Contents:
A new malware has made its way onto the threat landscape. Security experts have revealed the emergence of the SharkBot Android trojan. It apparently targets crypto and banking services from the U.S., the U.K., and Italy. It works by exploiting devices accessibility features having the goal of credentials theft.
Characteristics of SharkBot Android Trojan
According to a report from the Cleafy researchers, who also gave the banking trojan this particular name “SharkBot”, there were identified 22 targets of the malware among which there were international UK and Italy banks, as well as 5 other crypto services. These experts discovered the malware at the end of October 2021. Its very name seems to be related to the strings the researchers under discussion found in its binaries, as the discovered strings had the word “sharked” within.
Following the report information, SharkBot Android trojan has the following characteristics:
- It will appear in the form of data recovery apps, live TV, or a media player
- Users will come across a pop-up that requires Accessibility Services enablement
- In order to perform ATS attacks, it exploits accessibility settings to gain full control over the Android device
Here is an example of how this SharkBot Android trojan performs an ATS attack:
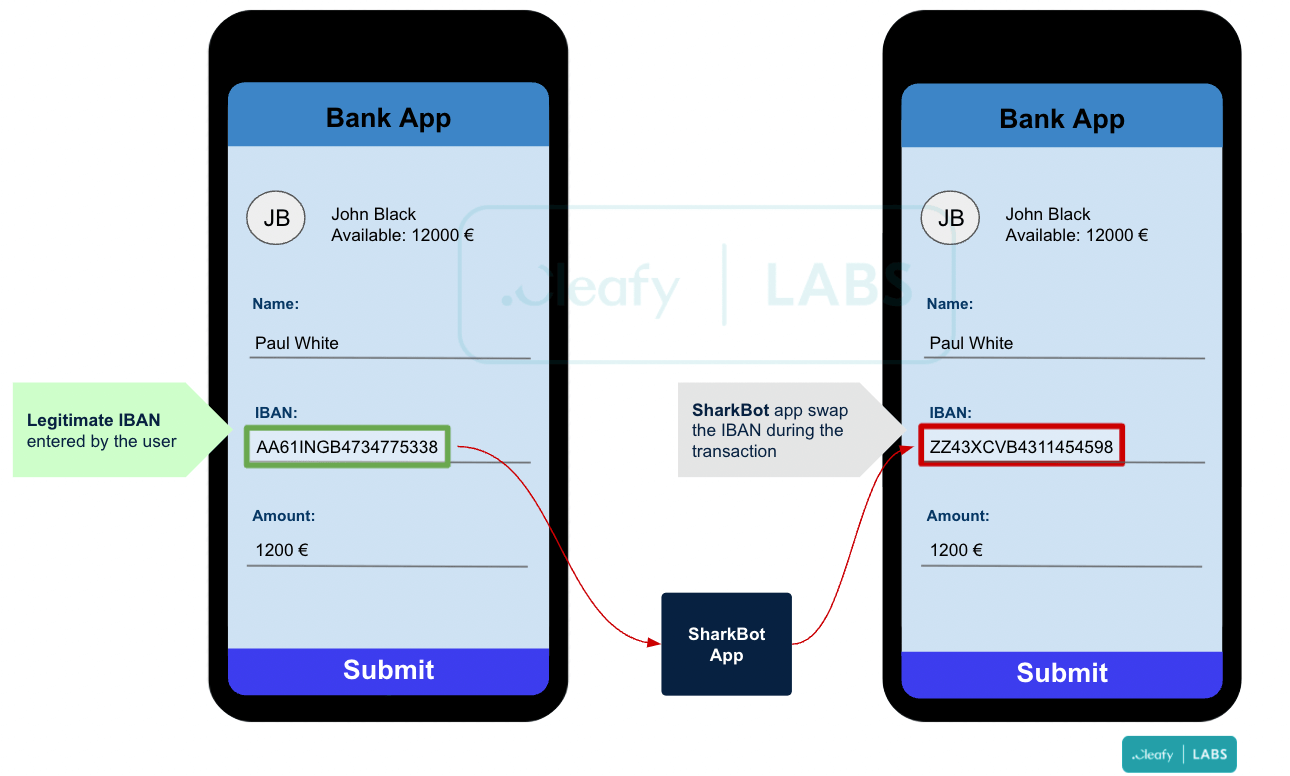
- This will let hackers alter fields in legitimate mobile bank apps by auto-filling them
- It can bypass banking enabled MFA authentication
- It can perform credentials theft through overlay attacks and also credit card info theft
- It has the capacity to intercept banking communications, the ones that are done via SMS
- It stands out because of its analysis and detection avoiding techniques like C2 communication encryption, emulator check running or after it is installed, it can remove the app icon pointing to it from the home screen.
- It also has the ability to enable functionalities like keylogging.
The main goal of SharkBot is to initiate money transfers from the compromised devices via Automatic Transfer Systems (ATS) technique bypassing multi-factor authentication mechanisms (e.g., SCA),” the researchers said in a report. (…) Once SharkBot is successfully installed in the victim’s device, attackers can obtain sensitive banking information through the abuse of Accessibility Services, such as credentials, personal information, current balance, etc., but also to perform gestures on the infected device.
However, malware samples could not be found in Google Play, this meaning the SharkBot Android trojan deployment on the compromised devices is done in a different way. Maybe through social engineering techniques or sideloading schemes.
Did you enjoy this article? Follow us on LinkedIn, Twitter, Facebook, Youtube, or Instagram to keep up to date with everything we post!


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










