Contents:
According to the researchers from Microsoft 365 Defender, the attackers were able to compromise their targets’ mailboxes by using phishing.
What Is BEC Fraud?
BEC Fraud is a scheme used by malicious actors to gain access to legitimate business emails through social engineering or computer intrusion and to impersonate an employee.
Also known as the “man-in-the-email” attack, BEC scams start with a large amount of research, with the attacker going through publicly available information about the company, like websites, press releases, or social media published content.
How Did the Attackers Operate?
By using phishing the attackers managed to exfiltrate sensitive information in emails matching forwarding rules, thus allowing them to obtain access to messages related to financial transactions.
The use of attacker infrastructure hosted in multiple web services allowed the attackers to operate stealthily, characteristic of BEC campaigns.
The attackers performed discrete activities for different IPs and timeframes, making it harder for researchers to correlate seemingly disparate activities as a single operation.
The researchers disclosed the entire attack flow that took place behind a recent BEC incident, from the get-go, when the attackers gained initial access to the victim’s mailboxes to gaining persistence and stealing data using email forwarding rules.
It looks like the login information was stolen by using phishing messages that were redirecting the targets toward landing pages mimicking the Microsoft sign-in pages asking them to enter their passwords under a pre-populated username field.
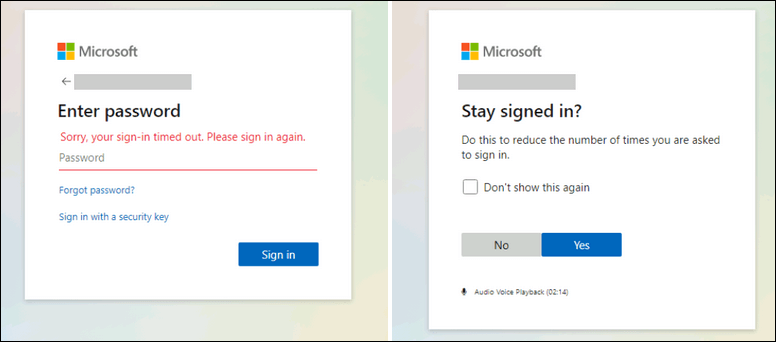
The use of stolen credentials for compromising inboxes is blocked when enabling multi-factor authentication (MFA), but Microsoft found that the attackers have used legacy protocols like IMAP/POP3 to exfil emails and therefore circumvent the MFA on Exchange Online accounts when the targets failed to toggle off legacy auth.
Credentials checks with user-agent “BAV2ROPC”, which is likely a codebase using legacy protocols like IMAP/POP3, against Exchange Online. This results in an ROPC OAuth flow, which returns an “invalid_grant” in case MFA is enabled, so no MFA notification is sent.
The attackers also made use of the cloud-based infrastructure disrupted by Microsoft in order to automate their operations at scale, “including adding the rules, watching and monitoring compromised mailboxes, finding the most valuable victims, and dealing with the forwarded emails.”

Heimdal® Network DNS Security
- No need to deploy it on your endpoints;
- Protects any entry point into the organization, including BYODs;
- Stops even hidden threats using AI and your network traffic log;
- Complete DNS, HTTP and HTTPs protection, HIPS and HIDS;
Microsoft discovered as well the fact that the scammers made use of the BEC activity that originated from multiple IP addresses that belonged to multiple cloud providers, while also making sure that they had set up DNS records that matched with the ones of their victims in order for their malicious activity to easily blend into pre-existing email conversations and therefore evade detection.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security








