Contents:
The Advanced Persistent Threat (APT) known as StrongPity is distributing malware-laced Notepad++ installers to infect their victims.
#APT #StrongPity NotePad++ installer(npp.8.1.7.Installer.x64.exe)
78556a2fc01c40f64f11c76ef26ec3ff
http[:]//advancedtoenableplatform.com pic.twitter.com/eEXZWIObnH— blackorbird (@blackorbird) November 30, 2021
The method is not new as this sophisticated cybercrime organization (also referred to as APT-C-41 or Promethium) was noticed delivering malicious WinRAR installers in highly targeted operations between 2016 and 2018.
In 2016, StrongPity was detected by Kaspersky in a campaign that targeted specific users in Belgium and Italy who were interested in Truecrypt and Winrar software. These APT groups’ campaigns are not commonly seen but different research groups have detected several StrongPity campaigns over the years.
The latest enticement involves Notepad++, a widely used free text and source code editor, and a Notepad replacement that supports several languages.
Because the malware ‘conceals’ itself inside a reputable program that is often available within companies, this attack technique is extremely effective.
The Attack Explained
In the early phase of the attack, the user downloads and runs the “Notepad++” setup file. The threat actor adds an Original Notepad++ icon to the malicious file in order to make it more convincing for the target.
As explained by BleepingComputer, once the malicious file is executed, it generates a new folder called “WindowsData” under C:ProgramDataMicrosoft and drops three distinct files on the computer that has been compromised:
- 8.1.7.Installer.x64.exe – the original Notepad++ installation file under C:\Users\Username\AppData\Local\Temp\ folder.
- exe – a malicious file under C:\Windows\System32 folder.
- exe – malicious keylogger under C:\ProgramData\Microsoft\WindowsData folder.
The first stage executable starts the genuine Notepad++ installation after the file is dropped, while the user is unaware of the two malicious files being installed in the background.
When the setup is complete, a new service called “PickerSrv” is generated, which ensures the malware’s persistence by executing it upon startup.
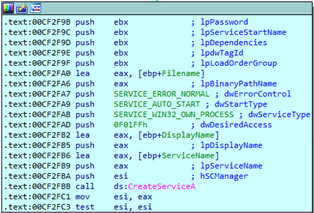
All user keystrokes are recorded by the keylogger and saved to concealed system files deposited in the ‘C: ProgramDataMicrosoftWindowsData’ folder. The StrongPity malware can also steal files and other information from the system.
While the keylogger runs in the background, winpickr.exe repeatedly checks C:\ProgramData\Microsoft\WindowsData folder for .tbl files. When a file is found containing the attributes of the log files created by ntuis32.exe (hidden, system, and read-only), it connects to its C&C server (https[:]//advancedtoenableplatform[.]com/contact[.]php) for file transfer. After sending the file to the C&C, winpickr.exe deletes the file on the endpoint.
What Can Users Do in Order to Be Protected?
If you need to use Notepad++, download the installer using the legitimate website.
Several other websites offer the source code editor, some of which pretend to be real Notepad++ portals but may carry adware or other malicious applications.
According to BleepingComputer, the URL that was delivering the malicious Notepad++ installers was removed after analysts identified it. However, the attackers were able to quickly register a new one.
Did you enjoy this article? Follow us on LinkedIn, Twitter, Facebook, Youtube, or Instagram to keep up to date with everything we post!


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










