Contents:
Patching is the second most challenging and resource-consuming task of a System Administrator.
That’s what Alex Panait told me when I wanted to know his opinion on the benefits and hurdles of patching.
Alex has been a System Administrator in Internal IT at Heimdal for the last 8 years.
He’s seen the company developing and brought up the whole system from zero.
While spending your time and energy to close known vulnerabilities is totally worth it, Alex advises that you automate the process.
Key Takeaways
- What tasks give System Administrators a hard time?
- Why is applying patches such a tiresome task?
- How does patch management impact compliance goals?
- Does Patch Tuesday help in automatically closing all Windows vulnerabilities?
- What are the risks if you don’t patch in time?
- Why don’t SysAdmins apply all patches on all software to stay safe?
- How should System Admins prioritize patches?
- How do you decide which patches to apply first in your infrastructure?
- How does Heimdal Patch and Asset Management help with this?
- How does the manual patch management process work?
- Advice for SysAdmin newbies.
Q What tasks give System Administrators a hard time?
A
In my experience, incoming alerts, like AV and malicious connection attempts alerts, are the most resource-consuming.
Why? Because you need to check thoroughly each one of them.
You don’t want to risk dismissing an alert as a false positive and discover later that it pointed to a real threat.
Patching, of course, comes next.

Q Why is applying patches such a tiresome task?
A
One reason is the continuous need to stay up to date with the latest security flaws.
For example, you should be aware of all that happens with Windows.
It’s a largely used operating system in lots of companies.
As a System Admin you always must follow:
- news alerts ;
- CVE databases, like The National Vulnerability Database in US;
- patch releases from software vendors;
- cybersecurity forums, like r/netsec on Reddit;
- updates from regulatory bodies, like Health Insurance Portability and Accountability Act (HIPAA) or Payment Card Industry Data Security Standard (PCI DSS).
Q How does patch management impact compliance goals?
A
Patch management plays a crucial role in demonstrating the company adheres to industry standards and best practices for mitigating security risks.
Patching known vulnerabilities in due time is part of cybersecurity regulations.
Failing to do that brings fines in case of a data breach.
In the US, for example, the Federal Trade Commission (FTC) is responsible for enforcing cybersecurity regulations and legislation on companies.
They check and, when the case, fine companies that fail to comply with security standards.
Some examples of cybersecurity compliance standards are:
- Payment Card Industry Data Security Standard (PCI DSS) – for companies that work with credit card information.
- GDPR (General Data Protection Regulation) – for organizations handling personal data of people in the European Union (EU).
- HIPAA (Health Insurance Portability and Accountability Act) – for healthcare organizations and their providers to protect sensitive patient data.
If you’re breached, proving compliance with security regulations helps:
- avoid fines;
- meet cyber insurance requirements.
Q Does Patch Tuesday help in automatically closing all Windows vulnerabilities?
A
Not all Windows updates are deployed automatically. Sometimes Microsoft just says “hey, you need to apply a certain setting.”
If you’re not aware this is happening and you need to act, the vulnerability will remain open for hackers to exploit it.
Microsoft can push all updates.
But you need a centralized location to manage the updates and make sure they get installed.
Q What are the risks if you don’t patch in time?
A
Unpatched software might contain vulnerabilities that bad actors could exploit to gain access to your organization. T
his can mean either a data breach, a malware infection, a ransomware attack, etc.
In 2017 the WannaCry ransomware outbreak infected more than 200,000 devices in 150 countries.
The malware exploited a known vulnerability (EternalBlue) in unpatched Windows systems.
Researchers estimated the financial damage to $4 billion.
When the WannaCry epidemics broke out, Microsoft had already released a security patch to protect users against this exploit.
IT teams had two months to apply the patch, before the ransomware attack hit.
Q Why don’t SysAdmins apply all patches on all software to stay safe?
A
Being able to patch all software depends on the company’s size and the diversity of their infrastructure.
Patching a software also depends on:
- what version of Windows runs on the device;
- existing system settings;
- organizational policies.
It could happen that some users need a certain version of software to do their work.
Updating to a recent version would generate incompatibility and workflow disruption.
For example, computers in your accounting department run on Windows 2008, which is End-Of-Life.
This means whatever new vulnerabilities appear for this OS, Microsoft will no longer release patches for it.
The solution is updating to a newer Windows version.
But your accounting software only runs on Windows 2008.
If you update your OS, the software won’t work anymore.
So, the accounting department won’t be able to do their job.
In this case, as a System Admin, what you can do is warn about the severity of this security risk and advise on buying new software.
And, of course, you should try to close all the known loopholes, isolate those machines as best as possible.
Q How should System Admins prioritize patches?
A
Depending on the business’ workflow and specifics, I advise prioritizing patches based on:
- how critical is a certain app for your activity;
- whether the app has access to sensitive data or communicates with such an app.
Q How do you decide which patches to apply first in your infrastructure?
A
Before taking any decision, I make sure that:
- there are no apps installed on the company devices that I am not aware of;
- I have control over admin privileges to prevent employees downloading unapproved software;
- I stay up to date with patch releases and vulnerabilities regarding the apps your company uses.
If a high risk zero-day appears for a software that is critical for my company, I mitigate the exploit risk until the vendor releases a patch to close it.
I follow the vendor’s advisory to see what safety measures I should apply until a patch is available.
If the flawed software is not that critical for the company’s activity, I might even uninstall it until I get a patch.
If the vendor already released a patch, I prioritize vulnerabilities that may have a higher impact on data safety.
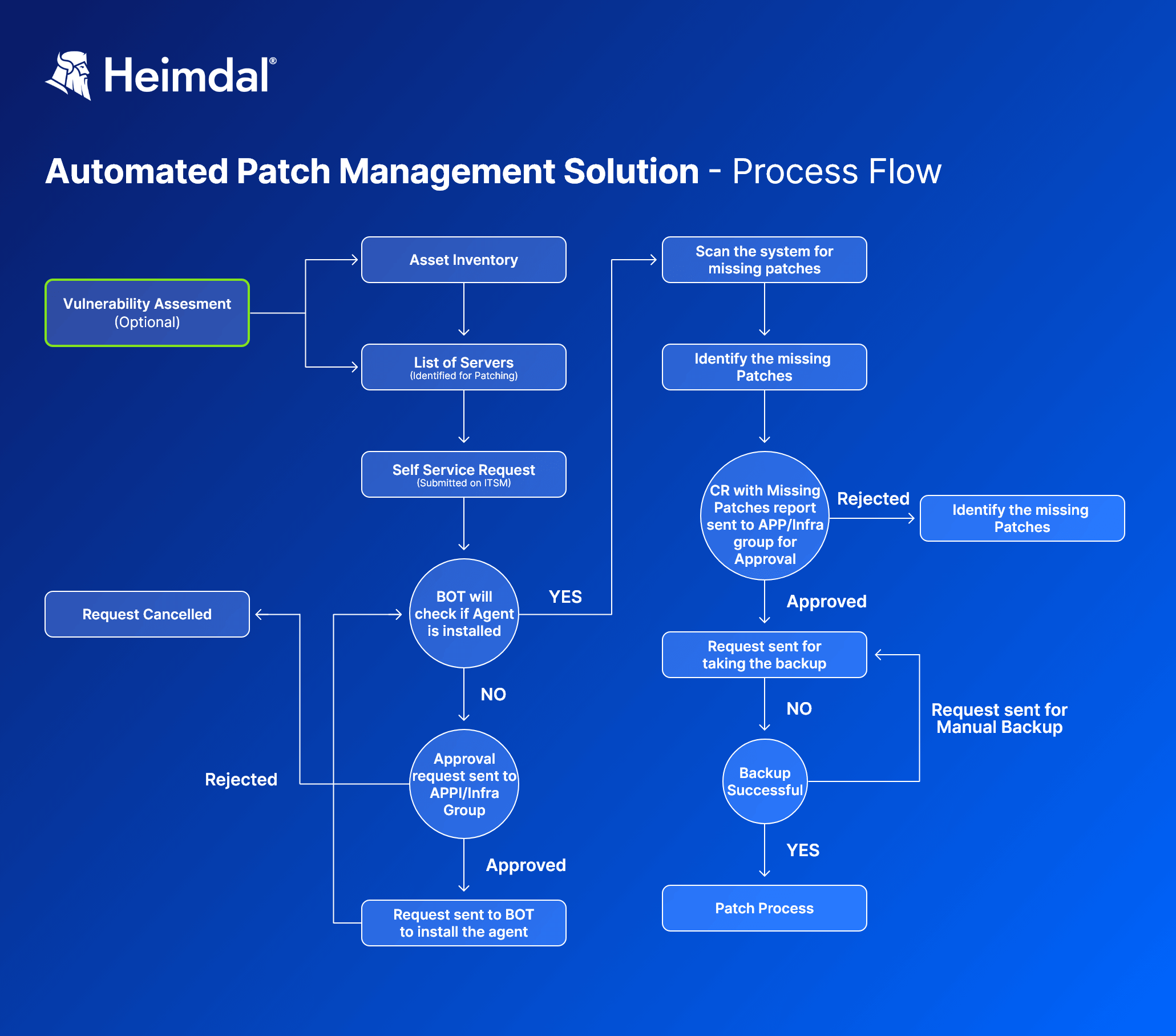
Q How does Heimdal Patch and Asset Management help with this?
A
Heimdal’s patching tool, which I use for our devices, helps apply available patches automatically.
Once the vendor releases an update, we apply it.
Through the Heimdal dashboard I can check:
- What are the vulnerabilities of an app;
- How high is their severity score – CVSS;
- Whether there’s a patch available to close the vulnerability.
Also, I don’t need to manually:
- Install the patch ;
- Test the patch.
Being able to do all of that in one click, through the Heimdal dashboard, saves lots of time.
Q How does the manual patch management process work?
A
If you don’t automate patching, then you need to:
- create some scripts that check the sites you’re interested in and alert you in case there’s a new patch available.
or
- manually check for new patches on the vendors’ sites, daily or weekly.
Usually, the vendor sends updates to their customers, but you might need to do all the work.
You’ll need a software inventory, so you know what vendors you should check on. If there’s a new update you need to install, the patching process steps are:
- download the patch;
- test it on a virtual machine;
- see if it works as intended;
- deploy it on several endpoints. Never deploy it on all devices, even if you tested the patch before. No virtual machine will replicate the exact conditions you have on a real device;
- check if all goes well. Did the patch install properly? Is it working as it should? If not, you need to debug;
- apply the patch on all devices.
So, in the absence of an automated patch management tool, you need to deal with all that.
Q What would you advise a rookie in this field to do so they keep all software up to date?
A
Use Heimdal Patch and Asset management or find a similar tool, that automates:
- asset inventory;
- patching;
- deployment;
- testing;
- checking for patches.
Automated patch management tools cut off the routine of repetitive tasks. This leaves enough time for a System Administrator to attend to other tasks such as system monitoring, alert investigations, and more.
From safety to functionality and compliance, you have all the reasons in the world to take patch management seriously.
But since it’s not the only task of a System Administrator, you’ll want patching to take as little of your time as possible.
In this case, automation is key.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, and Youtube, for more cybersecurity news and topics.

Heimdal® Patch & Asset Management Software
- Schedule updates at your convenience;
- See any software assets in inventory;
- Global deployment and LAN P2P;
- And much more than we can fit in here...










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security