Contents:
Later this week, proof-of-concept exploit code will be made available for a serious vulnerability in multiple VMware products that permits remote code execution (RCE) without authentication. This pre-auth RCE security hole, identified as CVE-2022-47966, is brought on by the usage of the insecure and out-of-date third-party dependency Apache Santuario.
Successful exploitation of the bug enables threat actors to execute arbitrary code on ManageEngine servers if the SAML-based single-sign-on (SSO) is or was previously enabled at least once before the attack.
The list of vulnerable software includes almost all ManageEngine products.
“Spray and Pray” Attacks Expected by Researchers
Security researchers with Horizon3’s Attack Team announced to admins on Friday that they created a proof-of-concept (PoC) exploit for the vulnerability.
Horizon3 vulnerability researcher James Horseman declared that, being “easy to exploit”, the vulnerability is a good candidate for attackers to “spray and pray” across the Internet.
This vulnerability allows for remote code execution as NT AUTHORITY\SYSTEM, essentially giving an attacker complete control over the system,
James Horseman, Horizon3 (Source)
Attackers are likely to start dumping credentials via LSASS once they have SYSTEM-level access to the endpoint or to use open-source tools to obtain stored application credentials for lateral movement.
Horizon3 researchers also shared a screenshot showing their exploit in action against a vulnerable instance of ManageEngine ServiceDesk Plus. The exploit is set to be released later this week.
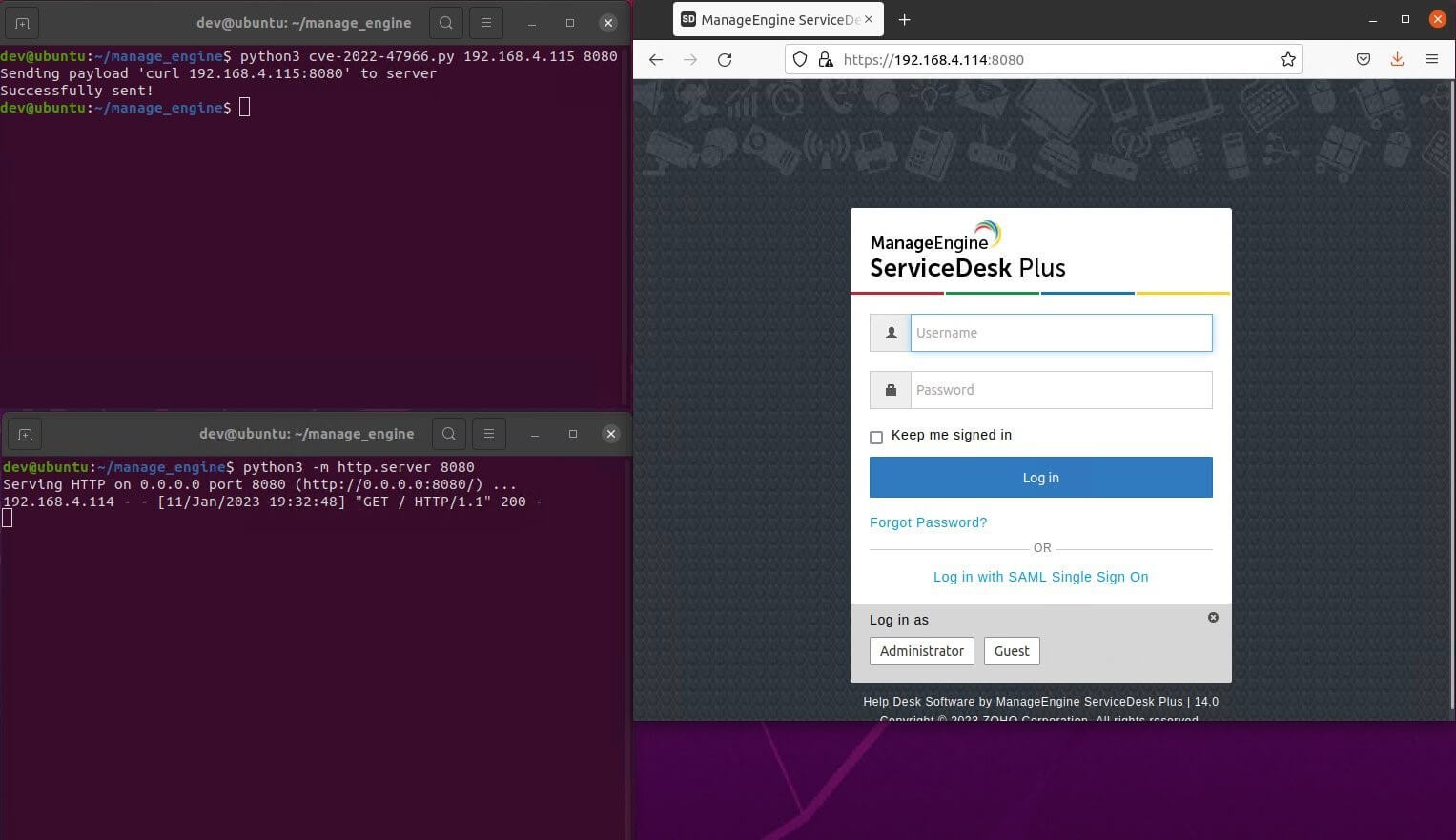
Horizon3’s Exploit in Action (Source: Horizon3)
Horseman discovered thousands of unpatched servers exposed online via Shodan while investigating just two of the vulnerable ManageEngine products, ServiceDesk Plus and Endpoint Central. No attempts to exploit the vulnerability have been identified in the wild so far, but motivated attackers are likely to move quickly to create their own RCE exploits once Horizon3 publishes their PoC code.
As per BleepingComputer, Zoho ManageEngine servers have been under constant attack in recent years, with nation-state hackers using tactics similar to those of the Chinese-linked threat group APT27, targeting them between August and October 2021.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security








