Contents:
Ransomware is an ever-evolving type of malware created to encrypt files on a device, making any files and the systems that depend on them unsuitable to use. Cybercriminals then request ransom in exchange for decryption. Ransomware attackers usually target and threaten to sell or reveal exfiltrated information or authentication credentials if the victims fail to pay the ransom.
Over the past few years, ransomware attacks have increased significantly and there is no sign of them becoming history anytime soon.
Threat actors keep improving their ransomware strategies all the time, including pressuring victims for payment by threatening to publish stolen sensitive information if they decline to pay, and publicly naming and humiliating victims as secondary forms of blackmail.
The attackers engage in lateral movement to target important data and spread ransomware across entire networks. These malicious actors also increasingly employ methods, such as removing system backups, that make fixing and recovery more difficult or infeasible for affected companies.
It has never been easier to perform ransomware attacks. With Ransomware-as-a-Service (RaaS), threat actors that are not very hi-tech can just purchase ransomware kits on the dark web.
In this article, we will analyze Dharma ransomware, a very dangerous family of ransomware that has been attacking computer users everywhere since its first appearance in 2016.
What Is Dharma Ransomware?
Dharma ransomware, also known as CrySiS is a “trojanized” high-risk ransomware-type virus targeting Windows OP used by threat actors to extort home computer users, but also small and medium-sized organizations.
This type of ransomware targets mostly directories inside the user’s directory on Windows. Every time a file is included in the directory, the ransomware encrypts the file and adds a suffix [bitcoin143@india.com].dharma.
Dharma ransomware’s uniqueness comes from the fact that it doesn’t attack the whole computer, but it conceals inside the system and continues to encrypt files every time they are added to the directory. So, in order to decrypt the files, it needs to be removed.
Dharma ransomware is scattered worldwide via email campaigns that claim to be authentic and the user is requested to download a password-protected attachment named Defender.exe. The whole operation is so successful that many people over the years have ended downloading it.
Dharma Ransomware Operation Mode
In essence, is a self-extracting archive that delivers the malicious file called taskhost.exe together with an old version of ESET AV Remover renamed Defender_nt32_enu.exe.
The minute the extraction is finished, the ESET AV Remover installer automatically starts and makes the user believe that the whole operation is genuine and distracts the victim from seeing Dharma ransomware encrypting the files in the background.
All the files encrypted with Dharma get the extension – . [], there are about 30 extensions, for example, .java, .cesar, .cezar, .wallet, .zzzzz, .dharma, .arrow, .write, .onion, .arrow,. bip, .combo; .brrr; .gamma; .bkp, .like, .gdb, .xxxxx, .AUF, .USA, .xwx, .best, .heets, .adobe, .btc, .pdf .qwex, .eth, .air, .888, .amber, .frend, .KARLS, .aqva, .aye, .korea, .plomb, .NWA, .azero, .bk66, .stun, .monro, .funny, .vanss, .betta, .waifu, .bgtx, .tron .
Unlike its previous version, Dharma ransomware doesn’t modify the desktop background, but generates a text file (“README.txt” or “Document.txt.[amagnus@india.com].zzzzz“) and places it in each folder that includes the affected files.
Once the Dharma ransomware successfully encrypts all valuable data on the attacked system, it drops a ransom message for the victim providing two email addresses the victim can utilize to contact the criminals and make the payment. In order to receive help, users have to contact Dharma’s developers through bitcoin143@india.com email address.
Dharma encrypts files using asymmetric algorithms and, therefore, public and private (decryption) keys are generated during the process. The private key is stored on a remote server controlled by the developers.
It would be impossible for the victims to decrypt files without this key therefore they are asked to pay a ransom. At the moment, files encrypted by Dharma ransomware can’t be manually restored since there are no tools that can perform this action.
The only solution for those affected is to restore their files/system from a backup.
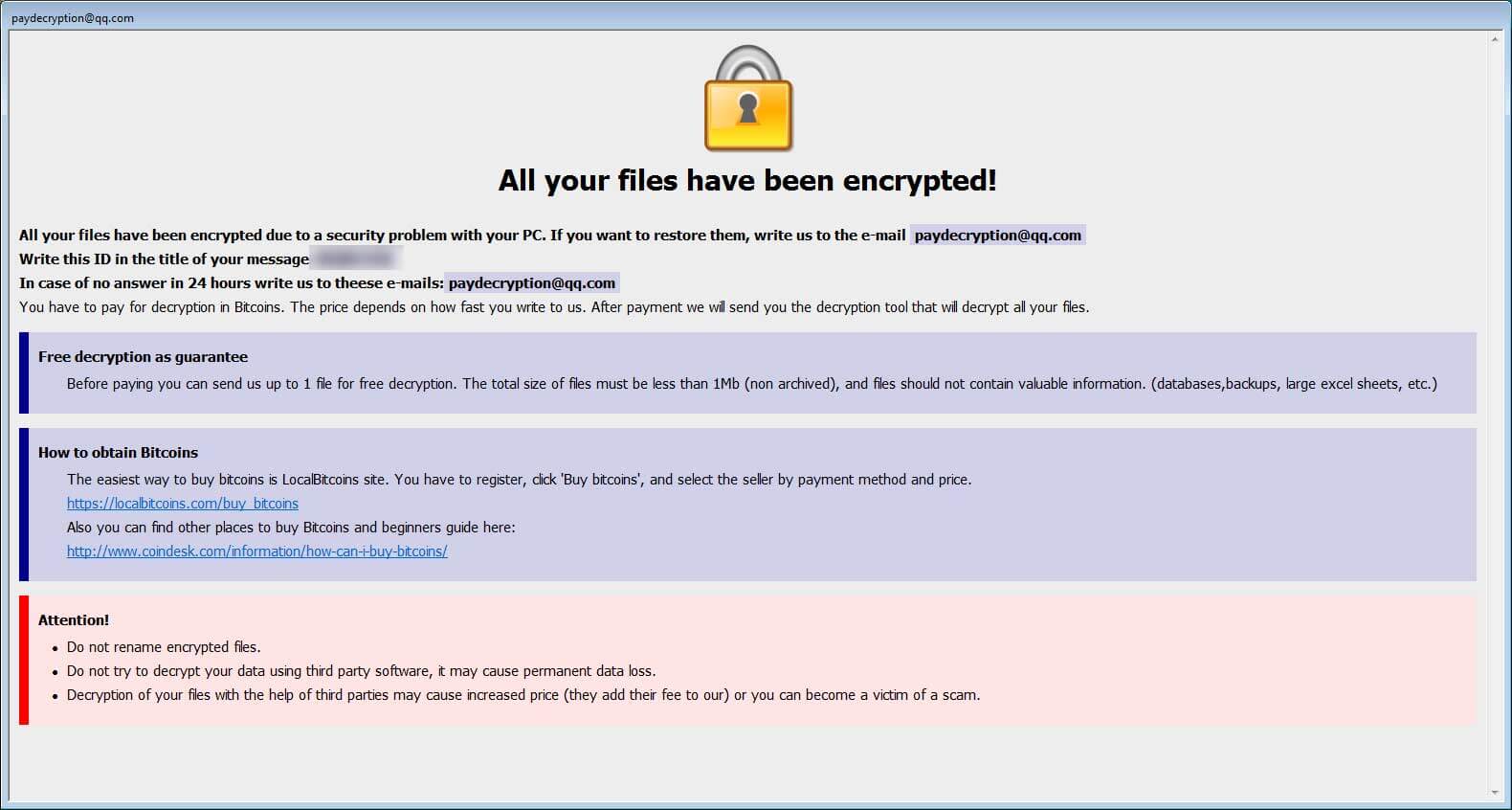
The malware operators are known to demand 1 Bitcoin per infected computer. Financial organizations frequently have to pay bigger ransomware though.
It is not recommended to pay the ransom because Dharma operators are not very reliable when it comes to fulfilling their part of the arrangement following the victim’s payment, many times failing to provide the decryption tools.
Dharma Ransomware – Methods Of Distribution
- Dharma ransomware is dispersed as malicious attachments in spam emails. The employment of malicious attachments that utilize double file extensions is a particular feature of this ransomware family, which under default Windows settings may seem to be non-executable when they actually are.
- Dharma ransomware can also be concealed in installation files for authentic software. Ransomware actors will suggest these installers that appear to be inoffensive for different authorized apps as downloadable executables.
- The main infection vector remains Remote Desktop Protocol (RDP) data that is frail enough to be hacked or just published online. The ransomware can be installed by a human criminal by utilizing brute-force cyber assaults on 3389 port.
How To Stay Safe From Dharma Ransomware
The newest Dharma (CrySis) ransomware strains do not have decryption tools available so, in this case, prevention beats the cure. For online safety, we recommend you follow these anti-ransomware security measures:
- Always backup your data in multiple locations. Use external sources such as a hard drive or in the cloud (Google Drive, Dropbox, etc.) to store it. Our guide will show you how to do it;
- Always keep your software upgraded to its latest versions, as malware and ransomware usually targets outdated programs and apps.
- Keep strong passwords for any account you use, either personal or in a business setting. At an enterprise level, Dharma ransomware can compromise an endpoint through brute-force attacks in order to gain access and execute the malicious file.
- DO NOT open spam emails or download or copy attachments, links, or files from unknown sources that could infect your computer;
- For protection from common ransomware strains, consider using multiple security layers. Antivirus should be the base but you should also have proactive, anti-malware security solutions with behavioral analysis. Your browser should have protections like adblockers in place.
- Given the rise of new types of malware, we remind you that security is not just about using all the latest security tools, it’s also about getting educated so you can better spot suspicious activity. These free educational resources can help you gain more knowledge in the cybersecurity field;
- In case you do get infected with ransomware (Dharma or other files), before attempting decryption duplicate your encrypted files and keep a copy safe. That way, if a ransomware decryption tool becomes available in the future, you can eventually restore your files.
- Lastly, never pay the ransom. As you can see, there is no guarantee and almost no chance to recover your data.
There are a lot of impediments in sorting out problems with encoders viruses, that’s why it is important to keep proper and trustworthy anti-ransomware software on your computer and keep Windows and browser-related components such as Java and Adobe updated.
Keep your browser clean of junk toolbars and add-ons to stop adware attacks that could cause malware infections. Be aware of unexpected email attachments and spam all the time. Also, it is essential to have a good backup system in place, just in case your PC does become infected and you can’t recover your files.
Staying secure from ransomware is easier with the correct knowledge and habits, as well as a trustworthy portfolio of solutions. As always, Heimdal Security is available to assist you with the latter. You can always contact us at sales.inquiries@heimdalsecurity.com or book a demo if you have any questions regarding which of our company’s products are most suited for your needs.

Heimdal™ Ransomware Encryption Protection
- Blocks any unauthorized encryption attempts;
- Detects ransomware regardless of signature;
- Universal compatibility with any cybersecurity solution;
- Full audit trail with stunning graphics;










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security








