Contents:
The Advanced Persistent Threat (APT) known as StrongPity has been observed distributing a fake Shagle chat app that is a trojanized version of the Telegram for Android app with an added backdoor.
Shagle is a legitimate random-video-chat platform that allows strangers to talk via an encrypted communications channel. However, the platform is entirely web-based, meaning there is no option for a mobile app.
A fake Shagle website has been used by StrongPity since 2021 to trick victims into downloading malicious Android apps. Using this app, hackers can spy on their targeted victims, including monitoring phone calls, collecting SMS texts, and stealing contact information.
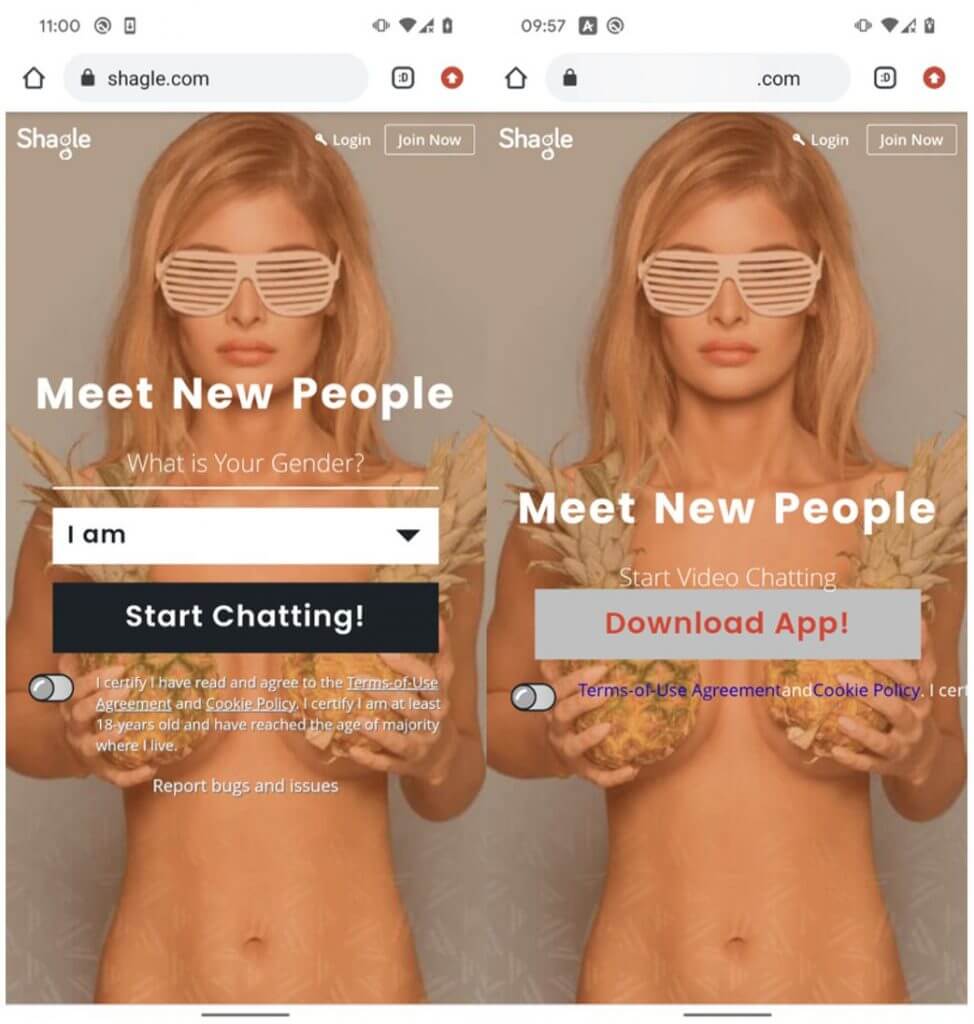
Real site on the left vs fake one on the right.
A Brief Recap on StrongPity Activity
The latest StrongPity activity was discovered by ESET researchers who attributed the campaign to the espionage APT group based on code similarities with past payloads. Additionally, as BleepingComputer points out, the Android app is signed with the same certificate the threat actors used to sign an app that mimicked the Syrian e-gov Android application in a 2021 campaign.
StrongPity (Promethium or APT-C-41), however, is also known for a previous campaign that distributed trojanized Notepad++ installers and malicious versions of WinRAR and TrueCrypt to distribute malware.
In 2016, StrongPity was detected by Kaspersky in a campaign that targeted specific users in Belgium and Italy who were interested in Truecrypt and Winrar software. These APT groups’ campaigns are not commonly seen but different research groups have detected several StrongPity campaigns over the years.
Trojanized Android Telegram App
StrongPity distributed a malicious Android app named “video.apk,”, a modified version of Telegram v7.5.0 (February 2022).
According to ESET, victims most likely arrive on the fake Shagle website through spear phishing emails, smishing, or instant messages. The malicious APK is not available on Google Play, but rather provided directly from the fake Shagle site.
Furthermore, ESET researchers claim the cloned site first appeared online on November 2021, meaning the APK has probably been under active distribution ever since. However, the first confirmed detection in the wild came in July 2022.
Using Telegram for the hacking group’s fake app has the disadvantage that if the victim already has the real Telegram app installed on their phone, the backdoored version cannot be installed.
The report mentions that, due to overuse, the API ID used in the captured samples has been limited, so the trojanized app will no longer accept new user registrations, thus the backdoor won’t work.
This might mean that StrongPity operators didn’t think this through, or perhaps there was enough time to spy on victims between publishing the app and it being deactivated by Telegram for APP ID overuse. Since no new and working version of the app was ever made available through the website, it might suggest that StrongPity successfully deployed the malware to its desired targets.
The StrongPity group has been active since 2012, commonly hiding backdoors in legitimate software installers. Based on ESET’s report, it appears this tactic is still the threat actors` favourite even after a decade.
How the Malicious App Spies on its Victims
Upon installation, the malware requests access to Accessibility Service and then fetches an AES-encrypted file from the attacker’s command and control server.
This file consists of 11 binary modules extracted to the device and used by the backdoor to perform various malicious functionality:
- libarm.jar – records phone calls
- libmpeg4.jar – collects text of incoming notification messages from 17 apps
- local.jar – collects file list (file tree) on the device
- phone.jar – misuses accessibility services to spy on messaging apps by exfiltrating contact name, chat message, and date
- resources.jar – collects SMS messages stored on the device
- services.jar – obtains device location
- systemui.jar – collects device and system information
- timer.jar – collects a list of installed apps
- toolkit.jar – collects contact list
- watchkit.jar – collects a list of device accounts
- wearkit.jar – collects a list of call logs
Data collected by the app is stored in its directory, encrypted with AES, and ultimately sent back to the attacker’s C2 server. The malware can read notification content from Messenger, Viber, Skype, WeChat, Snapchat, Tinder, Instagram, Twitter, and Gmail by abusing the Accessibility Service.
In rooted devices where the regular user has administrator privileges, the malware automatically grants itself permission to change security settings, write to the filesystem, reboot, and perform other dangerous actions.
As a means to mitigate this kind of attacks, when installing new apps on Android, be cautious with APKs not sourced from Google Play.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security







