Contents:
A new malicious campaign emerged last month having its focus on Docker servers that are not properly configured, being thus exposed to threats. Reportedly linked to TeamTNT, the cyberattacks are designed for crypto mining purposes.
Docker Servers Being Abused: Details
A recent report from the TrendMicro researchers describes how such a cyberattack works:
- In the beginning, by means of an accessible Docker REST API a container will be created on the susceptible host;
- For the hosting of compromised images, threat actors use compromised Docker Hub accounts or that are controlled by them. These images will be later deployed on the host.
- As the researchers mention, there were noticed more than 150,000 image pulls.
- Cronjobs are further on executed via the dropped container.
- The same container also retrieves different malicious tools for lateral movement and post-exploitation purposes.
- Among the mentioned tools, some that perform credentials theft, cryptocurrency miners, and container escaping scripts could be mentioned.
- Following similar past DDoS patterns, hackers focus on 2375, 2376, 2377, 4243, 4244, ports they check while looking for other vulnerable instances.
- Server data gathering attempts also make parts of the threat actors’ attack arsenal.
- The server data they are interested in include CPU cores numbers, type of operating system, architecture, container registry, and swarm participation status.
- The AlpineOS system underlays the created container image.
- For root-level access purposes, this image is executed with flags.
The experts also provided an illustration that shows the attack flow:
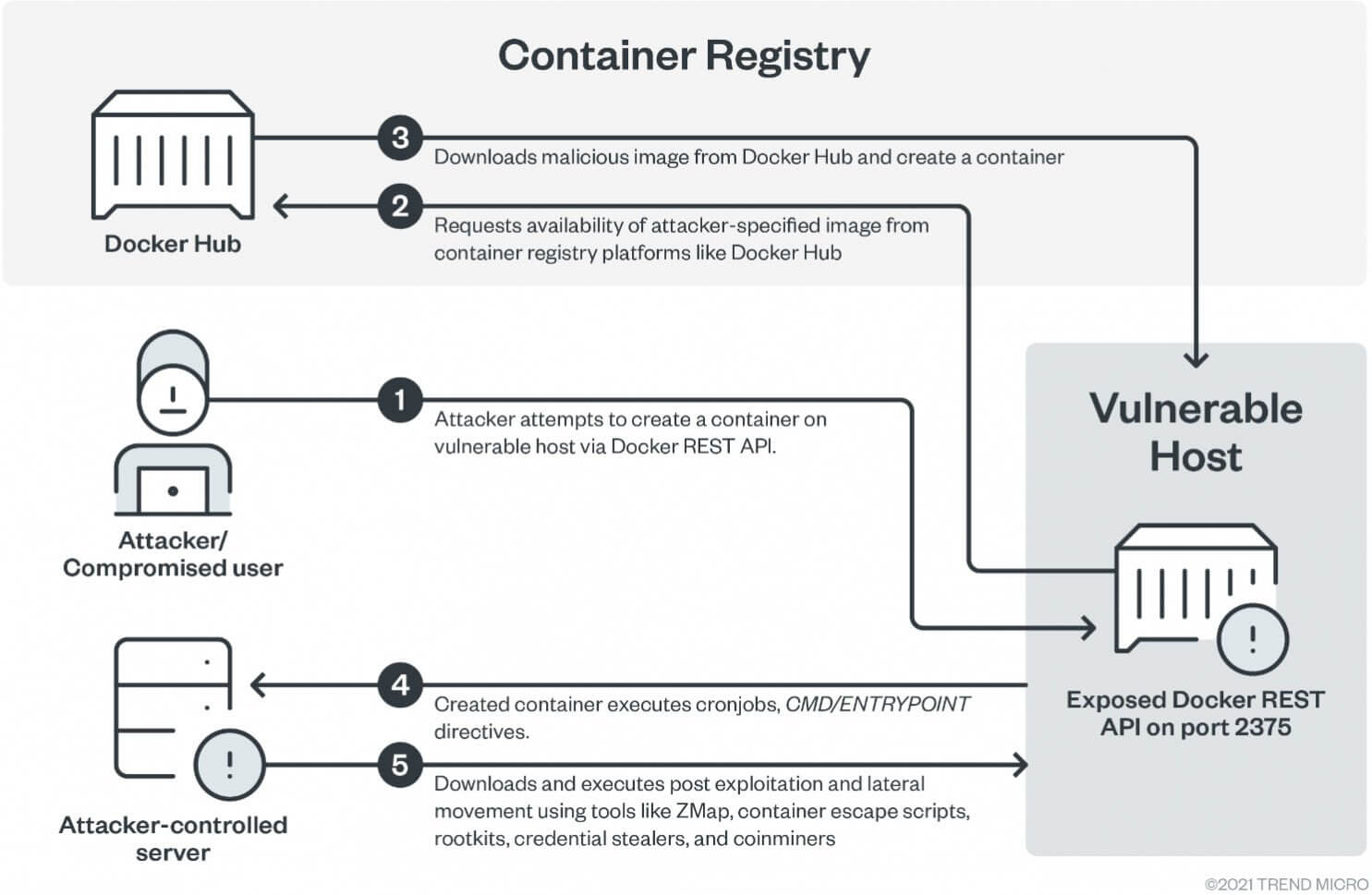
The researchers link the abusing of Docker servers with TeamTNT, a threat actor group focusing on Docker instances since 2020.
In this campaign, it seems that the goals follow 3 directions: Monero crypto miners installation, susceptible Internet-exposed Docker instances scanning, and network access achievement via container-to-host escapes.
It was also mentioned that TeamTNT used Docker Hub accounts under their control too for the docker images dropping as due to this method, distribution points work better for them as these cannot be easily mapped, reported, or taken down.
Docker Systems: the Favorite of TeamTNT
According to BleepingComputer, there is a whole background over the TeamTNT’s focus on Docker systems exploitation.
In August last year, they were creating a worm for Docker and Kubernetes exploitation purposes, then in October the same year Monero mining and credentials theft features were included.
The beginning of 2021 brought also updates for the TeamTNT’s miners, meaning that upgrades based on techniques capable to avoid detection were released.
What Is Docker?
Docker is an open-source project that provides developers with an easy way to use containers, which can be used for developing and shipping software. Docker containers are lightweight virtual machines that provide the software with a level of isolation, allowing it to run in its own space on the operating system.
How Can Heimdal™ Help You?
Heimdal™ is always up to date with the latest cybersecurity trends and so are its solutions. We are not the only ones who say this: our stunning Threat Prevention has been just designated “Best Cloud-Delivered Security Solution of the Year” working on preventing hidden cyber threats compromise your networks and endpoints. Combining Machine Learning, cybercrime intelligence, and prevention based on artificial intelligence, Threat Prevention makes for the best product that lets you stay away from cyber threat scenarios.
Did you enjoy this article? Follow us on LinkedIn, Twitter, Facebook, Youtube, or Instagram to keep up to date with everything we post!


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










