Contents:
Researchers have identified the real-world identity of the threat actor behind Golden Chickens Malware-as-a-Service (MaaS), known as “badbullzvenom.”
A 16-month-long investigation by eSentire’s Threat Response Unit revealed multiple instances of the badbullzvenom account being shared between two individuals.
The second threat actor, Frapstar, identifies themselves as “Chuck from Montreal”. The cybersecurity firm was thus able to piece together the hacker`s digital footprint, including his real name, pictures, home address, the names of his parents, siblings, and friends, along with his social media accounts and his interests. He is also said to be the sole proprietor of a small business that’s run from his own home.
Golden Chickens – Upon a Closer Look
Also known as Venom Spider, Golden Chickens provides Malware-as-a-Service through a variety of tools, such as Taurus Builder, which creates malicious documents, and More_eggs, which serves additional payloads via JavaScript.
Cobalt Group, Evilnum, and FIN6 have all used the threat actor’s cyber arsenal, causing losses totaling $1.5 billion.
As part of past More_eggs campaigns, some of which date back to 2017, threat actors spear-phished LinkedIn business professionals with bogus job offers so they could take control of their machines, harvesting information and deploying new malware on them. After a switch in tactics last year, resumes laden with malware were used as an infection vector to compromise corporate hiring managers.
According to The Hacker News, the earliest documented record of Frapstar’s activity goes back to May 2015, when Trend Micro described the individual as a “lone criminal” and a luxury car enthusiast.
About the Identity Reveal
‘Chuck,’ who uses multiple aliases for his underground forum, social media, and Jabber accounts, and the threat actor claiming to be from Moldova, have gone to great lengths to disguise themselves. They have also taken great pains to obfuscate the Golden Chickens malware, trying to make it undetectable by most AV companies, and limiting customers to using Golden Chickens for ONLY targeted attacks.
Chuck is suspected to be one of two threat actors operating the badbullzvenom account on the Exploit.in underground forum, with the other party possibly located in Moldova or Romania.
In their 16 months investigation, the researchers were able to reconstruct the social media trail which led to the positive identification of one of the cybercriminals.
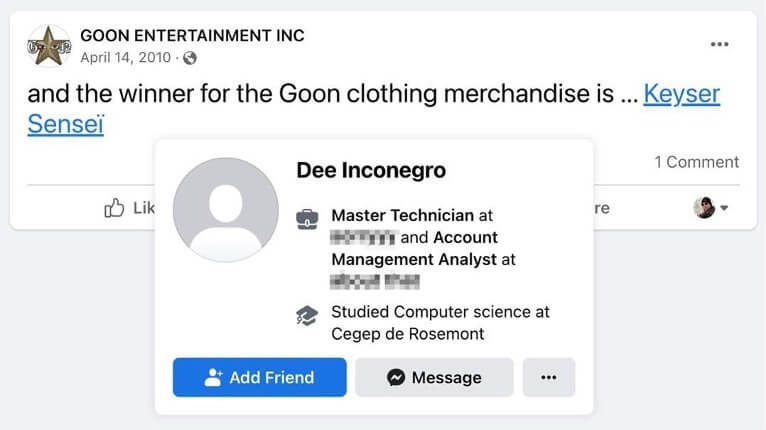
[…] we find a Pinterest account for “Dee Inconegro”, with a few boards created under it. One of those boards is dedicated to BMW M5 series photos, and another is dedicated to photos of English Bull Terriers, and the name of the board is “Bad Bullz”.
The same username is also found on Facebook, yet this time there are references to this account in other users’ posts, one of which referred to the account by an older name, “Keyser Sensei”.
The complete analysis is available in TRU report, here.
Recent Campaign
A new attack campaign was exposed targeting e-commerce companies, tricking recruiters into downloading a rogue Windows shortcut file masquerading as a resume from a website.
This shortcut contains malware dubbed VenomLNK, which is used to drop More_eggs or TerraLoader, which then serves as a conduit for deploying various modules, such as TerraRecon (for profiling victims), TerraStealer (for information theft), and TerraCrypt (for ransomware extortion).
“The malware suite is still actively being developed and is being and sold to other threat actors,” the researchers concluded, urging organizations to be on the lookout for potential phishing attempts.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security







