Contents:
Email spoofing is a type of cyberattack in which a threat actor sends messages with a fake sender’s email address.
In email spoofing, attackers can make it seem like an email is sent by a familiar person such as a colleague, partner, or manager. Spoofing is the process of manipulating the from: field to create the impression that the email is coming from a certain individual.
Spoofers can sometimes create an email address that seems authentic by replacing just one or two letters in a company name, such as “Arnazon” instead of “Amazon,” or other letter switches that are difficult to notice.
Email spoofing is a tactic designed to collect personal information and data from online users, take over their online accounts, deliver malware, or steal funds. According to some studies, targets tend to open an email that looks like a genuine one and seems to be from a trustworthy sender.
Spoofed email messages, for the most part, are either deleted or redirected to the spam folder. The problem starts the second a victim is tricked into opening an email and clicking on the malicious link that installs malware into their system.
Even though the majority of spoofed emails are easy to spot and can be addressed by simply deleting them, some varieties can have serious consequences.
Reasons for Email Spoofing
The motivations behind email spoofing are simple. Typically, an attacker will use this tactic to acquire sensitive information such as SSNs, financial details, and so on. Many hackers do this for various reasons, but the most common is to obtain access to personal information.
Here are some other reasons for email spoofing:
- Hiding the fake sender’s true identity. One of the main payoffs of email spoofing attacks is that it helps the threat actors to remain anonymous.
- Evading a spam blacklist. Many email service providers enable users to create a spam-filtering blacklist. Adding a spammer’s name or domain address to a filter is one way to stop them. When spoofing an email address, they can use one that is unlikely to be in the filter settings. As a result, the email passes undetected through the filters and goes into the victim’s mailbox.
- Damaging the reputation of the legitimate sender. This is another reason for email spoofing. In some situations, spoofed email messages may be used to make the sender or their company seem vulnerable or impacted by malware or cybercriminals. This may tarnish the sender’s public image, jeopardizing their business or social prospects.
- Planning to do personal harm. In certain cases, the motivation is personal. When email spoofing is successful, the attacker may acquire access to the victim’s computer files, professional contacts, social media accounts, and more. This might make the legitimate sender seem unprofessional, ruin their career, or compromise their device.
Attacks that Use Email Spoofing
Email spoofing is used for malicious activities such as:
- Spear phishing: Spear phishing can be defined as an email spoofing attack that aims to extract sensitive information from a victim using a very specific and personalized message. This email message is usually sent to individuals or companies, and it’s extremely effective because it’s very well planned.
- Business Email Compromise (BEC): Another attack that uses email spoofing is Business Email Compromise (BEC), a type of targeted scam in which an attacker impersonates a company executive or high-level employee with the intent of defrauding or extracting sensitive data from the company or its partners. The end goal of a BEC fraud is to persuade the target to make a money transfer or send confidential information to the attacker while believing they are executing a legitimate and regular business operation.
- CEO fraud: CEO fraud is a particular type of BEC that happens when an employee receives an email message that seems to be from their top boss (or CEO), asking you to do something on their behalf and keep it secret.
- Vendor Email Compromise (VEC): Both BEC and VEC scams are based on social engineering. But what sets them apart is that VEC attacks are targeting a supplier’s customers, who receive what looks like realistic payment requests for an actual service they are expecting to pay for.
- Spamming: Spam is made up of unsolicited emails or other types of messages sent over the Internet.
- Identity theft: Identity theft refers to the process of stealing someone’s personal identification data and using it online in order to pose as that person.
- Man-in-the-Middle (MITM): A man-in-the-middle attack represents a cyberattack in which a malicious player inserts himself into a conversation between two parties, impersonates both of them, and gains access to the information that the two parties are trying to share.
How Email Spoofing Attacks Work
Email spoofing is possible because of limitations in SMTP (Simple Mail Transfer Protocol), a technology responsible for allowing emails to be sent from one person to another.
SMTPs limitation is that it doesn’t verify if the email address in the “From” field is genuine.
Normally, even your computer could act as an SMTP server and send spoofed emails. However, Internet Service Providers have caught on to this tactic, so they block port 25, which is the one responsible for sending emails. But there’s an easy way around this.
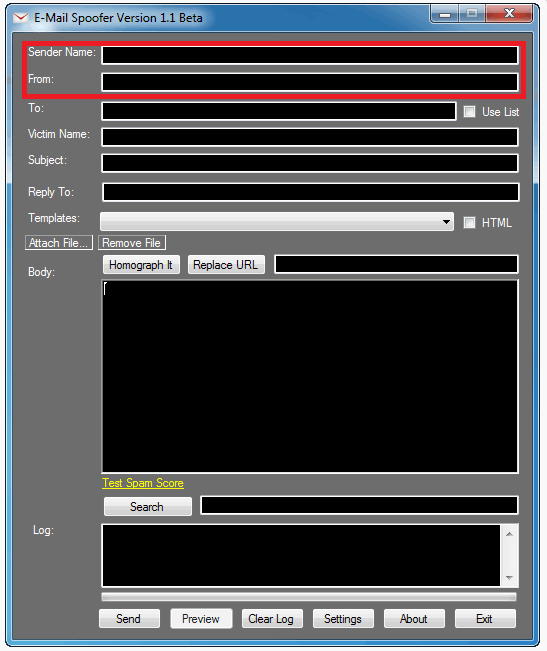
If a malicious hacker wants to spoof an email, all he has to do is use any of the free online Simple Mail Transfer Protocol server services, write up the email, and then type in his desired email address in the “From” field and then click send. Or, he might use a dedicated program for email spoofing.
It doesn’t matter if he doesn’t actually own the email address since the SMTP server won’t bother verifying it.
However, if the person who received the email replied, then the reply would go to the inbox of the real owner of the address, not the malicious hacker. That doesn’t matter much to the spoofer, as long as you click the link or do the action requested in the initial email.
How to Detect Spoofed Emails
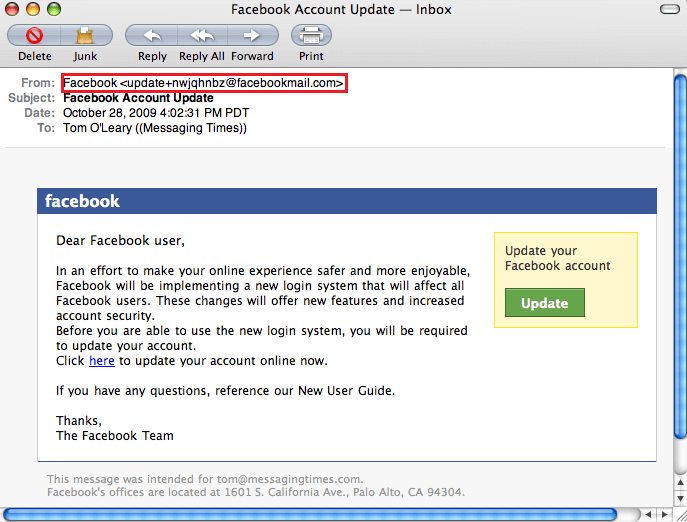
Check the sender’s email address and name
This won’t help every time. But will at least weed out malicious hackers that use a similar email address to the one they attempt to impersonate. For instance, they might use help@faceb00k.com or even stranger derivations.
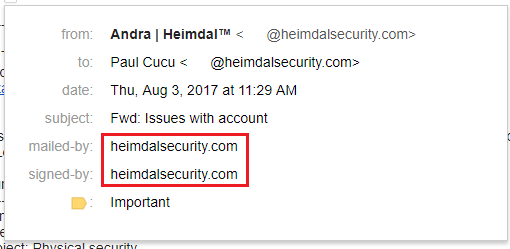
Gmail users can look at send-by, signed-by, and encryption fields
Gmail is a secure email service provider that offers a useful and easy-to-use feature that lets you see if the email is genuine or not. All you have to do is to open up the email, and then click on the dropdown arrow underneath the sender’s name.
Next, look at the mailed-by and signed-by fields. If they are present, then there’s a high chance the email is genuine.
If there’s a mailed-by field, then it means the email was secured using SPF, if there’s a signed-by field, then the email was signed by DKIM. We’ll do a really quick overview of DKIM and SPF a bit later on. Most banks and major companies will go to great lengths to ensure their infrastructure is safe, so they will have these verification methods in place to counteract email spoofing.
Here’s how to check for SPF and DKIM in Yahoo
Yahoo also offers an easy (if not as clean and elegant as Google) to check if an email message is legit, and coming from the real source. First, enter the email that interests you, and then click on the “Actions” button, represented by the 3 dots. Next, click on “View Raw Message”.
Next, you will be taken to a different page that has lots and lots of writing in notepad font. If you can’t find them easily, we suggest you press the search button and look for the following mentions:
For SPF:
For DKIM:
If both these are a “pass”, then the email is legit.
If the request seems strange, send a reply asking for confirmation
This takes advantage of the fact that replies to spoofed emails are sent to the real owner, not the spoofer. Mind you, the email has to be identical to the real one.
For example, the malicious hacker impersonates the email of your good friend Andrew Bob: andrew@company.com. He sends you an email message asking for a $50,000 loan. You know from past experiences that’s actually his real email, so you send him a reply asking if the request is real. This reply goes into Andrew Bob’s inbox and not the spoofers.
If he replies and says yes, you’ll have to think if Andrew Bob can ever hope to repay you $50,000 dollars, or if his account got hacked. If he says he never requested $50,000 dollars from you, then it’s highly likely someone spoofed his email account.
However, if the email address is andrew@c0mpany.com (notice the 0 in “company”), then your reply will land in the malicious hacker’s inbox. For this reason, it’s extremely important to check if the email address is genuine or not.
Don’t fully trust the “From” field
Simply being aware that it’s possible for someone to fake an email address should be enough to make you suspicious of spoofed emails allegedly coming from friends, relatives, or work colleagues.
How to Prevent Email Spoofing
Having someone else spoof your company’s email address is bad for business, either because of losses or brand damage. Fortunately, there are a few measures you can take to prevent email spoofing, even for smaller sites belonging to bloggers or SMBs.
Implement Sender Policy Framework SPF
Short for Sender Policy Framework, SPF checks if the email sender’s domain name (the @gmail.com part) comes from a designated set of servers and IPs that can send emails from that domain.
The SPF will first check the email domain and after that the IP address of the device that sent it. If the sending device wasn’t authorized, then the email failed the SPF check, marking it as “fake”. The email client of the receiver will then read this “fake” marking, and either block the email or send it into the spam folder.
However, if the receiver hasn’t properly set up his email client, he will miss the “fake” sign, and allow the email message to go through.
Setup Domain Keys Identified Mail (DKIM)
This security method will signature stamp emails coming out of your domain with a public key published in the DNS. This signature acts as a seal of proof that the details in the “From” section are legitimate and haven’t been tampered with.
Unfortunately, DKIM has its weaknesses as well. For instance, a malicious attacker can use only the signed part of the email (the “From” section), and then attach malicious content to the unsigned part of the email. He then sends it over to the target. This is basically a classic replay attack.
Implement DMARC, a combination of Sender Policy Framework and Domain Keys Identified Mail
DMARC is short for Domain-based Message Authentication, Reporting and Conformance (yes, it’s a huge mouthful). It aims to combine the best of SPF and DKIM into one single protocol and then adds extra functionality such as monitoring emails, quarantining them, and rejecting messages.
Employee training in cybersecurity awareness
Employee training on email spoofing, like many cybersecurity measures, helps create a shield against cyberattacks that may circumvent technical defenses. It’s essential to invest time in educating your staff on how to distinguish genuine emails from spoofed ones. Then, run additional tests to determine who is still vulnerable to an email spoofing attempt. This will help make sure that all your employees have the information needed to act accordingly if they receive a spoofed email.
Company branding
Email spoofing attacks can also affect your clients. That’s why consistent company branding in your marketing emails is crucial to avoid successful spoofing attacks. When your clients can easily identify a genuine email message from your organization, they will be able to recognize an email spoofing campaign.
Wrapping Up…
An added benefit to implementing the above security features is that email clients will have more trust in your domain. Since you cut down on spammers and impersonators, email providers such as Gmail or Yahoo understand that messages coming out of your domain are the real deal, so there’s a smaller chance of sending them to the spam folder.
Email spoofing is a remarkably efficient approach that more and more threat actors employ in order to gain personal information by impersonating a reputable organization or individual in digital communication. The great news is that there are many actions you can take to help protect your business from email spoofing.
How Can Heimdal® Help You?
Heimdal has developed two email security software aimed against both simple and sophisticated email threats: Heimdal Email Security, which detects and blocks malware, spam emails, malicious URLs, spoofed emails, and phishing attacks, and Heimdal Email Fraud Prevention, a revolutionary email protection system against employee impersonation, fraud attempts – and BEC, in general.
For example, you may want to consider Heimdal Security’s Heimdal Email Fraud Prevention, the ultimate email protection against financial email fraud, C-level executive impersonation, phishing attacks, insider threat attacks, and complex email malware. How does it work? By using over 125 vectors of analysis and being fully supported by threat intelligence, it detects phraseology changes, performs IBAN/Account number scanning, and identifies modified attachments, malicious links, and Man-in-the-Email attacks. Furthermore, it integrates with O365 and any mail filtering solutions and includes live monitoring and alerting 24/7 by our specialists.

Heimdal® Email Security
- Completely secure your infrastructure against email-delivered threats;
- Deep content scanning for malicious attachments and links;
- Block Phishing and man-in-the-email attacks;
- Complete email-based reporting for compliance & auditing requirements;
If you liked this article on email spoofing, follow us on LinkedIn, Twitter, Facebook, and YouTube, for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security