Contents:
Cybercriminals conducting phishing attacks now take advantage of Google SMTP relay service to get around email security software and successfully send malicious email messages to their victims.
A report from email security company Avanan shows that there has been a sharp increase in cybercriminals exploiting Google’s SMTP relay service since April 2022. According to the firm, this strategy was used to distribute at least 30,000 emails in the first two weeks of April.
What Is Google SMTP Relay Service?
Google provides an SMTP (Simple Mail Transfer Protocol) relay service that Gmail and Google Workspace users can utilize to send outgoing email messages.
This service is used by organizations everywhere for different reasons, varying from not having to manage an external mail server to using it for marketing emails to avoid having their mail server added to a block list.
How Does The Attack Happen?
According to the email security firm, cybercriminals can spoof other Gmail tenants using Google’s SMTP relay service without being noticed if those domains don’t have a DMARC policy configured with the ‘reject’ directive.
DMARC (the abbreviation of Domain-based Message Authentication and Reporting and Conformance) is an email authentication protocol developed to provide email domain owners with the capability to protect their domain from unauthorized use. This way, they can specify what should happen if an email is spoofing their domain.
A company can establish a specific policy that governs its email authentication guidelines. A DMARC policy tells the receiving mail servers like Gmail, Outlook, and Live how to enforce them if an email fails the DMARC verification.
There are three policies available, denoted by the symbol ‘p= policies’:
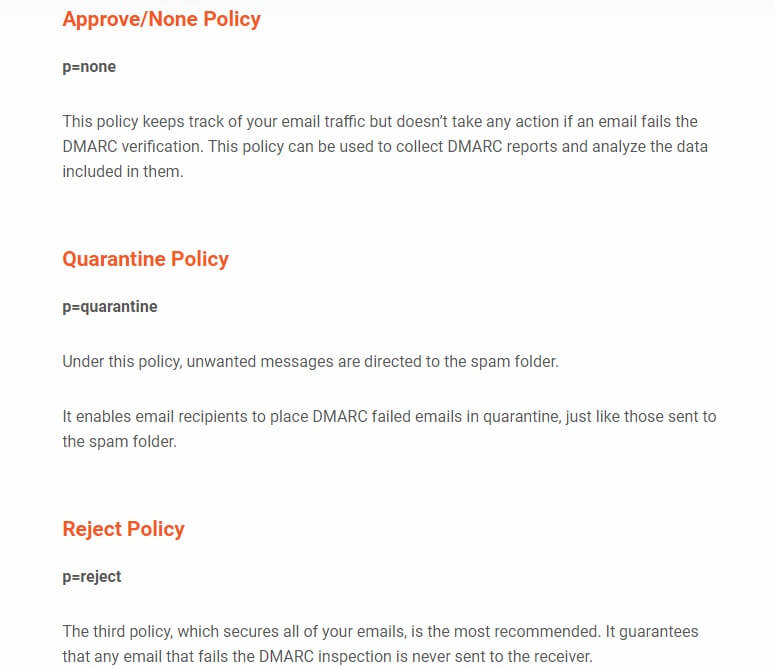
As explained by Bleeping Copmputer, the new phishing operations employ the ‘smtp-relay.gmail.com’ SMTP server, which is a trusted server that is frequently added to allow lists by email gateways and spam filtering solutions.
DMARC Plays a Huge Part
These cyberattacks are effective only if the spoofed organization’s DMARC policy is set to “none,” which isn’t as rare as you might think. DMARC policies are set to ‘none’ on dell.com, wikipedia.org, yandex.ru, pornhub.com, bit.ly, and live.com.
Nowadays, email security risks are multiplying at an alarming rate. Cyberattacks involving spear-phishing, whale phishing, or spoofing, have become a major concern for many businesses. Therefore, the implementation of DMARC is highly essential in such enterprises. Implementing email authentication guidelines within companies protects email domains from domain forgery and other email-based attacks.
Google SMTP Relay Service, Not the Only One that’s Vulnerable
While these cybercriminals are abusing Google’s relay service, Avanan claims that other relay services are also vulnerable to this type of exploitation.
The Gmail team has been notified of the abuse by the email security company on April 23, 2022.
A Google spokesperson has declared for Bleeping Computer:
We have built-in protections to stop this type of attack. This research speaks to why we recommend users across the ecosystem use the Domain-based Message Authentication, Reporting & Conformance (DMARC) protocol. Doing so will defend against this attack method, which is a well-known industry issue.
Details on how users can configure their environments appropriately can be found here: https://support.google.com/a/answer/2956491?hl=en and here: https://support.google.com/a/answer/10583557
There’s nothing unique to Workspace here, it speaks to how email standards operate across the industry. This research doesn’t reflect many of the layered defenses which keep customers safe, such as DMARC and email abuse filtering.
How to Stay Safe?
When it comes to spotting a malicious spoofing endeavor, verifying the sender’s address isn’t enough. Make sure you check the full headers when you’re in doubt.
Also, instead of clicking on links contained in the message body, hover over them to confirm the destination. Malware can be installed on your computer simply by visiting malicious websites.
And, as always, if the message contains attachments that seem suspicious to you, we advise against downloading or opening them.
How Can Heimdal™ Help?
Heimdal Email Security will keep your inboxes clean and lean as it uses an entire array of technologies to detect and block spam, malware, and ransomware threats before they compromise your IT system through malicious emails. The advanced spam and malware filter Heimdal Email Security is also compatible with Heimdal Email Fraud Prevention, a module especially designed to combat the growing threat of Business Email Compromise (BEC) attacks.
With our Email Security module, your business and employees will be spared from:
- The pervasive, evolving threat of phishing.
- Email exploits & botnet attacks.
- Unwanted content.
- The again-growing threat of ransomware.
- The frustration of having to click away through never-ending spam emails.
- Botnet attacks through email.
- Malicious links and attachments.
- Emails coming from infected IPs and/or domains.
- Advanced spam.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










