Contents:
The ransomware operation known as Rhysida has rapidly gained notoriety, especially following a series of attacks on healthcare organizations. This surge has led to heightened vigilance from government agencies and cybersecurity firms, prompting them to closely monitor Rhysida’s activities.
Growing Influence
The spotlight on Rhysida intensified after the U.S. Department of Health and Human Services (HHS) issued a security bulletin alerting the public to the threat.
The ransomware-as-a-service (RaaS) group that has emerged in May 2023, has first grabbed attention in a month later, when it leaked sensitive documents pilfered from the Chilean Army. Initial analysis by SentinelOne suggested that Rhysida’s ransomware was in early stages of development, lacking standard features seen in most strains, such as persistence mechanisms and Volume Shadow Copy wiping.
Global Reach
While its primary targets included education, government, manufacturing, technology, and managed service provider sectors, recent attacks have expanded to the Healthcare and Public Health (HPH) sector. Notably, Rhysida was responsible for a recent cyberattack on Prospect Medical Holdings, which experienced a system-wide outage affecting 17 hospitals and 166 clinics across the United States.
However, the scale of Rhysida’s activities has reached perilous levels, with victims scattered across Western Europe, North and South America, and Australia. For example, a healthcare institution in Australia found itself listed on Rhysida’s dark web data leak site, given a week to pay the ransom before data leakage.
How Rhysida Operates
According to various reports, the threat group typically initiates attacks through phishing emails, employing Cobalt Strike and PowerShell scripts for lateral movement before deploying the ransomware payload. Notably, Rhysida’s PowerShell scripts actively terminate antivirus processes, delete shadow copies, and modify RDP configurations, suggesting ongoing development and evolution of the ransomware’s functionalities.
According to HHS`s security bulletin, the group employs a ransom note threatening public data distribution, aligning with double-extortion practices. These ransom notes, written as PDFs, are deposited in affected folders on targeted drives, with the document content embedded in the binary in plain text.
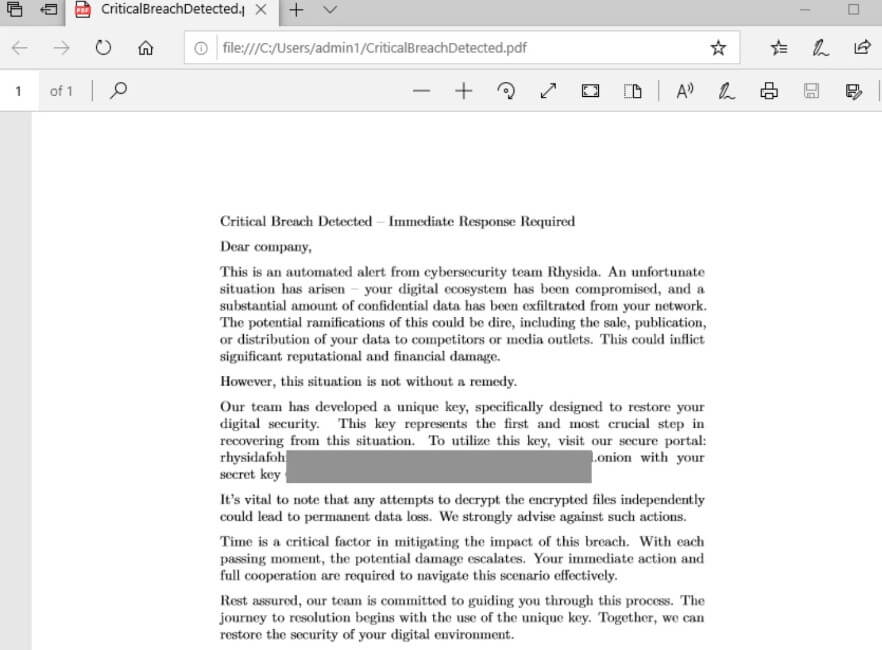
Victims are directed to contact the attackers via a TOR-based portal, using their unique identifier from the ransom note. Rhysida exclusively accepts Bitcoin, offering guidance on its acquisition and use on the victim portal. Once a unique ID is submitted, victims can provide further details like authentication and contact information via an additional form.
The Heimdal® Take
The emergence of Rhysida as a potent ransomware threat, with a particular focus on healthcare and public health sectors, raises significant concerns.
Heightened awareness, robust defenses, and proactive measures are crucial to countering the escalating threat posed by Rhysida and other such threats, as well as their potential implications for various industries.
Heimdal is equipping its clients with an exceptional integrated cybersecurity suite, featuring the Ransomware Encryption Protection module. This module operates entirely without relying on signatures and boasts seamless compatibility with all antivirus solutions, guaranteeing exceptional detection and resolution capabilities for all forms of ransomware, regardless of whether they are fileless or file based.

Heimdal™ Ransomware Encryption Protection
- Blocks any unauthorized encryption attempts;
- Detects ransomware regardless of signature;
- Universal compatibility with any cybersecurity solution;
- Full audit trail with stunning graphics;
Do you work for an NHS Trust? Heimdal is giving you free ransomware licenses to combat growing cyberattacks.
Get your free ransomware protection here.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, and YouTube for more cybersecurity news and topics.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security







