Contents:
On the 28th of April, acting on a tip received from an anonymous source, Heimdal®’s SOC team has come across an active phishing campaign that appears to specifically target Romanian telecom customers. The preliminary analysis of all of the evidence presented so far has indicated that the threat actor(s) involved in this operation exhibit the same modus operandi observed by Heimdal® in mid-February while investigating the Romanian National Post smishing campaign. At this point in time, it’s difficult to ascertain whether or not the group is behind both attacks.
The Facts in the Case of the Romanian National Post Office Phishing Attack – A Reprise
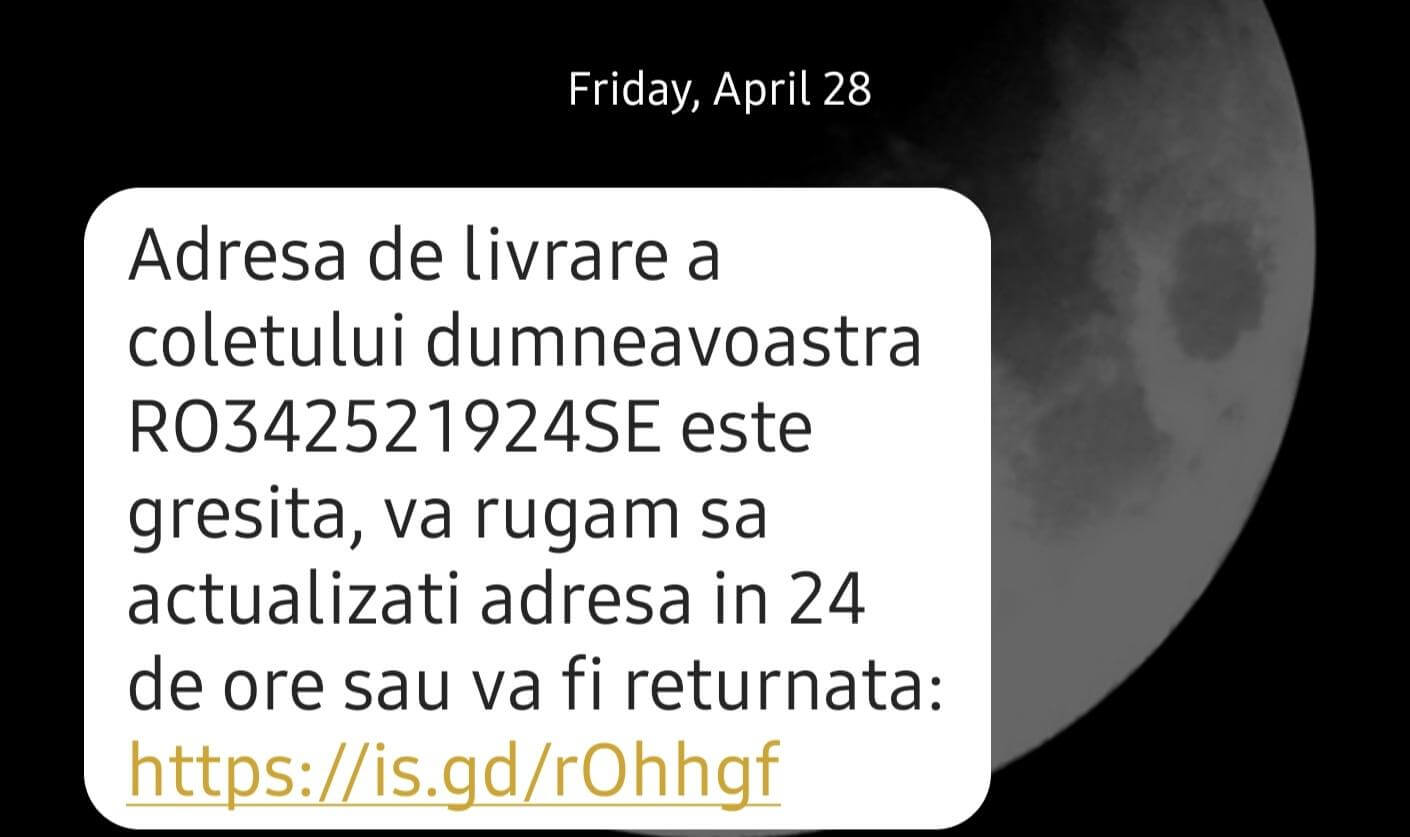
As stated in the introduction, the latest phishing campaign presents many of the characteristics previously described in the above-mentioned case. In both instances, the threat actor has employed SMS to establish a rapport with his potential victims. Furthermore, both message bodies contained TinyURLs that were engineered to redirect the victim to a cloned version of the Romanian National Post’s official website, more specifically, to the section that contains the payment forms. In this case, the user would be informed that the previously specified delivery address is invalid and that he or she is required to update the address in order to receive the package. Below is a snapshot of the URL-carrying message.
Translated from Romanian, it reads: “The delivery address for your package RO342521924SE is not valid, please update your delivery address in 24 hours or the package will be returned.”
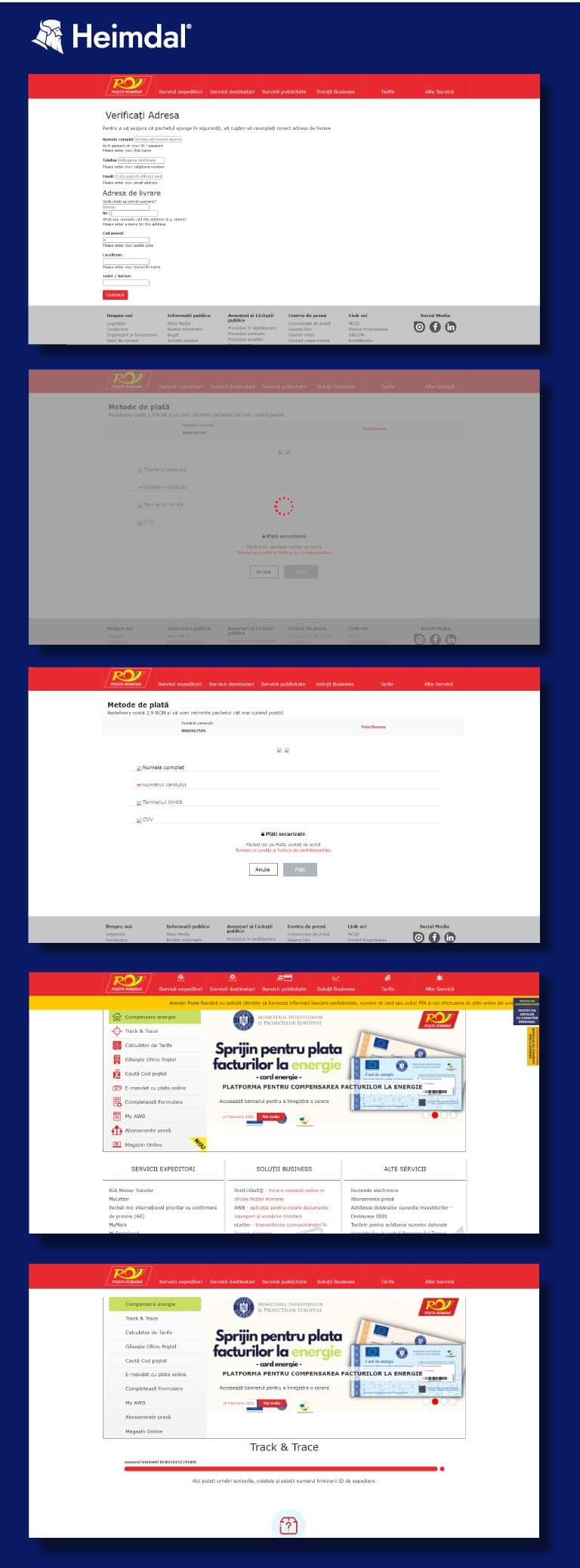
On user interaction, the TinyURL would have been opened up in the phone’s default browser where it would fetch a cloned version of Posta Romana’s payment form for outstanding packages. The user is then instructed to input credit card information into the appropriate fields in order to pay out a tax associated with the address-updating process. Several tests performed on the cloned page have returned varying results. During the first attempt, the page would return a 403-error following detail submission. On the second run, we were redirected to a blank page with no indications whatsoever that the resource was associated with the official website. For safety purposes, Heimdal® has taken the precaution of blocking the malicious URL. The entire phishing flow is presented below.
Technical Analysis
Digital forensics analysis has uncovered the following facts.
First line attack URL
URL: https://is.gd/rOhhgf
Domain: is.gd
The above is an URL shortener. Although not malicious by nature, it’s often used by malicious actors to hide the real URL. It will redirect the user to http://poste-rornana.cc/, domain poste-rornana.cc.
WHOIS records
Registered On: namesilo.com
Expires On: 2024-04-25
Registered On: 2023-04-25
Updated On: 2023-04-26
The attack domain appears to be fresh, but has already been blocked by both Google and Microsoft.
DNS Records
A 46.17.43.174
NS ns1.dnsowl.com
Based on the IP, the domain serves its content from a datacenter in Moscow. Oftentimes, the website returns 403 denied, which would indicate that it works on specific hours or is manually enabled by the attacker. The website is a clone of the main page of posta-romana.ro official webpage. Further analysis reveals that it was written in PHP and hosted on an nginx server.
As for the author, our analysis indicates that it serves two functions – /ipstatus.php and /visiter.php.
- /ipstatus.php decides if to keep the user on this page or redirect to https://www.vodacom.co.za/ , based on a banned IP list. The vodacom.co.za domain appears to be clean.
- /visiter.php is used to store the users’ IP addresses.
The main goal is to get users information, by convincing them that they have a unclaimed delivery that requires more details to be delivered.
After filling the required data the user is redirected to https://poste-rornana.cc/page4.php , where the attacker attempts to get the financial information. Moreover, the same page will try to fetch some graphics from ceshi3.iqakdie.com (e.g. https://ceshi3.iqakdie.com/images/MasterCard.svg). We have concluded that both websites are part of the same phishing campaign.After filling in the card info the page sends them to /page4.php, shows a loading screen and stops working; goal complete.
Additional Information
The first domain has ties https://ceshi3.iqakdie.com. See registrar info below.
Registered On: namesilo.com
Registered On: 2023-04-16
Expires On: 2024-04-16
Updated On: 2023-04-16
The domain is also fresh, but a few days older than poste-rornana.cc. See DNS records below.
DNS Records
For iqakdie.com:
A 91.195.240.123
Based on the IP, the domain serves its content from a datacenter in Germany, Köln. The ceshi3.iqakdie.com domain serves its content from a datacenter (hostwinds.com) based in USA, Seattle.
Preliminaries
- Overall the quality of indicates an entry-level threat actor.
- There is no form validation (i.e., you can send the user info form empty, only the card page has some field verifications).
- The original website is not fully cloned, only the main page is functional.
- The attacker-added JavaScript is not obfuscated and still has console.log lines.
This is an ongoing Heimdal® investigation. We will update this article as soon as more information becomes available.
Anti-phishing Cybersecurity Tips
Below, you will find a short, but comprehensive list of tips on how to guard yourself against phishing and smishing attempts.
Avoid opening suspicious-looking links
Bear in mind that some Google ads you may come across are not malicious. However, this doesn’t mean that you should open everyone, just because the item looks interesting or was on your Wishlist (those can be tracked across apps and platforms). If you do open a link via SMS, make sure it has the HTTPS certificate – check for the padlock icon next to the link.
Use Tracking Features When Available
Most online resellers allow users to track down their orders in real time. So, if you come across this type of message, hop on the reseller’s app and double-check the status of your package. Alternatively, you can always contact the reseller’s support center for additional information.
Follow the rule of the thumb
When ordering something through the Romanian Postal Services, you’re usually notified of any delivery changes via phone, mail, or even physical notes. If you have a Posta Romana account, it would be a good idea to log in and check the status of your order.
This article has been written in collaboration with Eugeniu Cernei, Machine Learning Engineer at Heimdal®.
If you liked this article, follow us on LinkedIn, Twitter, Facebook and YouTube, for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security