Contents:
Free WordPress open source plugin WooCommerce has released a patch fix for a critical vulnerability that was identified on July 13, 2021, through the company’s HackerOne security program. The researchers said the flaw could be exploited without authentication.
The vulnerability known as SQL Injection Vulnerability is so critical that the popular e-commerce plugin for the WordPress content management system is pushing the update automatically to impacted publishers.
The admins are urged as the vulnerability affects more than 90 versions starting with 5.5.0.
Even though the updates are automatic, some publishers are reporting that some of their websites did not receive the update yet.
WooCommerce is an open-source e-commerce plugin for WordPress. It is designed for small to large-sized online merchants using WordPress. Launched on September 27, 2011, the plugin quickly became popular for its simplicity to install and customize and for the market position of the base product as freeware.
The organization discovered that the bug impacted the WooCommerce plugin versions 3.3 to 5.5, as well as versions 2.5 to 5.5 of the WooCommerce Blocks feature plugin, but both plugins received an update to version 5.5.1.
According to BleepingComputer, the bug has yet to receive a tracking number but its severity score has been calculated at 8.2 out of 10 by Patchstack, a company that protects WordPress sites from plugin vulnerabilities.
Oliver Sild, the founder and CEO of Patchstack, observed that the patch removes the vulnerability by modifying two PHP files that enabled introducing malicious code in SQL statements without having to authenticate.
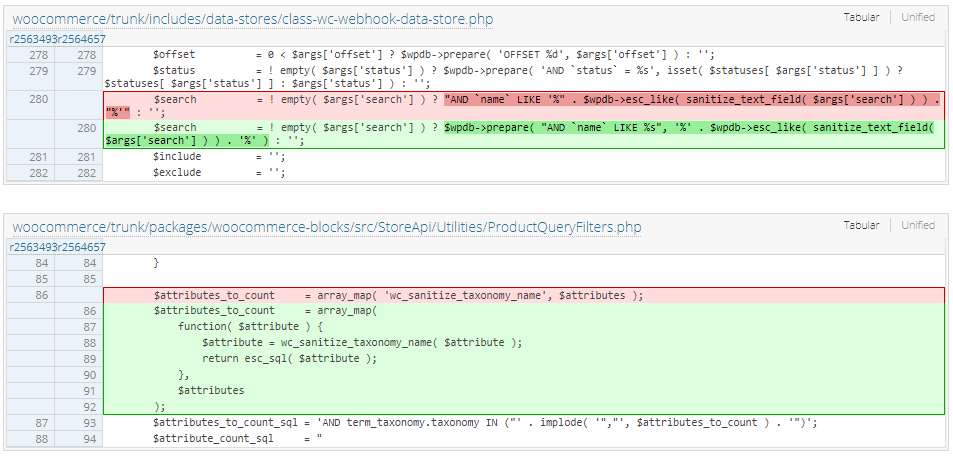
The injection was possible because of a webhook search function that injected the search parameter into a SQL query without using a prepared statement.
According to Sild, despite the use of sanitize_text_field and esc_like functions, the latter could be used without a prepared statement, which no longer happens in version 5.5.1.
The security specialist stated that the absence of authentication happened because of the improper escape of the $attributes parameter in a public-facing endpoint that did not need authentication.
The $attributes parameter in this endpoint (line 86) is taken from the user input and then processed and injected into a SQL query that was not properly escaped.
What Data Was Exposed?
It is not clear yet if the data of those impacted had been compromised, although WooCommerce has declared it will be sharing more details with administrators on how to investigate this particular security flaw on their websites.
At the moment, with the help of the WordPress.org Plugin Team, impacted WooCommerce installations receive the patch automatically.
Websites on the WordPress.com blogging platform have already received the fix.
In an email, WooCommerce notified online store owners that stores hosted on WordPress.com and WordPress VIP had already been secured.
Patchstack has not noticed any attempts to use this flaw in the wild but cybercriminals may jump at the occasion before the fix reaches more sites.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










