Contents:
POS malware is still a threat exploited by cybercriminals, even if the card payment industry has been working on implementing security measures. It has been recently discovered that two point-of-sale (PoS) malware variants have been used by an unknown threat actor to steal information related to more than 167,000 credit cards from payment terminals.
In their report, researchers from the Singapore-based cybersecurity company Group-IB, estimate the stolen data could amount to as much as $3.34 million if sold on underground forums.
Point-of-sale (POS) malware is basically designed to infect POS terminals with the clear purpose of stealing payment data stored bank cards.
TreasureHunter and MajikPOS are both malware responsible for brute-force attacks targeting PoS terminals, followed by extracting payment card information from the system’s memory, and forwarding it to a remote server.
It has been reported that the cybersecurity researchers identified the command-and-control (C2) servers associated with the two PoS malware and further concluded that 77,428 and 90,024 unique payment records were compromised by MajikPOS and Treasure Hunter respectively, between February and September 2022, with most of the stolen cards having been issued by banks in the U.S., Puerto Rico, Peru, Panama, the U.K., Canada, France, Poland, Norway, and Costa Rica.
MajikPOS
Ever since its discovery in 2017, the MajikPOS malware has enabled its operators to use a combination of PoS malware and remote access trojan (RAT) to attack their targets, mainly represented by businesses across the U.S. and Canada.
The typical kill chain of an attack involving this type of malware begins from scanning for open and poorly secured VNC (Virtual Network Computing) and RDP (Remote Desktop Protocol) ports. Next, the attackers use brute-force attacks to gain entry into the system.
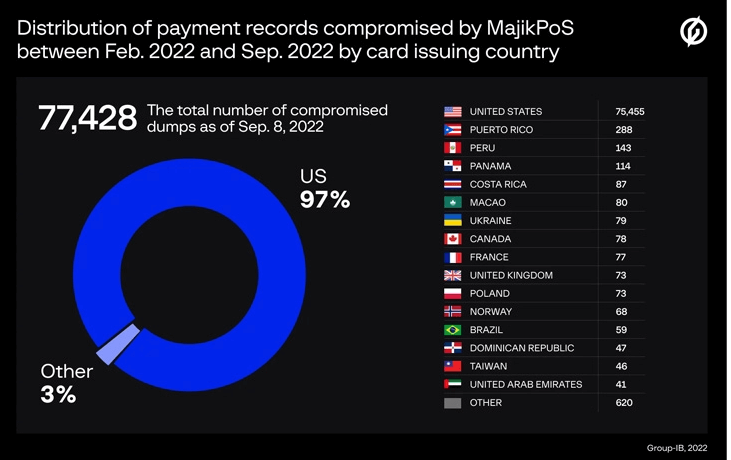
TreasureHunter
A POS malware that was first detected in 2014, its initial kill chain phases are similar to MajikPOS. However, the difference is that after infecting a POS terminal, the malware enumerates the running processes, extracting all available payment card information and forwarding it to a C2.
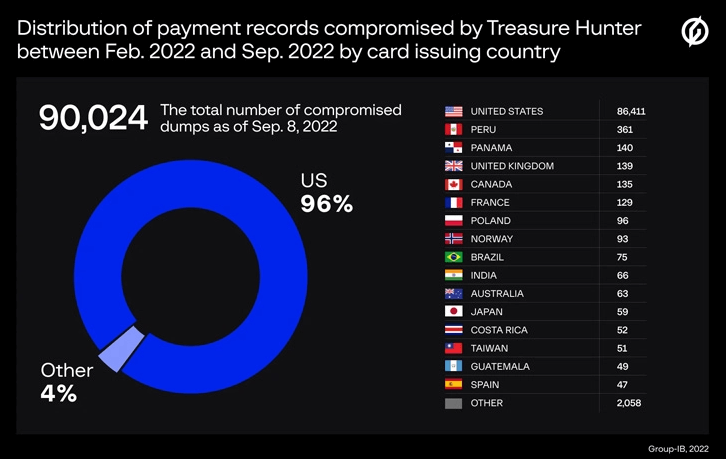
Researchers argue that most POS devices infected with TreasureHunter were compromised in 2021, while in 2022 the threat actors reoriented towards MajikPOS. Nevertheless, the identity of the actors remains unknown, and there are no clear details whether the stolen data has been profited from by the culprits.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security









