Contents:
When it comes to ransomware, this sophisticated piece of malware that blocks the victim’s access to files until a ransom is paid, Petya ransomware is surely one that has stirred up some nuisances.
What is Petya Ransomware?
Petya ransomware represents a family of ransomware that affects Microsoft Windows-based components. When a computer’s master boot record is infected with Petya, it executes a payload that encrypts data on the hard drive’s systems. Petya can lock up the entire hard drive, preventing the computer from booting up completely.
Short History of Petya Ransomware
Petya ransomware, whose name is a GoldenEye 1995 James Bond movie reference, firstly appeared in 2016, when it used to spread via malicious email attachments.
Petya ransomware became famous in 2017, though, when a new variant, which can be found in the press with the name NotPetya, hit Ukraine. As Microsoft says, in Ukraine “more than 12,500 machines encountered the threat.” They “then observed infections in another 64 countries, including Belgium, Brazil, Germany, Russia, and the United States.”
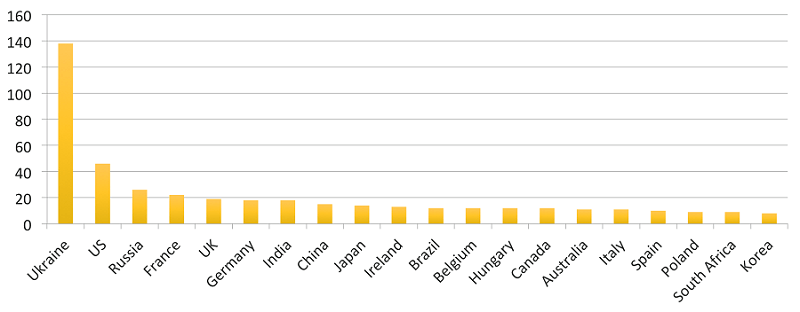
Top 20 countries based on the number of affected organisations
How Does the Petya Ransomware Work?
Petya ransomware encrypts a computer’s Master File Table (MFT), which acts like a quick-reference guide for all the files located on the drive. By being unable to access the MFT, the computer won’t find any files, so it won’t boot up.
After Petya ransomware gets installed on the computer, it proceeds with infecting the Master Boot Record (MBR) – that computer part that loads the operating system when the computer is turned on. The process goes as follows: Petya forces the computer to restart and then the ransom note is displayed while the MFT is being encrypted. The infected computer won’t be able to access anything on its hard drive – not even its operating system.
Petya ransomware usually spreads via email campaigns in which there are various types of attachments – .zip, .exe, .pdf, .pif etc. – or various links to online services. The fake emails pattern upon job offers, job applications or legal proceedings and rely on the user to run the compromised attachments.
Petya ransomware might also propagate itself by exploiting the MS17-010 vulnerability (EternalBlue) or by getting access to credentials and spreading across network shares. EternalBlue “is the name given to a software vulnerability in Microsoft’s Windows operating system” and it works by “exploiting the Microsoft Server Message Block 1.0. The SMB is a network file sharing protocol and <<allows applications on a computer to read and write to files and to request services>> that are on the same network.”
What about NotPetya?
NotPetya exploits the EternalBlue vulnerability and is even more dangerous than Petya ransomware because it permanently encrypts any file it finds. In case of a NotPetya attack, decryption is impossible even if the victim decides to pay the ransom. For this reason, NotPetya can be considered a wiper malware disguised as ransomware.
Victims of the Petya Ransomware
The most famous target of the Petya / NonPetya Ransomware was Ukraine, although similar attacks were reported in Russia, Polland, France, Germany, Italy, United Kingdom, United States and Australia.
The 2017 attack is believed to have “originated from an update of a Ukrainian tax accounting package called MeDoc […], developed by Intellect Service. MeDoc is widely used among tax accountants in Ukraine, and the software was the main option for accounting for other Ukrainian businesses, according to Mikko Hyppönen, a security expert at F-Secure. MeDoc had about 400,000 customers across Ukraine, representing about 90% of the country’s domestic firms and prior to the attack was installed on an estimated 1 million computers in Ukraine.”
On the 27th of June, the day of the attack, a MeDoc update was released – and then the ransomware notes began to appear. Marcus Hutchins, a British malware expert, believes that “the software’s automatic update system was compromised and used to download and run malware rather than updates for the software.”
NotPetya encrypted all the files found on the infected machines and could also intercept passwords and perform administrator-level actions.
Among the institutions that were affected by the $10 billion attack(s) (total damage) there were Ukraine’s Chernobyl Nuclear Power Plant, various Ukrainian ministries, banks and metro systems, as well as the Boryspil International Airport, Ukrposhta and Ukrain Railways.
Outside Ukraine, some of the victims were: the Danish shipping firm Maersk, the Russian oil company Rosneft, the American pharmaceutical giant Merck.
Wrapping Up
Even though ransomware already has a long history and there were thousands of targets around the Globe, it is still one of the most high-profile forms of cyberattack. It’s important to remember that paying the ransom only seems the quickest and easiest way of getting back in business, so you must have some security measures in place in order to avoid an attack in the first place.
Here are some additional ransomware resources that could help.
Heimdal™ Ransomware Encryption Protection










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security









