Contents:
Ransomware is hitting more victims even as payouts drop, setting the stage for a 2026 threat landscape defined by high volume and fast-evolving tactics. Explore our 2025 ransomware stats to see the shifts shaping stronger defense priorities in 2026.
Ransomware attacks continue to be a major cybersecurity concern for both large enterprises and small and medium businesses.
In fact, this year’s industry reports on ransomware statistics show that small businesses are even more prone to become victims of this threat.
While more and more organizations started refusing to pay ransom and thus discourage ransomware-as-a-service (RaaS) business models, the overall figures for ransomware attacks impact are still high. Verizon’s Data Breach Investigation Report found a 37% increase
from last year’s report. Their data showed ransomware was present in 44% of all the breaches they reviewed, up from 32%.
So, let’s kick it off with the key ransomware incidents trends!
Key Ransomware Attack Trends
To find out what the ransomware attack trends were this year I checked DBIR 2025, Statista, and ransomware.live, which is a personal project of CTO Julien Mousqueton.
All three sources agree on the following.
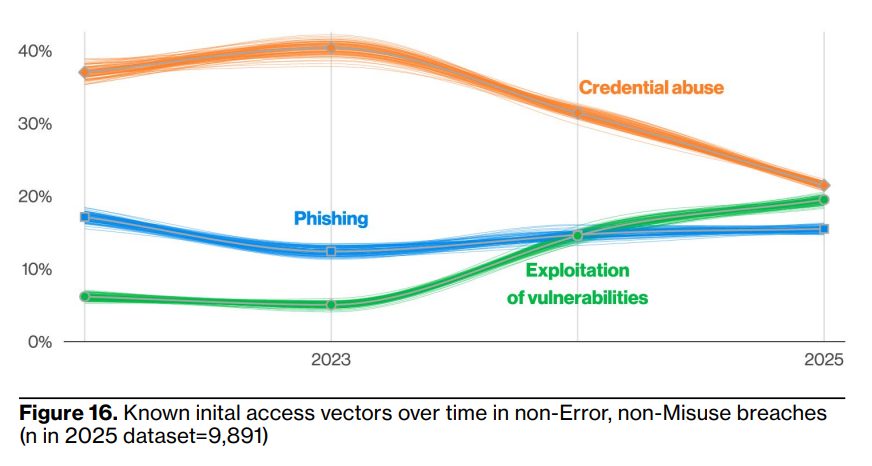
Exploiting vulnerabilities and compromised credentials
Upatched vulnerabilities and zero-days are the number one initial access tactique that ransomware groups use. Using compromised credentials comes second, according to Statista:
- 32% exploited a vulnerability to gain access
- 23% used compromised credentials
- 19% of ransomware incidents had a malicious email as root cause
- 18% started with phishing
- 6% used brute force
DBIR data also point to exploited vulnerabilities and compromised credentials as top root causes of ransomware attacks:
Less victims agree to pay ransom
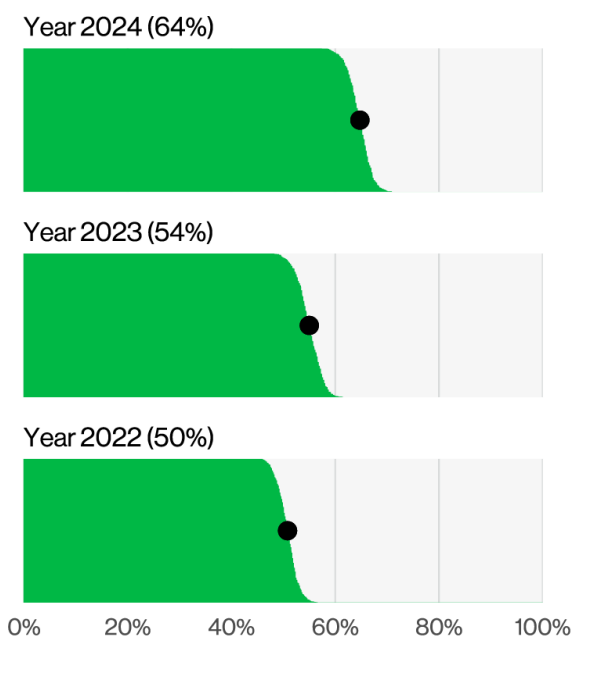
According to DBIR’s numbers, the number of organizations that pay the ransom, thus supporting Ransomware-as-a-Service business models, keeps going down.
Also, the median sum of money paid as ransom dropped. This could mean organizations became aware that prevention measures against ransomware payoff:
- a layered cyber security strategy
- backups
- critical systems redundancy
Double extortion and the lack of control over whether you’ll get your data back or not after paying the hackers could also be a cause of this drop.
However, Statista data say the overall number of ransomware victims keeps rising.
Long story short, here’s what the figures say:
- the median paid ransom decreased with $35,000 from 2023 to 2024
- the highest ransom price also went down, from $9,900,250 in 2023 to $3,637,500 in 2024. This is almost 2 times lower than the 2022 maximum – $7,712,500
- 64% of ransomware victims refused to pay ransom in 2024, which is 10% higher than last year’s results (54%)
- the lowest number of victims year-round for 2023 was 166 (January), while the lowest for 2024, same month, was 286, which is more than double
- the highest number of victims for 2023 was 484 (November), and the lowest for 2024, same month, was 632.
Ransomware hits small and medium businesses harder
It is no secret that smaller businesses have less chances to recover after a ransomware attack. Smaller budgets, less specialized workforce to handle the incident and follow through a recovery plan are among the reasons.
But this year’s DBIR report revealed another facet of SMB’s cybersecurity landscape. While in the case of large enterprises security analysts found ransomware in 39% of the breaches, ransomware was involved in 88% of SMBs reported breaches.
Ransomware is also disproportionally affecting small organizations. In larger organizations, Ransomware is a component of 39% of breaches, while SMBs experienced Ransomware-related breaches to the tune of 88% overall.
Source – DBIR 2025
Most active ransomware groups in 2024 and 2025
Out with the old, in with the new does not always apply in cybercrime, as years go by. Some of the largest ransomware actors in 2024 still rank well in Julien Mousqueton’s ransomware report. His individual project, ransomware.live, monitors and scrapes leak sites to find and list latest ransomware victims.
While most ransomware reports work with a past year’s data, this platform shares almost real time ransomware stats:
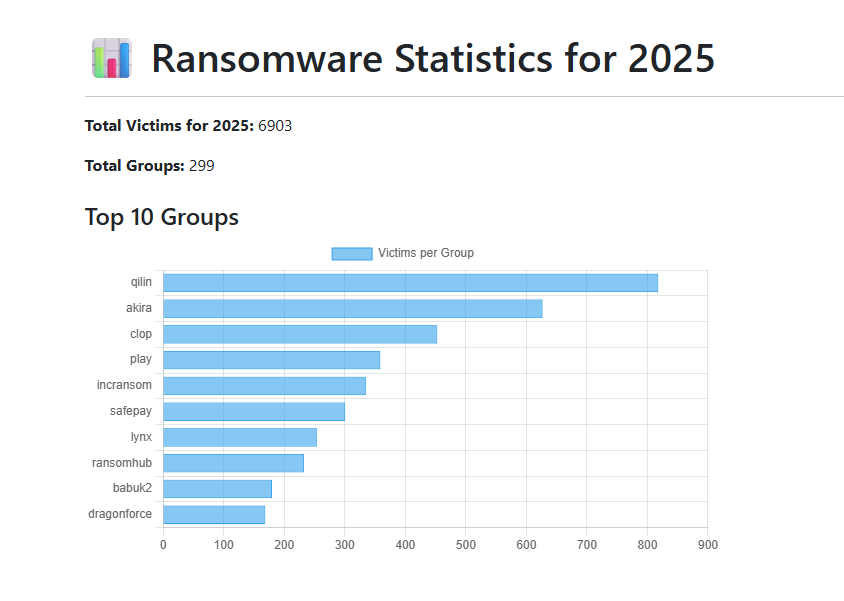
Here’s what it revealed on ransomware attacks worldwide for 2025 (until November):
- the platform spotted 6903 ransomware victims
- attacks were carried on by 299 distinct ransomware groups
- top 5 most active groups were:
- most reported victims for 2025 are based in the US
- 2025 is not over yet, but we can still see there were more victims of ransomware each year and the numbers are growing:
– 6903 in November 2025
– 6129 in 2024
– 5336 in 2023
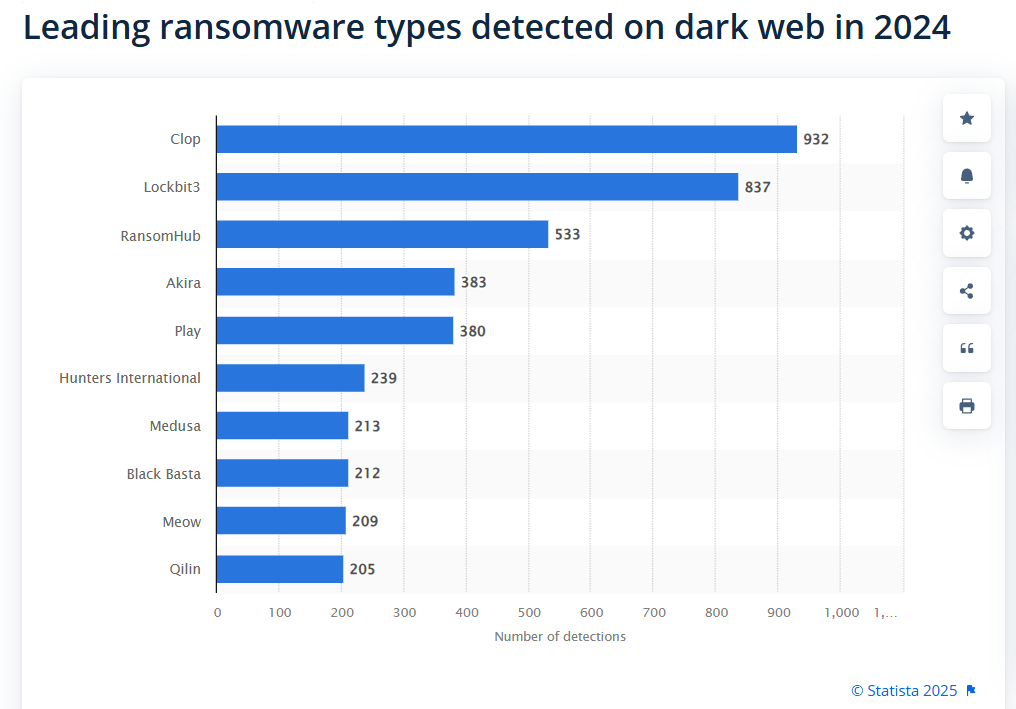
A top 5 most active ransomware threat actors for 2024, according to Statista, puts Clop first:
- Clop ransomware – 932 detections on dark web
- LockBit3 – 837 detections
- RansomHub – 533
- Akira – 383
- Play – 380
Ransomware Statistics by Sector
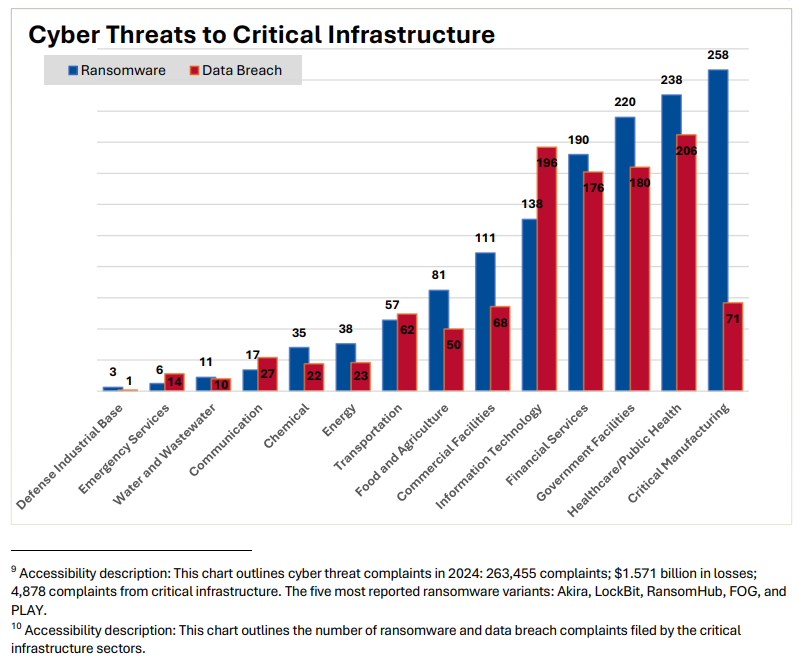
No activity sector is immune to ransomware attacks. IC3’s 2024 chart for cyber threat complaints shows clearly that ransomware was the most often reported threat by the critical
infrastructure sector.
Here’s a top 5 of most ransomware hit sectors in 2024:
Critical manufacturing
The critical manufacturing sector covers industries like metal, railroad, engines, machineries, trains, aircraft production, etc. CISA states that:
A direct attack on or disruption of certain elements of the manufacturing industry could disrupt essential functions at the national level and across multiple critical infrastructure sectors.
During 2024, IC3 registered 258 ransomware attack complaints from the critical manufacturing sector. It was the highest number of complaints for this threat in the report.
Healthcare
With 238 cases, healthcare takes the second place for complaints regarding a ransomware threat.
During the last years, attackers focused more on healthcare organizations, due to both the impact on human lives and low security levels.
In 2024, the largest ransomware attack targeting healthcare was the one that hit Change Healthcare. The threat actors got 192.7 million people were affected by ransomware. (HIPAA report)
Government facilities
This sector includes all sorts of public buildings, from recreational and educational, which are open to public, to embassies, national laboratories, courthouses, etc. Each has specific risk factors, and their well-functioning directly impacts public safety and life quality.
During 2024, the IC3 got 220 ransomware complaints for this area.
Financial services
Banks, insurers, and other financial organizations keep being targeted by ransomware. In their case too, threat actors can rapidly cause operational disruption and expose high-value financial data.
This put the financial sector on the 4th place on IC3‘s chart, with 190 ransomware complaints.
Information technology
Fifth on the list is the information technology sector. In their case, the number of reported data breaches exceeds that of ransomware. It was 196 data breaches to 138 ransomware incidents in 2024.
This sector includes MSPs, software companies, cloud providers, etc. Because many organizations depend on them for core operations, attackers often target IT companies to gain unauthorized access to their customers.
CISA stresses that the IT sector
is central to the nation’s security, economy, public health, and safety, as businesses, governments, academia, and private citizens are increasingly dependent on its functions.
Ransomware Predictions for 2026
Ransomware is still a lucrative business, although more and more victims become reluctant to ransom payment. Those who did enforce prevention measures like securing backups and redundancy for critical systems were able to recover quickly and without paying ransom.
However, there are still plenty of people who decide to pay. So, ransomware families will continue to affect all industries in 2026 and beyond.
Based on available industry reports, here are a few ransomware trends and predictions to keep in mind:
- 54% of the respondents to ISACA’s 2026 Tech Trends & Priorities Pulse Poll say ransomware is one of the most concerning cyber threats for 2026
- Less than 44% of the respondents to the same ISACA survey consider they’re fully prepared to face a ransomware attack
- Ransomware attackers will focus even more on targeting third-party providers and exploiting zero-days, according to Google’s Cybersecurity Forecast 2026.

Heimdal™ Ransomware Encryption Protection
- Blocks any unauthorized encryption attempts;
- Detects ransomware regardless of signature;
- Universal compatibility with any cybersecurity solution;
- Full audit trail with stunning graphics;
How to Protect Your Assets Against Ransomware
First, stick to the three big “don’ts” of cybersecurity best practices:
- don’t downloading content from suspicious web pages.
- don’t open email attachments from senders that are not on your emailing list
- do not click on any links in suspicious emails
You also need to be aware how ransomware spreads, so you can take fast and effective incident response measures.
Keeping your antivirus up to date is another step forward against cybercrime.
On top of all that, to reduce the risk to a minimum, start using an advanced ransomware encryption protection solution.
Heimdal’s XDR platform – version 5.0.5 and beyond – includes a Ransomware Encryption Protection module which is universally compatible with any antivirus solution and 100% signature-free.
Its Kernel mini-filter driver can identify and stop more than 800 ransomware categories through its 4 sub engines:
- Encryption Engine – enables real-time file encryption monitoring to detect if any unauthorized actors are trying to encrypt your data
- Rename Engine – detects suspicious file rename activity, frequently used by ransomware during encryption attacks.
- Volume Shadow Copy Engine – monitors and protects Volume Shadow Copies from deletion to preserve restore points.
- Canary Engine – creates and monitors decoy files to detect unauthorized access.
Book a customized demo and see how Heimdal can protect you from ransomware attacks.
If you liked this article, follow us on LinkedIn, Reddit, X, Facebook, and Youtube.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security








