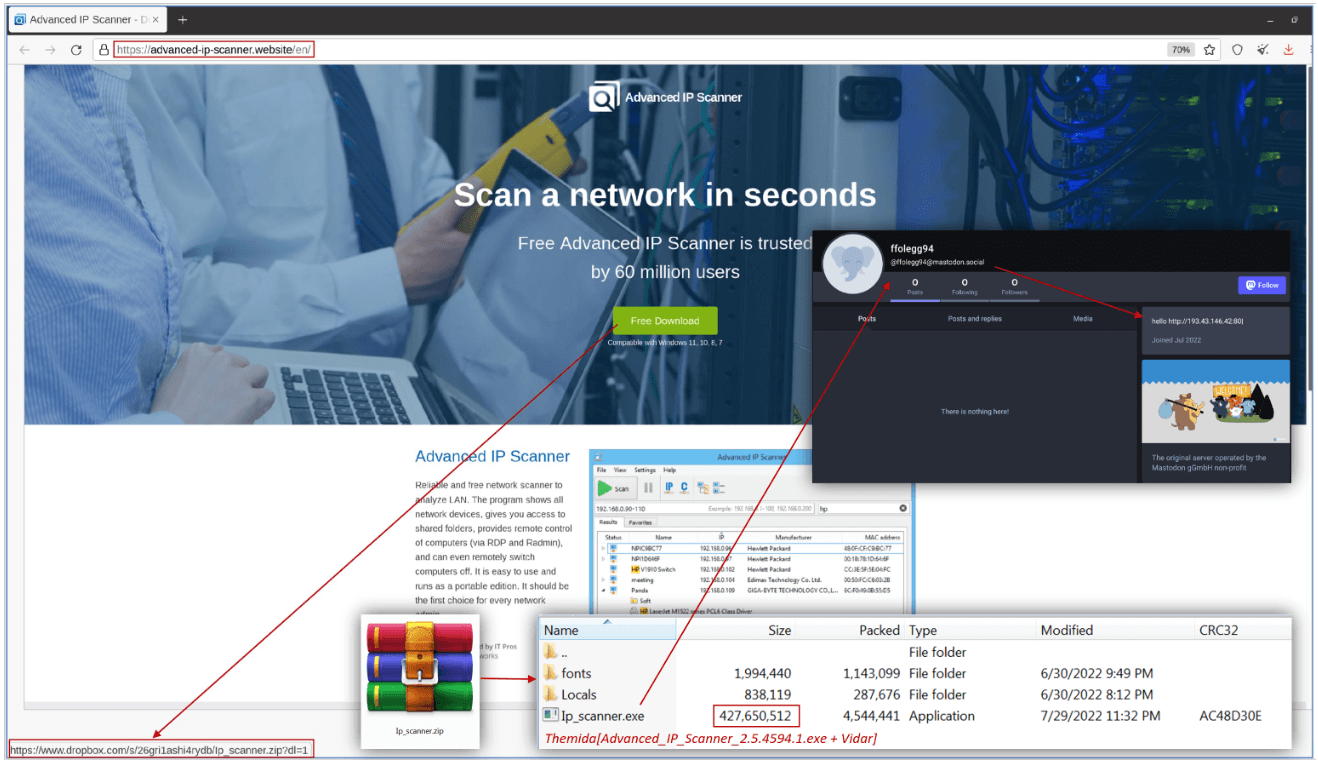
Fake Website Used by FRwL (Source: CERT-UA)
After gaining access to the victim’s Telegram account, the threat actors would abuse the account to steal VPN connection data (authentication and certificates). If unprotected, the threat actors would use the VPN account to gain unauthorized access to the corporate network of the victim’s employer.
The attackers then set up a Cobalt Strike beacon, steal information, and carry out various remote access and surveillance tasks using Netscan, Rclone, Anydesk, and Ngrok. CERT-UA reports that the attacks started in the spring of 2022.
The agency also notes that while Somnia initially used the symmetric 3DES algorithm, the most recent samples of the ransomware strain used in these attacks rely on the AES algorithm.
According to BleepingComputer, Somnia targets documents, databases, archives, photos, videos, and more. Somnia’s operators are more concerned with disrupting the target’s operations than making money, so they do not ask the victims to pay a ransom in exchange for a working decryptor, making the malware a data wiper rather than a traditional ransomware attack.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










