Contents:
Three things are certain in this world – death, taxes, and networking students have to learn the OSI stack by heart. Despite being the least palatable part of networking, the layered OSI model is vital in understanding how machines communicate with others. So, because there’s nothing more thrilling than going back to the basics, this article will be dedicated to the ‘infamous’ Open Systems Interconnection model. Enjoy and, of course, don’t forget about that subscription button.
What (exactly) is the OSI Model?
As I’ve mentioned in the intro, OSI is an acronym for Open Systems Interconnection – a conceptual model that homogenizes all communication functions of computing or telecommunication systems. To cut a long story short, OSI showcases how computers or other types of systems “talk” to each other. Why is OSI important in or to networking? Because variety is the spice of life, which in this case means that we need to find some sort of ground for inter-device communication – breaking the language barrier if you will.
Since each system has its own technological distinctiveness and works with different telecom protocols, putting it on the line with a system that boasts the same traits may prove to be challenging. This is the very reason we need OSI – to create a universal standard of communication between devices. Think about it for a second: if not for this standard, how would you be able to send an email from a mobile device to a desktop PC or the other way around? Leaving aside the epistemological aspects, we should agree that without OSI, we could wind up with a (digital) Tower of Babel.
Developed during the late ’70, ISO’s OSI model would officially get adopted in the early ‘80s, thus writing the first page in the history of (standardized) computer networking. The need for OSI becomes more obvious – and stringent – with the rapid development of computing networking methods and technologies. For reference, the ‘70s cradled technologies such as Ethernet, LAN, WAN (Wide-Area Networking), Cable TV, Arpanet (precursor to the modern Internet), the TCP/IP model, and, of course, the Worldwide Web. Naturally, the decade that followed brought even more innovations in the field of computer networking. Now, with all these marvelous protocols and technologies in place, we made machines capable of ‘talking’ to each other, but do they speak the same language? The answer is “no” and this is exactly the same consideration that leads to the creation of the OSI model.
With the history lesson over, it’s now time to turn our attention to the model itself. OSI is comprised of 7 interdependent layers or levels, each describing the data’s journey, as it travels from one machine to another. Each level performs specific functions that address data transmission issues such as physical addressing, access control, routing, data reassembly, and more. We’ll get familiar with those later in the article. The OSI levels are as follows:
- Layer 1: Physical.
- Layer 2: Data Link Layer (DLL).
- Layer 3 Network.
- Layer 4: Transport.
- Layer 5: Session.
- Layer 6: Presentation.
- Layer 7: Application.
OSI Layers Explained – Layers, Functions, and Services
1. Physical Layer (Layer 1)
The first OSI level describes the physical medium (environment) required in order to transmit raw, binary data between nodes (i.e., machines). Layer 1 includes components such as cable specs (e.g., thin coaxial, category 3,4,5 twisted pair, fiber-optic), repeaters, network adapters, host bus adapters, network interface controllers, wireless technology, and more. As I’ve mentioned, each layer has its own functions.
In layer one’s case, the functions are Bit Synchronization, Bit Rate Control, Physical Topologies, and Transmission Mode.
Physical Layer Functions
- What is Bit synchronization?
In node-to-node communication, bit streams ‘flow’ between the sender and the receiver; and vice-versa. To ensure that the signal is in perfect sync (i.e., knowing where the signal begins and ends), we use a clock. In more technical parlance, this is called a PLL or Phase Locked Loop.

- What is Bit Rate Control?
Unless you want to end up with a bit deluge during a node-to-node transmission, you’re going to need some kind of rate control mechanism. Layer one’s bit rate control function serves exactly this purpose: dictate how many bits are sent out or received every second.
- What are Physical Topologies?
The physical layer also provides insight into how the various nodes and devices and whatnots are organized in the network. There are two types of network topologies: physical (i.e., describes the network’s physical layout), and logical (i.e., how that network is designed aka the network’s architecture). Since this is quite an extensive topic, I’m just going to name a few of the most familiar network topologies out there. So, for physical network topologies, we have P2P, circular, and mesh. As for logical topologies, we have Bus and Ring.
- What is (the) Transmission Mode?
Layer one also handles the way data is transmitted between nodes. There are three types of transmission notes defined at the physical layer: Simplex, Half-Duplex, and Full-Duplex. Cutting back on the details, simplex means that the communication is unilateral (i.e., the receiver cannot reply to the message sent by the sender), half-duplex means that the action is bilateral, but one at a time (e.g., the sender can reply to the message, but cannot send the reply concomitantly), and, of course, full-duplex means that both the sender and the receiver can receive and send replies at the same time).
2. Layer 2: Data Link Layer (DLL)
The second OSI level is called the Data Link Layer or DLL – not to be mixed up with DLL as in Dynamic-Link Library. DLL helps up figure out how to send the data from one node to another over layer 1 (i.e., physical level). Now that we’ve covered the Physical Layer and moved up to the second one, it’s time to start talking about PDUs or Protocol Data Units. A PDU is protocol-specific single unit information. For instance, layer one deals with bits and symbols, while DLL handles frames – basically, a container for network packets. We’ll talk more about that when we tackle the Network layer.
Because DLL is built on top of the physical layer, its job is to ensure that the data sent from one node actually reaches the other node and, most importantly, that it arrives there without errors. Since the DLL handles everything from transmission to error control, it will require some extra muscle in the form of two sub-layers: LLC (Logical Link Control) and MAC (Medium Access Control). Let’s take a closer look at each of them.
Sub-Layers
- Logical Link Control (LLC)
Being the uppermost DLL sub-layer, one of the LLC’s jobs is to provide a connection between DLL and MAC, the second DLL sub-layer. On top of that, LLC also plays a key role in multiplexing (i.e., merging multiple analog or digital signals into one signal that travels across a shared medium), provides flow control, identifies network layer protocols, and encapsulates them.
- Medium Access Control (MAC)
Medium or Media Access Control (MAC) is the second DLL sub-layer and is responsible for controlling the hardware aspect of machine-to-machine communication. MAC also provides unique tags to Network Interface Controllers (NICs); these identifiers are called MAC addresses and are vital to delivering the data to the right network-connected machine. Here’s a little challenge for you: what’s the main difference between MAC and IP addresses? MACs are used for intra-network communication, while IPs are used in network-to-network communication. Don’t get them mixed up!
Data Link Layer Functions
DLL functions are as follows: Framing, Physical Addressing, Error Control, Flow Control, and Access Control.
- What is Framing?
Framing basically means creating a container for the data transmitted between two devices. A typical DLL frame is composed of four elements: the header, which will contain the source and destination addresses, the payload field, which is the message’s body, the trailer which contains bits used in error detection and adjustment, and the flag which is used to mark the frame’s beginning and end. Don’t forget that frames are DLL’s PDUs.
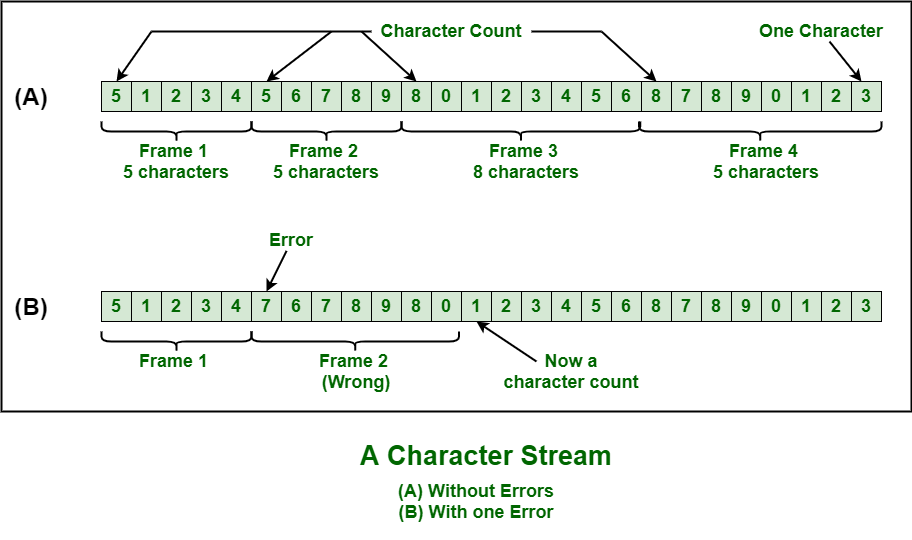
- What is Physical Addressing?
If frames are like envelopes then what should we do to make sure that the letter sent to X actually reaches its intended destination? Writing the correct address on the envelope of course. Now, in networking, the DLL encloses the sender’s/receiver’s MAC address in the frame’s header (see above).
- What is Error Control?
The Data Link Layer provides the means to identify and correct errors that may occur during transmission. If it detects lost or damaged frames, it will automatically retransmit them.
- What is Flow Control?
The law of matter conservation says that what goes in, must come out. The same statement also applies to sent and received data – if too much data gets sent, the message itself might become corrupted. Thus, DLL uses flow control in order to streamline data transmission between nodes.
- What is Access Control?
Here’s a scenario you’re likely to encounter in networking: several devices attempting to communicate over the same channel. How do you solve this conundrum? With access control, of course. MAC, DLL’s second sub-layer, will get to choose which device can exert control over the comm channel at a given time.
3. Network Layer (Layer 3)
Still there? Great! Let’s talk about the third layer of the OSI stack which is called the Network layer. In a nutshell, this layer enables devices located on different networks to talk to each other. Remember MAC, the second sub-layer of DLL? MAC allows machines located on the same network to talk turkey, but can’t do anything about out-of-bounds devices. This is where layer 3 comes into play: using IP addresses (i.e., logical addressing) and packet routing (i.e., packets are the network layer’s PDUs) to ensure that the right message reaches the right party.
Network Layer’s functions are Routing and Logical Addressing.
Functions
- What is Routing?
They say that the shortest distance between two points is a straight line, but that’s not how it works in networking, because, at times, the shortest route may not be viable. To overcome this issue, the network layer uses protocols in order to plot the best route possible.
- What is Logical Addressing?
IP is to (the) Network Layer, as MAC is to (the) Data Link Layer – it allows the system to identify each host connected to the internetwork and to devise an addressing scheme. Similar to physical addressing (see layer 2 for additional information), in logical addressing the sender’ and receiver’s IP addresses will be placed in the header.
4. Transport layer (Layer 4)
Before we talk about the Transport Layer, there’s one thing I’d like to mention – the distinction between media layers and host layers. No, these are not extra OSI layers, but rather another way of looking at the OSI stack. Physical, Data Link and Network are considered media layers because they are hardware-oriented (i.e., every function described so far is handled by hardware). Transport, Session, Presentation, and Application are considered host layers because they are software-oriented. With this in mind, let’s now take a closer look at layer number four.
Servicing the Application Layer (i.e., Layer 7) the Transport Layer – as its name suggests – handles everything related to logistics. This includes end-to-end delivery, acknowledgment of successful data transmission, and flow & error control. On that note, it’s layer four’s ‘job’ to retransmit the data in case the error is found.
Now, since this is a host, software-oriented layer, apart from the regular functions, we also have services.
The Transport Layer’s functions are Segmentation & Reassembly and Service Point Addressing. On the service(s) side we have Connection-Orientated Service and (the) Connectionless Service.
Functions
- What are Segmentation and Reassembly?
Bear with me on this one – in most cases, the message passed between the sender and receiver might be just too big to be transmitted in one bout. So, the Transport Layer uses the Segmentation function in order to break down the message passed down from the Session Layer (Layer 5). The broken-down message is then sent down below to the Transport Layer which, in turn, (re)assembles the message – easy-peasy!
- What is Service Point Addressing?
There are tons of apps and processes that leverage network functions. So, how do you know which one needs to receive the message? With service point addressing, of course – this function enables the transport layer to append a special type of address to the message header. That way, the layer knows exactly where the message must be delivered to. In technical terms, this address is called a service point address, but in the (more) common tongue it goes by the name of port address.
Services
- What is (a) Connection-Orientated Service?
In essence, it’s the transport layer’s (boiled down) version of the TCP/IP Three-Way Handshake. The Connection-oriented service has three phases: connection, data transfer, and disconnection. So, the sender connects with the receiver, the message gets transmitted, and the receiver acknowledges the transport. If everything’s hunky-dory, the connection is terminated.
- What is a Connectionless Service?
Connectionless Services only handle the data transfer part, meaning that the receiver is not required to acknowledge the acceptance of the packet. What’s the difference between the two services? Connection-oriented services are more secure, more reliable, but more sluggish. Instead, Connectionless Service sacrifices reliance and security for speed.
5. Session Layer (Layer 5)
The Session Layer is the second host layer (i.e., software-oriented) and handles things like security, authentication, session maintenance, and, of course, establishment.
Layer 5’s functions are Session Establishment and Termination, Synchronization, and Dialogue Control.
Functions
- What is Session Establishment and Termination?
The session layer tells the two parties (i.e., sender and receiver) how to communicate, and how the communication should be established and ended.
- What is Synchronization?
The Session Layer’s error control mechanism allows a ‘chatty’ process to add checkpoints or flags in the transmission in order to identify (and correct) any inconsistencies along the mark.
- What is Dialogue Control?
Session Layer can ‘force’ a process to transmit in either half-duplex or full-duplex mode.
6. Presentation Layer (Layer 6)
Layer number 6 or the third host level is in charge of translating the info grabbed from the Application Layer (i.e., Layer 7). For this reason, the Presentation Level is also called the Translation Level. Other ‘duties’ include data compression, translation, and encryption/decryption.
The Presentation Layer’s functions are Translation, Encryption/Decryption, and Compression.
Functions
- What is Translation in (the) Presentation Layer?
Ever tried to translate from ASCII to text? Great exercise, but kind of tiresome. The Presentation Layer can do something like that in a heartbeat.
- What is Encryption/ Decryption?
Encryption means using a key to turn plain text into ciphertext and using the same key (or PKI) to decrypt the message. For a crash course in cryptography, be sure to check out my article on PGP encryption.
- What is Compression in (the) Presentation Layer?
The Presentation Layer uses this function to shave off a couple of bits from the message in order to make the transmission smoother.
7. Application Layer (Layer 7)
Also called the Desktop Layer, the Application Layer is the place where we can actually the OSI layers at work. Here you have your favorite apps like browsers and email clients, games, video players, and what-nots.
The functions of the Application layer are Network Virtual Terminal, FTAM (File Transfer Access and Management), Mail Services, and Directory Services.
Functions
- What is a Network Virtual Terminal?
An NVT is an application that allows the user to remotely connect to another host or to a server via software emulation.
- What is FTAM (File Transfer Access and Management)?
FTAM is a protocol that enables users to distribute and manipulate files over the network. Yes, I know you were thinking FTP, but they’re nothing alike. FTAM has broader attributes compared to FTP (e.g., printing & spooling, generating network file systems, and looking up remote database records). Check out the “Big Book of Internet File Transfer RFCsv” by Pete Loshin for more info and clarification.
- What are Mail Services?
This function enables email forwarding and storage in the Application Layer – Outlook can be considered a prime example of Layer 7’s mail service function.
- What are Directory Services?
A Directory Service is an overarching software infrastructure that helps you locate, organize, and manage network resources (e.g., LDAP, DNS, Netware Directory Service, etc.).
Conclusion
And we’ve come to the end of this article on the OSI layers. Hope you’ve enjoyed it and may it aid you in the process of understanding how computer network ticks. Before I take my leave, I wanted to say a couple of words about protocols. Each OSI layer has one or more. What are protocols? A set of rules and guidelines for network communication. I won’t stir the hornet’s nest by deep-diving into that one, but I’m going to round up the most important comm protocols that can be found at each level.
Layer 1 Protocols – RS-232, PON, DSL, Bluetooth, USB, Ethernet, Infrared Data Association, etc.
Layer 2 Protocols – ATM, ARP, MAC, SLIP, L2TP, PLIP, etc.
Layer 3 Protocols – Ipv4, IPv6, ICMP, IPX, PLP, AppleTalk, etc.
Layer 4 Protocols – TCP, UDP, SCTP, DCCP, SPX.
Layer 5 Protocols – NetBIOS, SAP, PPTP, RTP, SOCKS, etc.
Layer 6 Protocols – MIME, XDR, ASN.1, ASCII, PGP.
Layer 7 Protocols – SIP, DNS, FTP, Gopher, HTTP, NFS, SMTP, Telnet, DHCP, etc.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.

Heimdal™ Ransomware Encryption Protection
- Blocks any unauthorized encryption attempts;
- Detects ransomware regardless of signature;
- Universal compatibility with any cybersecurity solution;
- Full audit trail with stunning graphics;










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security







