Contents:
Heimdal® has recently discovered what can very well be the debut of a massive phishing campaign unfolding in the Nordics. According to a tip sent to us by an anonymous reader, the APT’s choice in phishing is an email in which the victim is informed about the status of an unclaimed postal package. Further analysis indicates that the PostNord DK website is being used at the forefront for the newly detected phishing campaign. Part of the PostNord Group which encompasses the Swedish Posten AB, PostNord DK offers basic postal and packet-tracking services to Danish customers.
The Facts in the Case of the PostNord DK Phishing Campaign
Acting on a note received from an anonymous party, Heimdal® has launched an investigation into the latest phishing action. This operation, although fairly new in cyberspace, shares many of the characteristics identified by Heimdal® in previous, Nordics-centric, smishing cases. For instance, in the Nordea Bank smishing operation, the APT would send the user a message with instructions on how to update the MitID authentication app; both wording and formatting appear to be congruous to the ops. Another example would be the recently covered Posta Romana smishing campaign, whereupon the customer is prompted to update the shipping address via a cloned form.
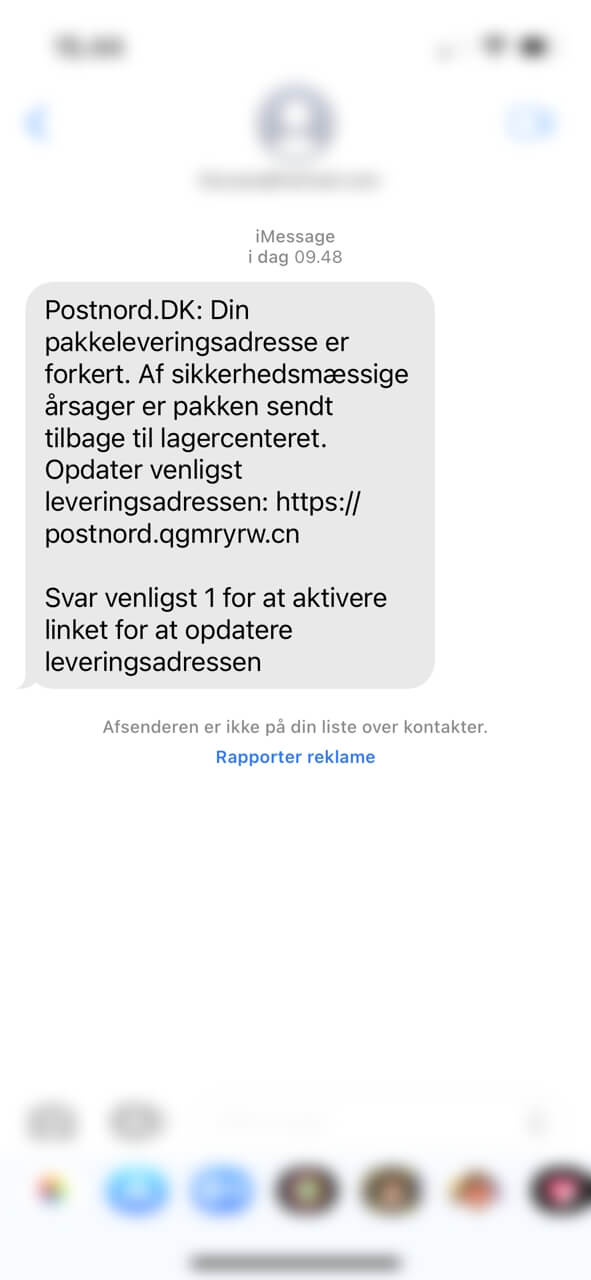
The PostNord DK phishing campaign has a similar mechanism. Novelty-wise, this operation features a unique interactive mechanism – upon receipt, the victim is asked to resend the message with “1” written in the body. Based on the instructions, the update link becomes active only after the user resends the message with the above-mentioned addition. The message has been reproduced below; for confidentiality purposes, we’ve taken the precaution of redacting some fields.
Translated from Danish, the message reads: “Postnord.Dk: Your package delivery address is incorrect. For security reasons, the package has been sent back to the warehouse. Please update the delivery address: [redacted malicious URL]. Please answer 1 to activate the link to update the delivery address.”
Technical analysis
The findings in the case of the PostNord DK phishing campaign can be found below.
URL: https://postnord.qgmryrw.cn.
Domain: qgmryrw.cn.
WHOIS data
- Registered On:2022-09-28
- Expires On:2023-09-28
- Registrant: 吕广阔
- Registrant Contact Email: 2029989126@qq.com
DNS data
- qgmryrw.cn
A 155.94.163.135
NS dns11.hichina.com.
- qgmryrw.cn
A 155.94.163.135
IP Lookup
The website is hosted in the United States of America, most likely in the Los Angeles area.
On that IP was registered an SSL certificated for the following domains:
- qatarposra.com;
- qatarposre.com;
- qatarposrt.com;
- qatarposru.com.
A VirusTotal query reveals that at least one is marked as malicious, and was probably used in a phishing campaign against Qatar Post. Other domains using the same IP . The list can be found below.
- cajkg.xyz;
- gqlms.xyz;
- haidkli.cn;
- higxazk.cn
- isxre.xyz;
- nczxadq.cn;
- nngfr.xyz;
- oftgjbz.cn;
- ogzdr.xyz;
- rdpijtq.cn;
- rhncb.xyz;
- tolkldo.cn;
- tqvfhbq.cn;
- wotpfvt.cn/
Most of them use a hichina.com name server and were registered on the same day, 28.09.2022, which leads us to the conclusion that they are part of the same campaign.
Preliminaries
After consulting open-source intelligence, we found some more domains pointing to that IP. Please consult the list below.
- rdpijtq.cn – involved in phishing campaign for Saudi Post.
- tolkldo.cn – involved in phishing campaign for PostNord.
- whghwth.cn – involved in phishing campaign for Posti, a delivery company in the Nordics.
- wotpfvt.cn – involved in phishing campaign for Qatar Post.
- cajkg.xyz – involved in phishing campaign for Taiwan Post.
- my-aeions.gqlms.xyz – possible phishing for a Malaysian food delivery company.
- ogzdr.xyz – phishing for Romanian Post.
- ubqkt.xyz – involved in phishing campaign Posten, a Norwegian postal service.
Update
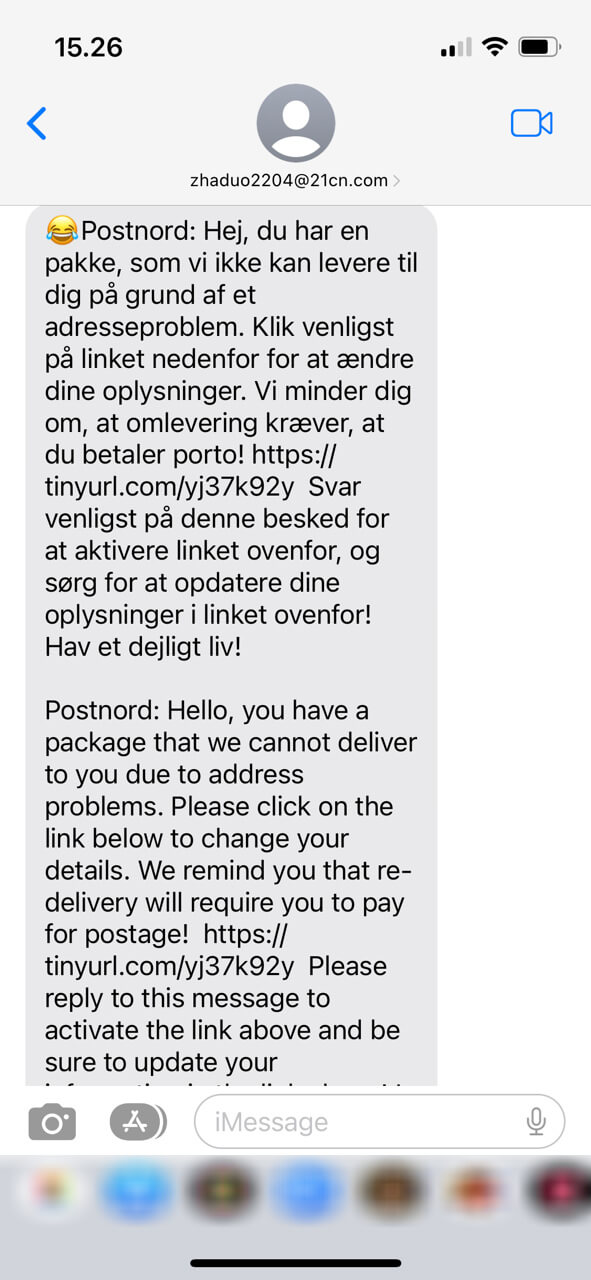
On the 15th of June, Heimdal® received yet another anonymous tip about the ongoing PostNord phishing attempt. Our analysis has unearthed additional information regarding the threat actor behind these attacks. The findings have been summarized below. We’ve also enclosed the message received from the attacker.
Original URL: https://tinyurl.com/yj37k92y
The attacker used an URL shortener service to hide the final domain
Redirects to: postnord.user-dk.xyz
Fails with the error “Too many redirects“
Main domain: user-dk.xyz
WHOIS data:
Registered at: ALIBABA.COM SINGAPORE
Registered On: 2023-06-10
Expires On: 2024-06-10
Additional information:
Organization: Selina Mavuso
State: Gauteng
Country: ZA (South Africa)
The personal details of the registrant are not hidden which leads up to conclude that the attacker might not have taken the necessary steps to reduce online footprint or the supplied data might be fake
DNS data:
A records: 172.67.136.178
A records: 104.21.56.208
The domain is hosted on Cloudflare
Conclusions
Analyzing the APT’s targets, we can see that all of them are delivery services. Most likely the victims are presented with a website stating that they have a pending delivery and can get it by paying a small fee, at which point the attacker gets the card details. The targets are spread around the globe, from East Asia to Saudi Arabia to Nordic Europe; The domains were registered in bulk more than 6 months ago. Based on these arguments, it’s most likely that the operation was done by an organized group, instead of a single individual.
Anti-phishing Cybersecurity Tips
Below, you will find a short, but comprehensive list of tips on how to guard yourself against phishing and smishing attempts.
Avoid opening suspicious-looking links
Bear in mind that some messages you may come across are not malicious, even though they contain links. However, this doesn’t mean that you should follow through, in spite of the incentive. If you do open a link via SMS, make sure it has the HTTPS certificate – check for the padlock icon next to the link.
Use Tracking Features When Available
Most online resellers or, in this case, the postal service operator, allow accountholders to track down their orders in real-time. So, if you come across this type of message, head to your account to check its status. Alternatively, you can always contact the support center for additional information or clarifications.
Stay in Touch with Your Postal Service
When ordering something via Post, you’re usually notified of any delivery changes via phone, mail, or in some instances, by physical notes. Always remember – when in doubt, check your official account, contact support or, if available, call the courier service that handles your delivery.
This article has been written in collaboration with Eugeniu Cernei, Machine Learning Engineer at Heimdal®.
If you liked this article, follow us on LinkedIn, Twitter, Facebook and YouTube, for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security