Contents:
A new twist to the classic phishing campaign has been observed in a recent string of emails targeting UK residents, and especially retail and insurance companies in the UK. This new twist claims that the targets have been subpoenaed and summoned to court within the next 14 days, providing a malicious link for details.
Once the curious victim clicks on the link in the fake subpoena phishing campaign, they become infected with Predator the Thief.
Predator the Thief is a particularly nasty info stealer malware, developed by Russian hackers and first discovered in February 2019. Since its initial spotting, Predator the Thief has changed delivery methods a few times, becoming very effective in reaching its targets.
This new fake subpoena phishing campaign targeting the UK is the latest trick up the Predator’s sleeve. After all, most of us can’t remain indifferent to an official-looking invitation to court. What if we’re sued or called to testify? Sadly, we’re compelled to check what it’s all about.
How Does the Fake Subpoena Phishing Campaign Work?
Like most phishing campaigns, this new one also impersonates a trusted brand, partner or institution in order to appear legit. With the victim’s trust earned, the scammers attach a malicious file or link that redirects them to another legitimate-looking portal, where they are asked to log in. The credentials go directly to the hackers, who then use them to steal precious data and assets.

Heimdal® Email Security
- Completely secure your infrastructure against email-delivered threats;
- Deep content scanning for malicious attachments and links;
- Block Phishing and man-in-the-email attacks;
- Complete email-based reporting for compliance & auditing requirements;
Phishing, in general, is a social engineering mechanism, which relies on how convincing it can be and on manipulating emotions (trust, fear, joy) in the victim. In the case of the new fake subpoena phishing campaign, the emotion the hackers are trying to arouse is obviously alert, or fear.
This is how the fake subpoena phishing campaign unfolds.
It starts with a spoofed email modified to look as if it’s coming from the UK Ministry of Justice. The message itself contains little info besides the notice that the victim has been subpoenaed and they need to comply within 14 days. This obviously creates a sense of urgency and panic, which can lead people to click the link without thinking too much.
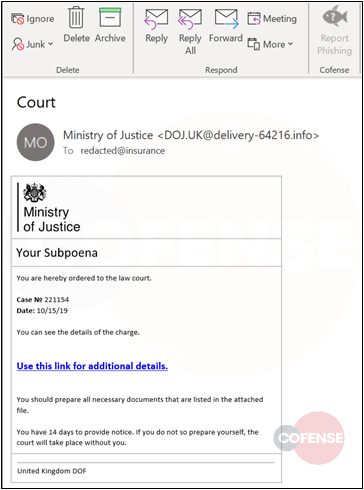
The attackers in the new fake subpoena phishing campaign are also urging the victim to prepare all the documents requested of them in the link. One more incentive to click the malicious link.
Once the victims clicked it, the Predator the Thief malware payload was delivered via a multi-step redirection chain, all pages looking legit. The Cofense researchers who initially discovered the campaign said that the first Word document downloaded by the user is used to execute a first-stage downloader for Predator, silently.
How Does the Infection with Predator the Thief Act on the Infected Device?
After a device becomes infected with Predator the Thief from the fake subpoena phishing campaign, the info stealer starts harnessing.
The Predator the Thief is an exceptionally dangerous stealer, conceived from the start with built-in self-obfuscating mechanisms that conceal part of its code at all times.
What kind of information does Predator steal? This is what researchers have noticed in the current campaign:
- Credentials and other sensitive data;
- Harvesting info from various local and cloud folders;
- All files related to cryptocurrency (all .dat and .wallet Ethereum, Multibit, Electrum, Armory, Bytecoin, and Bitcoin files);
- Cookies from a large list of web browsers (Chrome, Firefox, Filezilla, WinFTP, Steam, and Discord among others – so gamers are also targeted by it);
- Regular screen captures (screenshots).
Once the information has been gathered, it’s packed and sent to the C2 (command and control) server of the malware creators. The data package is sent via HTTP POST requests, alongside fingerprint data and sensitive network configurations.
After the data is sent, the Predator malware cleans up most of the infection’s traces and self-destructs. This makes it particularly difficult to detect and makes post-factum forensics less effective than they are when researching regular malware infections.
Furthermore, the creators of the Predator info stealer market it heavily in a MaaB (Malware as a Business) regime, on Telegram groups. They allow access to their malware for a low price, to anyone interested, along with an easy mode of use and even support when necessary. That means that virtually everyone can buy and use the Predator info stealer regardless of their technical skills.
Still, the people who are deploying it now, in the fake subpoena phishing campaign definitely know what they are doing. The pages look legit through and through and the message is well crafted to induce panic and compliance.
How to Stay Safe from this Phishing Campaign
I’ll end this post on the same note as all our anti-phishing advice. There are three things you can and must do to keep your business and personal data safe from Predator the Thief info stealers and others like it.
#1. Learn more about phishing.
We have several guides on how to recognize phishing and spear-phishing attempts, and there are plenty of other valuable resources online. Take time to read a bit every week and you’ll get better at detecting something amiss. Stay on guard.
#2. Have an active DNS traffic filter to block phishing links.
In today’s threatscape, you can’t be safe with Antivirus alone. You also need a reliable DNS traffic filter, especially if you have a business network to protect. A cutting-edge solution like our Heimdal™ Threat Prevention can block criminal infrastructures before they have time to deliver their payload via infected links.
#3. Stay skeptical and always double-check.
This new fake subpoena phishing campaign wouldn’t be successful if people would take time to investigate before clicking, instead of panicking. Know that phishing gets more and more frequent and creative, so maintain a critical view of everything you receive online.
If you have any doubts about a domain or email or link, you can always send it to us at support@heimdalsecurity.com and we’ll get back to you with a verdict right away. Stay safe!


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










