Contents:
Heimdal™ Security, among other cybersecurity providers, has recently detected a phishing campaign that specifically targets Fan Courier business customers located in Romania. Several companies have reported receiving fraudulent Fan Courier-signed invoices requesting payments for fictitious orders. All the payment request emails originated from a fake Fan Courier address and contained malicious attachments masquerading as .pdf attachments. The malicious endeavor was nicknamed the Fan Courier phishing campaign.
Detailing the Incident
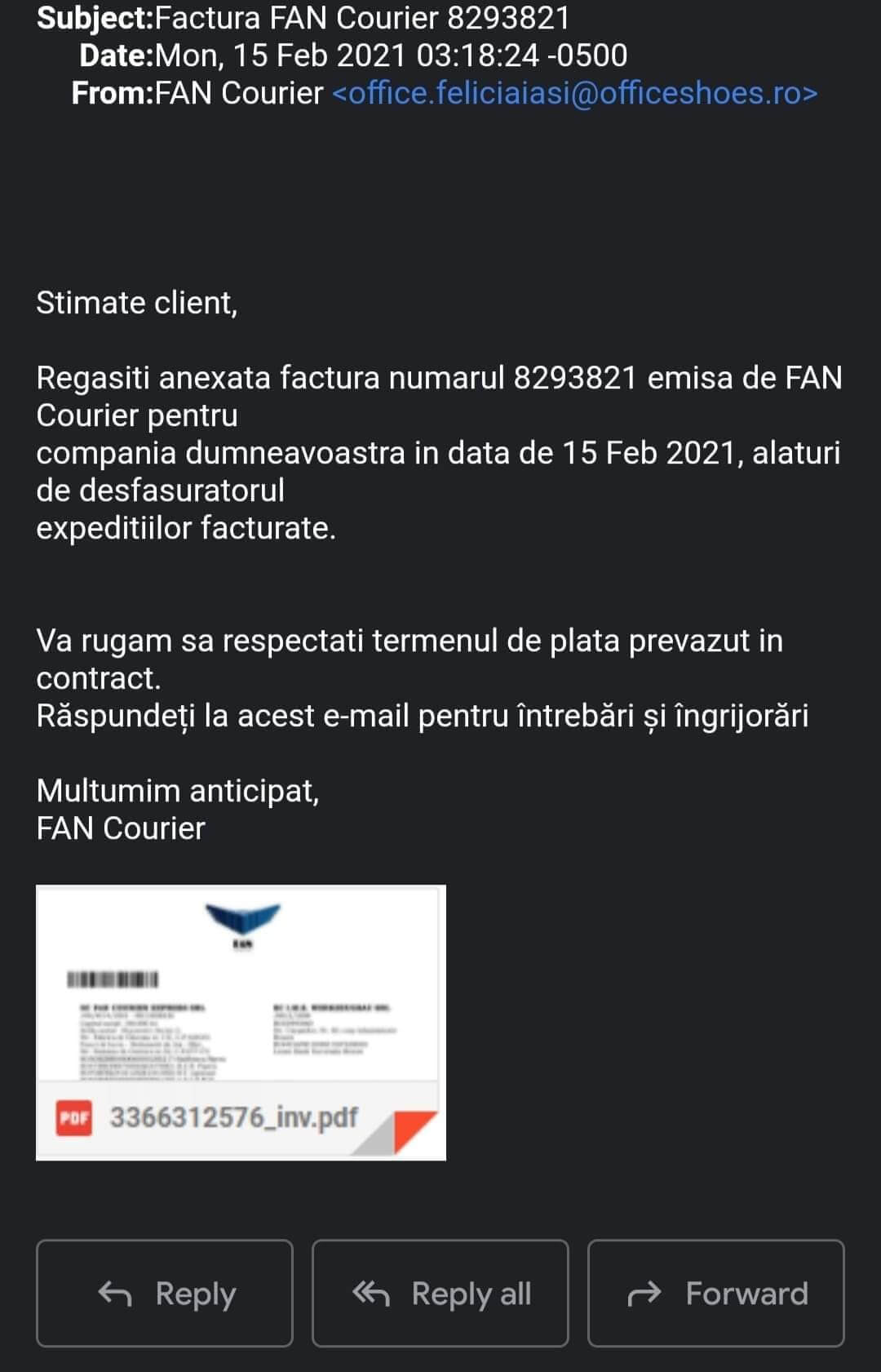
On the 15th of February, several of our B2B customers have sent us notes on what appeared to invoice requests from Fan Courier. At first glance, these emailed requests, which were mostly inboxed by company-issued emails addressed – some have been transmitted on personal email addresses – did not disclose any of the elements associated with phishing campaigns (i.e., spelling issues, grammatical inconsistencies, the overall feeling of urgency, redirectional links and so on). However, on closer inspection, our team has discovered that in all instances, the sender’s field did not match Fan Courier’s official emailing address. In the first case, the email was sent from dough RO TLD (please see attached print-screen with translation),
Translated from Romanian:
Dear Client,
You can find attached invoice number 8293821 issued by Fan Courier for your company on February 15, 2021, together with the description of the goods and services of the invoiced shipments.
Please respect the payment term provided in the contract. Reply to this email for questions and concerns.
Thank you in advance,
Fan Courier.
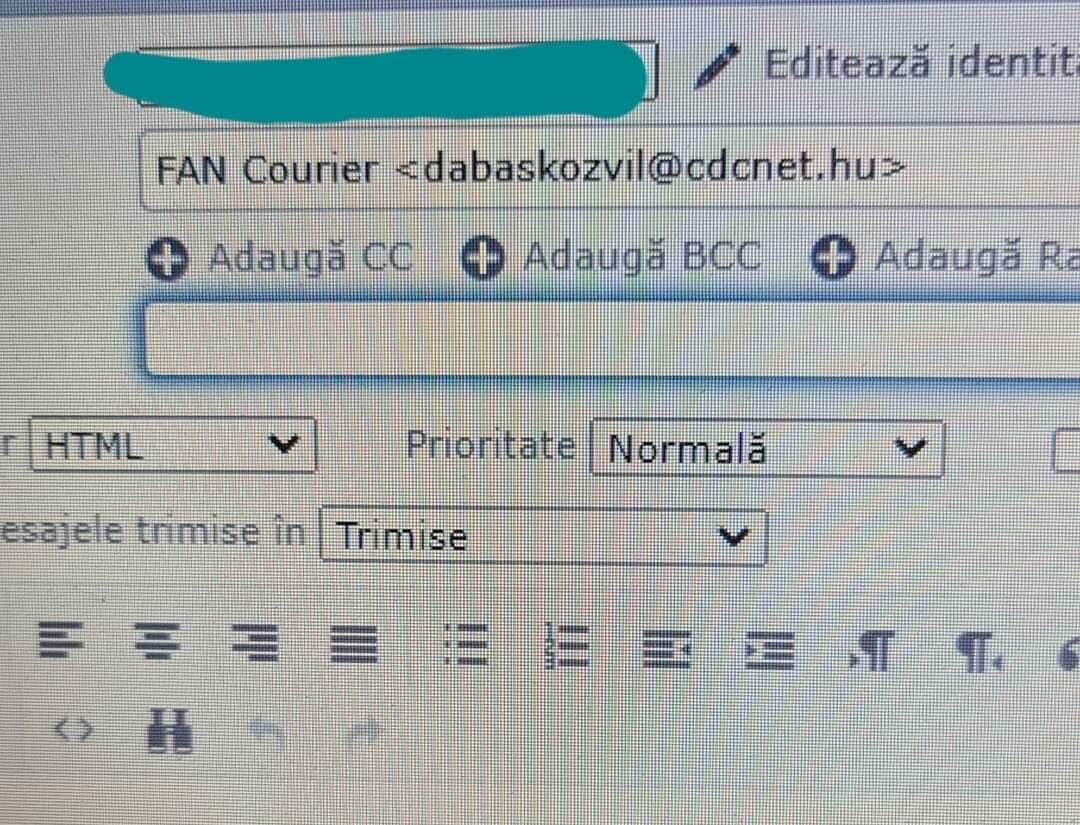
In the second case, the crafted email seems to have been sent from a dough HU TLD (see attached print-screen).
Note that all of these inboxed emails contained pseudo-Portable Document Format (.pdf) attachments with a generated invoice-like doc preview. The document attachment’s in question were found to be malicious .exe or .bat executables. Heimdal™ Security’s SOC team confirmed that the executables, which required low-level privileges, would have bypassed normal UAC authentication for the purpose of installing backdoors. The behavioral analysis also suggests that some Fan Courier phishing variants could have been utilized to open the default or user-defined Remote Desktop Port and run PowerShell scripts on the victim’s computer, deploy keyloggers or even unpack trojan-type code.
So far, none of the victims reported financial or data losses. Following the incident, Fan Courier issued a statement on its official website, detailing the incident and steps took to mitigate the incident. According to this statement, Fan Courier’s data center remains intact and no data has been leaked. As a pre-emptive measure, Heimdal™ Security advises its clients not to open email attachments received from Fan Courier if no shipments have been provisioned in the mentioned timeframe.

Heimdal® Email Security
- Completely secure your infrastructure against email-delivered threats;
- Deep content scanning for malicious attachments and links;
- Block Phishing and man-in-the-email attacks;
- Complete email-based reporting for compliance & auditing requirements;
In regards to how the threat actors have managed to acquire the company’s mailing list, right now, the working theory is that one or more of Fan Courier’s partners might have had experienced a data breach sometime during February. Again, I emphasize that the theory on the Fan Courier phishing campaign has yet to be confirmed or refuted.
On mitigating phishing attempts, Heimdal™ Security recommends the following:
- Refrain from opening email attachments received from unconfirmed sources.
- Perform regular data backups.
- Ensure that your security solutions are up-to-date and running.
For complete protection against email phishing, I highly recommend Heimdal™ Security’s Email Security solution – advanced spam filter and with an attachment deep-scanning feature capable of looking inside any type of attachment.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security