Contents:
The Federal Bureau of Investigation disrupted a Russian government-controlled Snake malware network that compromised hundreds of computers belonging to NATO-member governments and other Russian targets.
According to the Justice Department, the disruption effort, called Operation MEDUSA, took the malware offline earlier this week.
More About Snake
Wielded by Russia’s Federal Security Service (FSB) and created by a Russian state-sponsored group called Turla (also known as Iron Hunter, Secret Blizzard, SUMMIT, Uroburos, Venomous Bear, and Waterbug), Snake was dubbed the “most sophisticated cyber espionage tool. In at least 50 countries, threat actors have used it to steal sensitive documents from hundreds of devices, including those of NATO member countries, journalists, and research facilities.
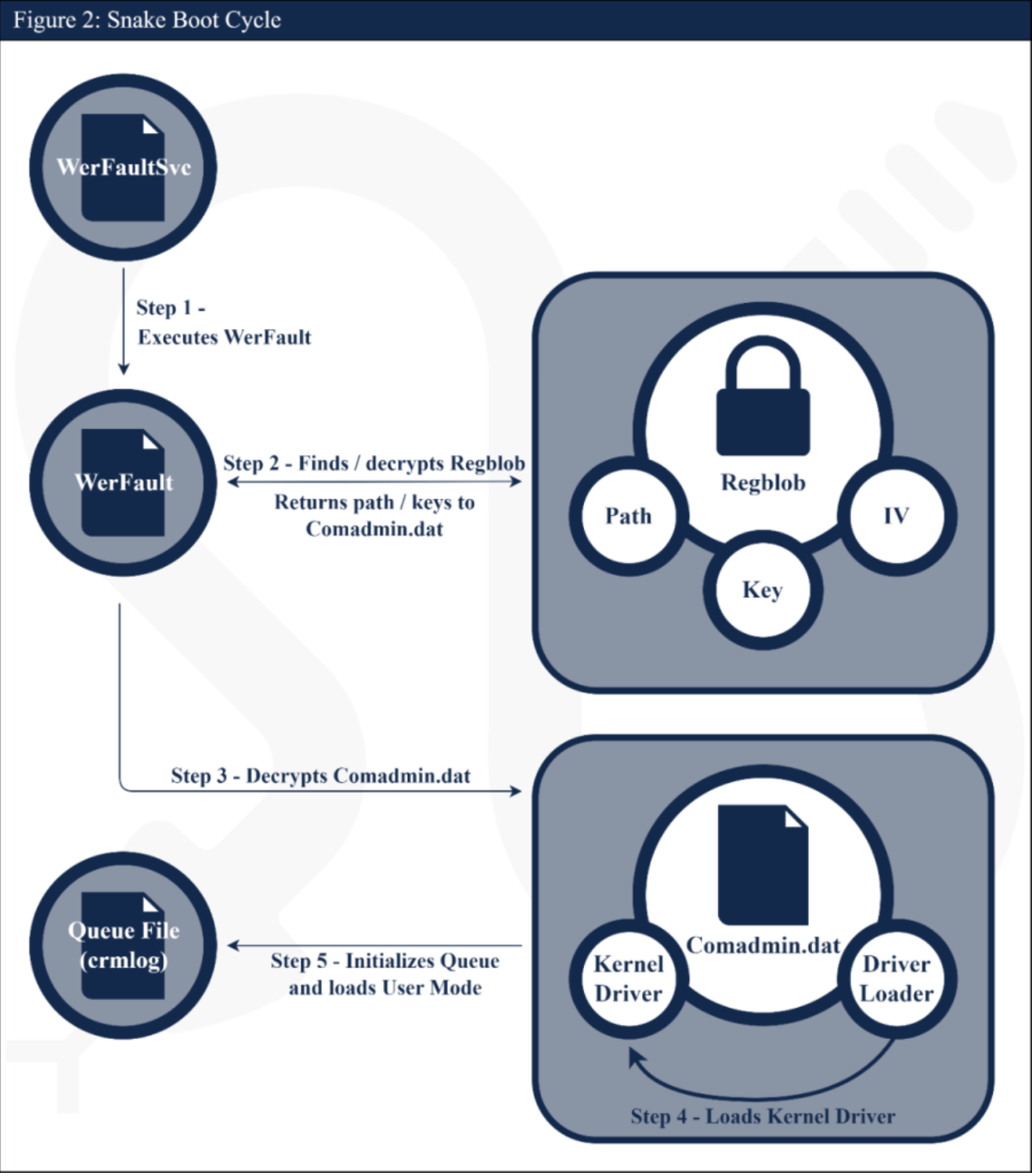
Snake enabled operators to perform the illicit tasks remotely, such as:
- Install malware
- Steal sensitive information
- Maintain persistence
- Hide malicious activities via a covert peer-to-peer network
The software was able to record every keystroke a victim made and send it back to Turla’s control center.
For nearly 20 years, this unit […] has used versions of the Snake malware to steal sensitive documents from hundreds of computer systems in at least 50 countries, which have belonged to North Atlantic Treaty Organization (NATO) member governments, journalists, and other targets of interest to the Russian Federation.
Snake, which has been the target of multiple cybersecurity industry reports, has been updated and retooled on various occasions by Turla. The goal being to guarantee that it is their most intricate long-term cyberespionage malware implant. As long as it isn’t operated against, Snake can remain on a computer’s system unbeknownst to its user or authorized users indefinitely. Despite the fact that victims have made attempts to clean the infection, the FBI reported observing Snake remaining present in certain cases.
Operation MEDUSA and Neutralization
According to THN, the effort dubbed Operation MEDUSA was conducted by means of a tool created by the U.S. Federal Bureau of Investigation (FBI) codenamed PERSEUS, that allowed the authorities to issue commands to the malware that caused it to “overwrite its own vital components” on infected machines.
The self-destruct instructions, engineered after decrypting and decoding the malware’s network communications, caused the “Snake implant to disable itself without affecting the host computer or legitimate applications on the computer,” the agency said.
The development comes a little over a year after U.S. law enforcement and intelligence agencies disarmed a modular botnet known as Cyclops Blink controlled by another Russian nation-state actor referred to as Sandworm.
The US Cybersecurity and Infrastructure Security Agency (CISA) and various other agencies have published a detailed technical advisory containing information that can be used to detect and prevent attacks involving the Snake malware, including a recent variant.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, and YouTube, for more cybersecurity news and topics.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security







