Contents:
[playht_player width=”100%” height=”90px” voice=”Michael (en-US)”]
On Dec. 11, 2021, Kronos, a workforce management company that serves over 40 million people in over 100 countries, was notified that a ransomware attack had compromised its Kronos Private Cloud.
As a result of the attack, millions of Kronos employees are still short hundreds or thousands of dollars as the Kronos software continues to fail to reconcile to this date.
The outage and incident affected many organizations, including Tesla, PepsiCo, Whole Foods, and the New York Metropolitan Transit Authority.
In the Northern District Court of California, Tesla and PepsiCo employees filed a class action lawsuit against UKG, alleging negligence in data security practices.
As a result of the Kronos outage, New York MTA employees filed a separate lawsuit in U.S. District Court for the Southern District of New York alleging that overtime wages were not paid.
It was a huge mess that was hard to avoid. However, it’s possible to manage third-party risks, and we’ll tell you exactly how.
In today’s article, we’ll take a look at the following:
- How the Kronos ransomware attack happened;
- What you can do in a similar situation;
- How to manage third-party risks.
Let’s begin!
How the Kronos Ransomware Attack Happened
As with any ransomware attack, the hackers hold the victim’s data or information as ransom until the victim pays the demanded ransom.
Kronos (Ultimate Kronos Group or UKG) is a well-known suite of workforce management solutions for human resources (HR) functions such as monitoring employee attendance and processing payroll. With Kronos’ ability to be a scalable, mobile, and secure platform for managing HR functions, its popularity is based on its cloud-based nature.
As a result of the Kronos ransomware attack of 2021, several companies could not process paychecks or access employee attendance records for several weeks.
According to the company, on-premises and self-hosted companies were not affected by the ransomware attack.
The potential consequences of the Kronos ransomware attack were that it affected thousands of users and prevented third-party access to valuable data.
For example, White House COVID-19 team members could not access their data from Maryland hospitals when Maryland experienced its most significant hospitalization spike.
One of the significant impacts of the Kronos ransomware attack was that the credibility of cloud-based solutions, mainly due to security and privacy concerns, was significantly compromised.
How Did the Attack Work?
The ransomware was executed by hackers who targeted Kronos Private Cloud (KPC) and stole client data. Banking Scheduling Solutions, Healthcare Extensions, UKG Telestaff, and UKG Workforce Central were all hosted on Kronos’ public cloud. Once the ransom payment had been made, the stolen data could be decrypted with the right decryption tools.
As a result of the Kronos ransomware attack, Kronos was forced to pay a ransom to regain access to its stolen data. Unfortunately, Kronos has yet to reveal the details of the attack mechanism.
To gain access to enterprise software, ransomware attackers typically use compromised user credentials or spear phishing emails to infiltrate security protocols.
How Was the Attack Handled?
The company relied on manual and semi automated systems to deliver some functionality to compromised clients after the attack.
In addition, several clients had to rely on their plans to function: one healthcare company resorted to using a “clone pay period,” which paid employees following the number of hours worked in the last attendance cycle before the attack compromising the latest attendance records.
Kronos has not disclosed the nature or amount of the ransom demanded by attackers. However, according to NBC Boston, Kronos paid the ransom.
How Can You Prevent Another Kronos Style Ransomware Attack
Having an incident response plan for your company is essential when it experiences a cyber-attack, but you should also have one for your vendors when they share it.
Don’t get us wrong; we don’t mean meddling in your service provider’s recovery activity. However, safeguarding critical operations tied to third parties is essential.
Investing in cyber awareness training and education for all employees can help businesses minimize the risk and impact of ransomware attacks. Users can recognize potential phishing attempts if they are adequately prepared.
Hackers often rely on users clicking on malicious links to gain access to enterprise systems. Therefore, user education can be a crucial defense against ransomware attacks.
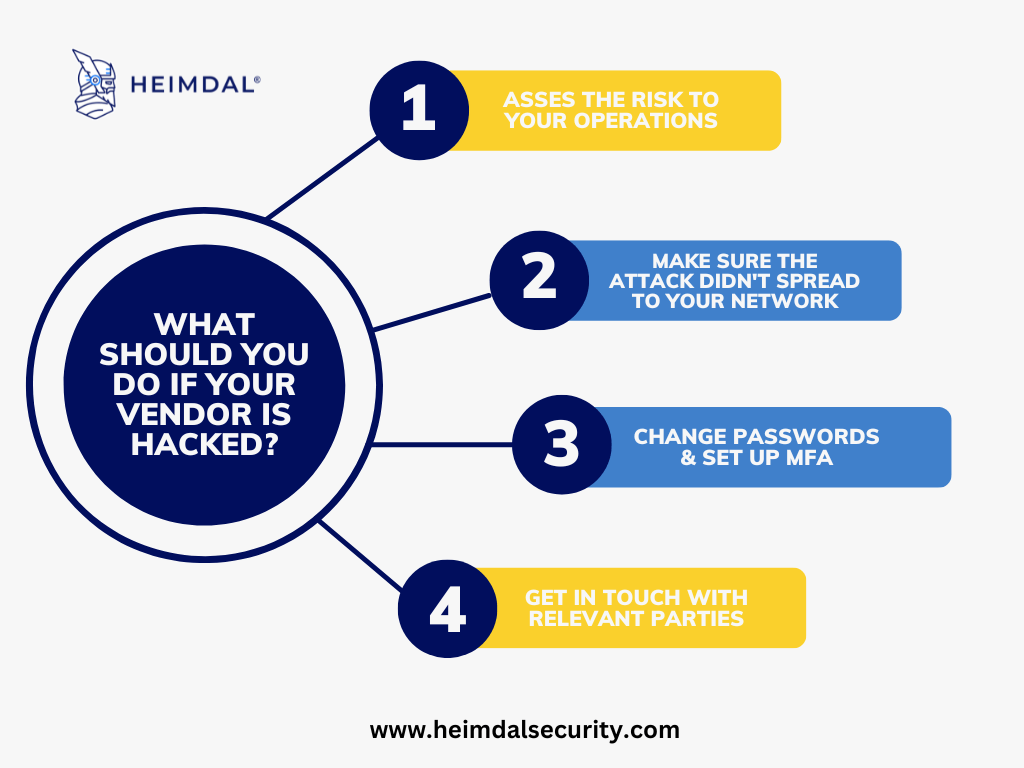
Here are some things you need to do when your vendor is hacked:
- Assess the risk to your operations.
When a vendor goes down, you should first figure out how it will affect your operations. Check if any critical applications are tied to the vendor and estimate how much damage you will sustain if service is lost.
- Make sure the attack did not spread to your network.
Check whether the attack can spread to your network. In the Kronos case, the attack was isolated to the company alone, but there have also been cases of attacks spreading to the vendor’s customers. Perform a thorough network scan for possible data breaches and check your activity logs for suspicious activity.
- Set up MFA and change your passwords.
You should immediately set up multi-factor authentication (MFA) and implement company-wide password changes. By doing so, attackers won’t be able to use stolen data, such as passwords and login credentials, to break into your system.
However, it would help if you erred on caution because it’s hard to determine precisely what data the attackers gained from your vendor.
- Contact relevant parties as soon as possible.
When dealing with any security breach, speed and information are critical. Inform your IT security team or your managed service provider (MSP) of any such issue as soon as possible. They will be able to act more quickly to protect your network, assess the damage, and hopefully resolve any problems that may arise.
How to Handle Third-Party Risk
There’s only so much you can do to manage third-party risk. However, you can still take steps to minimize your exposure because you can’t control how an external company operates its cybersecurity. Here are some things you can do to manage third-party risk:
- First, identify each vendor’s security posture.
If you’re dealing with a vendor, ask the right questions. Try to determine what security measures they have in place against cyber threats, what security standards they adhere to, and what guarantees they offer should their service fail. Keep their cybersecurity posture in mind at all times.
- Prioritize each vendor based on the risk.
Once you have determined the risks associated with each vendor, you will be able to categorize them based on their importance to your business and the potential threats they may pose.
Doing so will give you a clearer picture of your third-party service portfolio. In addition, it will help you identify any critical issues before they develop and decide if switching to another vendor is the right move.
- Ensure that critical applications are redundant.
For mission-critical operations, employ redundancy whenever possible. You will be able to recover your bearings if your vendors suffer a service outage, so if your critical app fails, you will already have a workaround to minimize disruption.

Heimdal™ Ransomware Encryption Protection
- Blocks any unauthorized encryption attempts;
- Detects ransomware regardless of signature;
- Universal compatibility with any cybersecurity solution;
- Full audit trail with stunning graphics;
Wrap Up
Providing its customers with an outstanding integrated cybersecurity suite, Heimdal ® offers Ransomware Encryption Protection, which is universally compatible with any antivirus solution and 100% signature-free, ensuring superior detection and remediation of all types of ransomware.
Moreover, our patch management automation solution, Heimdal ® Patch & Asset Management, keeps hundreds of thousands of enterprise endpoints secure and up-to-date. Although we keep our data updated at a much higher rate than industry benchmarks because of our quick response and implementation times, we still have fascinating insights to come out of it.
Companies looking to protect themselves from ransomware and other cyberattacks can benefit significantly from identity and access management (IAM) and other security software. This is why Heimdal ® Privileged and Access Management is excellent. You can create automated defenses using the only solution that combines PAM, zero-trust execution, and automatic de-escalation of user rights when a threat is detected.
See for yourself by booking a demo!
If you liked this article, follow us on LinkedIn, Twitter, Facebook, YouTube, and Instagram for more cybersecurity news and topics.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security








