Contents:
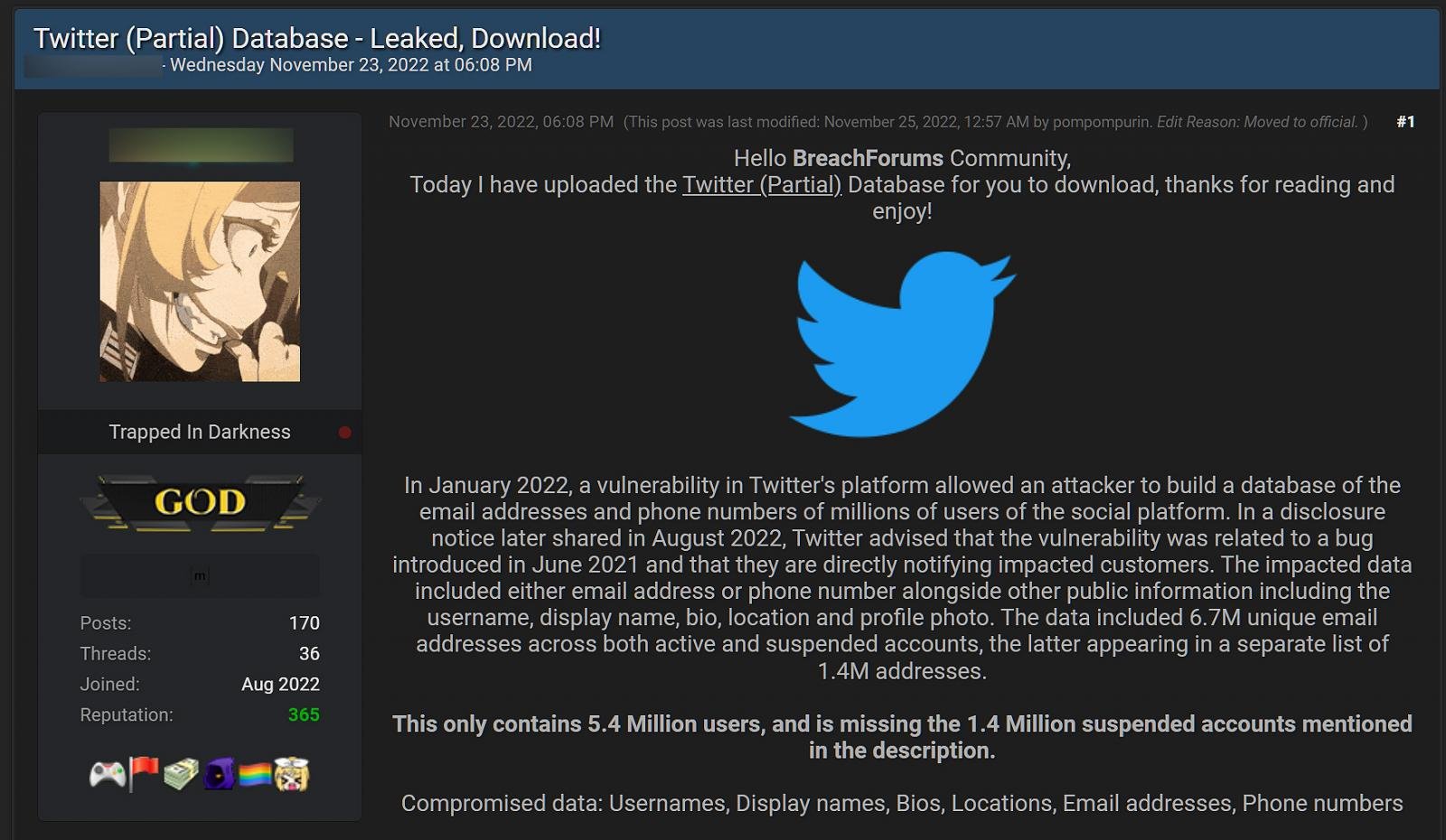
5,485,635 Twitter user records that contain personal data were released on November 24th, for free, on a hacker forum. Cybersecurity researchers say that the data was stolen due to an API vulnerability that Twitter announced to have fixed in January this year.
The same data is thought to have been previously for sale in August, but cybersecurity researchers have strong reasons to fear that there`s an even bigger data dump, reaching over 17 million user accounts, that was disclosed.
Twitter Users, Watch Out for Targeted Phishing Attacks!
While some of the data leaked are only public information, like Twitter IDs, names, and login names, there is also private information that was disclosed, like phone numbers and email addresses.
Threat actors that are into phishing attacks can easily now use the data for obtaining the victims` login credentials. So, Twitter users have all the reasons to be on guard and carefully read twice any email that seems to be sent from Twitter. Ignore or at least make sure you thoroughly check emails that announce that your Twitter account has login problems or had been suspended and that you need to log in to a non-Twitter domain in order to make things straight. You might be the target of a phishing attack.
Where Does the Data Come From
An update Twitter did to their code in June 2021 led to a bug that was discovered and fixed in January this year. At first, threat actors that took advantage of the vulnerability put the data on sale on a hacking forum for 30.000$. Shortly after discovering the data spillage, Twitter came up with some explanations and advised its users to activate multi-factor authentication:
In July 2022, we learned through a press report that someone had potentially leveraged this and was offering to sell the information they had compiled. After reviewing a sample of the available data for sale, we confirmed that a bad actor had taken advantage of the issue before it was addressed.
(…)
While no passwords were exposed, we encourage everyone who uses Twitter to enable 2-factor authentication using authentication apps or hardware security keys to protect your account from unauthorized logins.
According to BleepingComputer, not only the 5.4 million records are at stake right now, as the bug appears to have been exploited by more than one threat actor.
They have reasons to believe that there is another data dump, containing more Twitter records that include personal phone numbers, account names, Twitter ID, bio, and screen names.
BleepingComputer has obtained a sample file of this previously unknown Twitter data dump, which contains 1,377,132 phone numbers for users in France. Furthermore, none of these phone numbers are present in the original data sold in August, illustrating how much larger Twitter’s data breach was than previously disclosed and the large amount of user data circulating among threat actors.
Threat Actor Pompompurin states they have nothing to do with the newly discovered data dump and reckons there might be other threat groups that exploited the Twitter API vulnerability.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security









