Contents:
Ransomed.vc threat group claims they`re responsible for an alleged Sony data breach and attempt to sell the stolen data on the dark web.
While Ransomed.vc stated they compromised „all of Sony`s systems”, and stole 260 GB of data, the file tree they provided as proof does not exceed 6,000 files. As Sony allegedly refused to pay, the adversaries said they had no choice but to sell the stolen data. Despite the name suggesting otherwise, Ransomed.vc is not a ransomware gang, but rather an extortion one.
We have successfully compromissed all of sony systems. we will sell the data. due to sony not wanting to pay. DATA IS FOR SALE
Hackers also warned that unless a buyer shows up until September 28th, they will leak the data on dark forums.
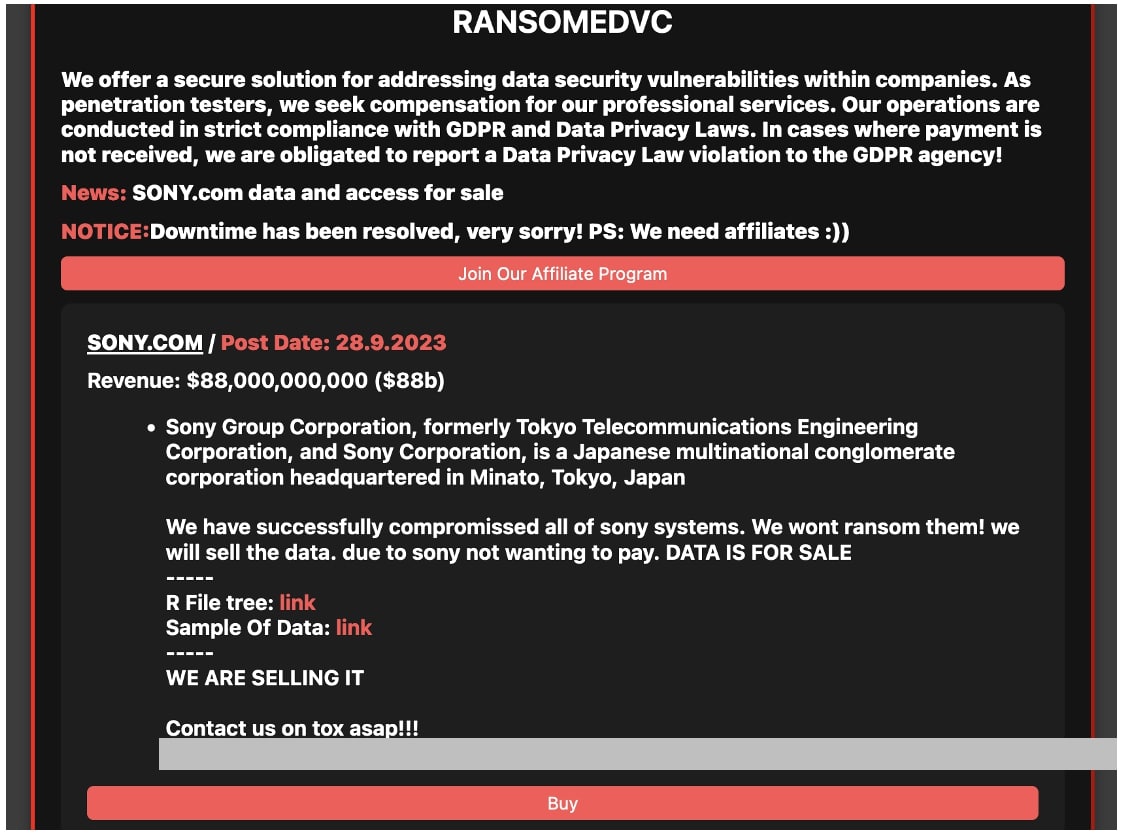
photo source: BleepingComputer
Details About Sony`s Stolen Data
Until now, Ransomed.vc only published 2MB of data, that comprised:
- screenshots of an internal login page,
- a PowerPoint presentation that included testbench information,
- Java files,
- build log files,
- HTML files.
Most of the files were written in Japanese.
Who Hacked Sony?
While the company declared they were conducting an ongoing investigation of the matter, another threat actor claimed to be the author of the Sony data breach.
A hacker dubbed MajorNelson said ”Ransomed.VCs are scammers who are just trying to scam you and chase influence.”
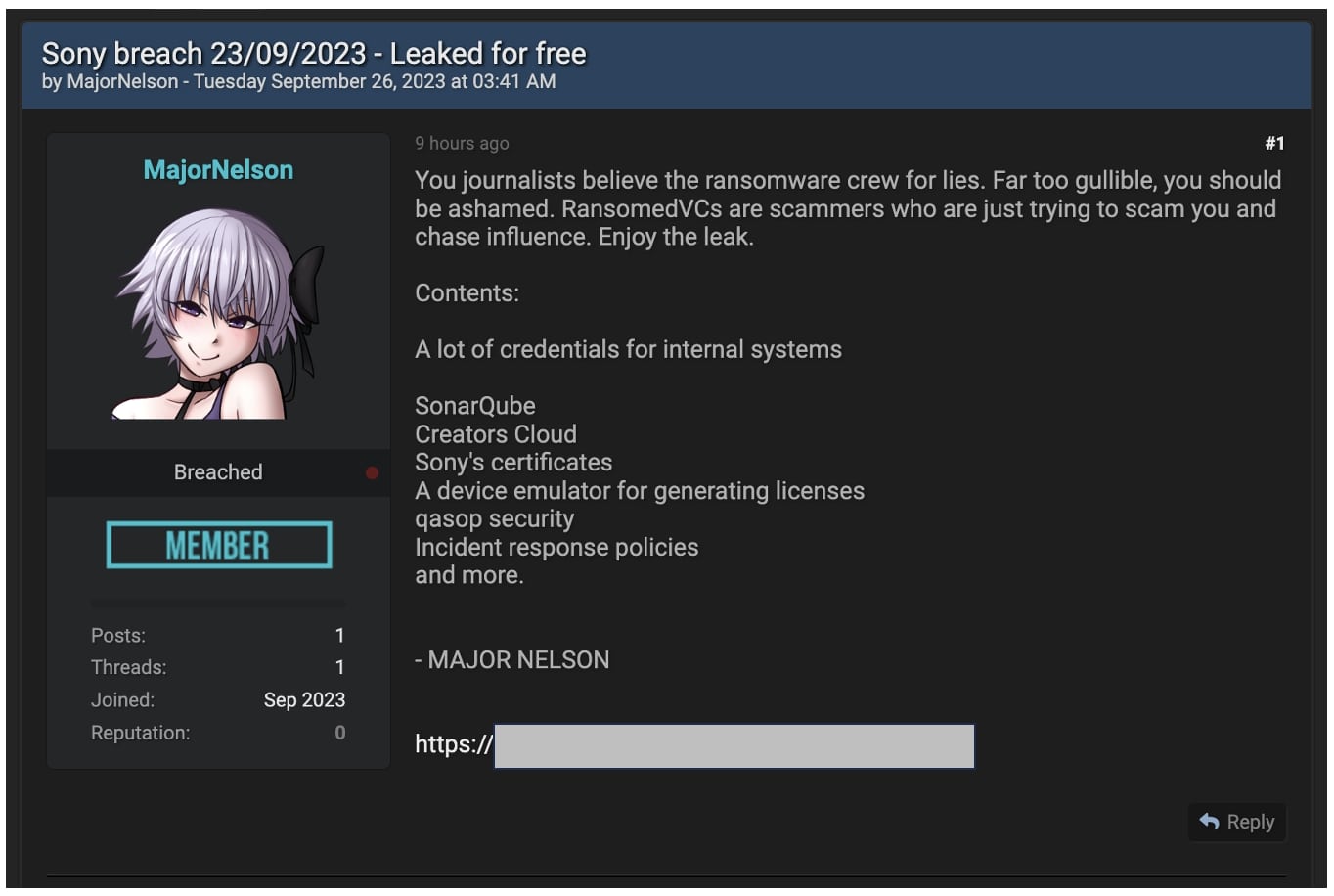
The adversary also posted a free 3.14 GB sample of the alleged stolen data. The data was leaked on BreachForums and included credentials for internal systems along with files related to:
- SonarQube,
- Creators Cloud,
- Sony’s certificates,
- A device emulator for generating licenses,
- Incident response policies.
It`s worth noticing that MajorNelson`s archive included both Ransomed.vc`s data and additional information.
Until now, it remains unclear which threat actor is the author of the alleged breach.
Use Data Encryption to Mitigate the Effect of a System Breach
Encrypting your data makes things safer in case of a system breach. Even if hackers get inside your system, they will not be able to compromise your most valuable data.
To get the best results, you should use encryption along with other protection measures. Here`s what you need to do to prevent a data leakage:
- Use application control,
- Enforce a Privileged Access Management (PAM) solution,
- Implement a password security policy,
- Use Multi-Factor Authentication (MFA)
- Use a Mobile Device Management (MDM) solution,
- Never miss a patch. Use an automated patch management product to keep software and old devices updated.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, and Youtube, for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security









