Contents:
Microsoft has announced on their website on the 26th of August about an ongoing open redirects phishing campaign that uses several techniques to trick users into clicking on compromised links. This is managed via e-mail messages that contain open redirector links which eventually lead victims to a malicious page where their credentials are stolen.
Open Redirects Phishing Campaign: What Are Open Redirects?
A web application lets an HTTP parameter have inside an URL that is user-input based, so supplied by the user. This makes the HTTP request become redirected and go to the intended source. This means an open redirect.
As Microsoft says, link redirecting is often used in marketing or sales campaigns as these have the target to determine users to access some landing pages for metrics tracking purposes. However, open redirects might be misused by hackers in phishing campaigns, because they change the value of the parameter in the URL and this eventually leads to a compromised website.
Open Redirects Phishing Campaign: the Hackers’ Methods
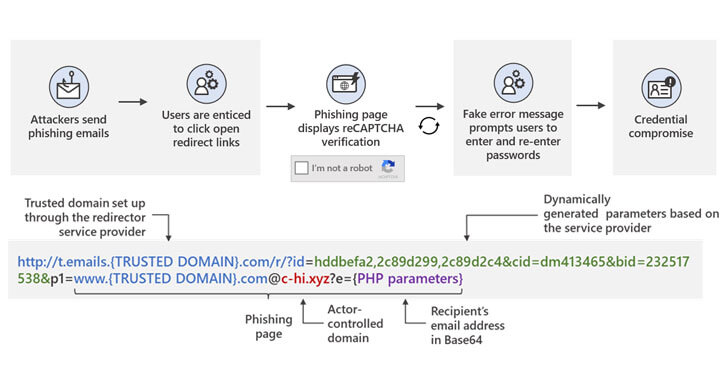
In the current open redirect phishing campaign, threat actors have the following methods, according to Microsoft’s report:
- They use open redirects embedded in URLs present in e-mail messages that impersonate legitimate tools to make the clicked link lead to their compromised website. For example, you might receive a message that seems to be a notification from Office 365 or a Zoom invitation notification with a big button that says to review the message or invitation.
- Tools cannot identify it because the URL of the correct domain is maintained as it is in the full URL.
- Even if the user hovers over the link, there’s nothing that seems doubtful, they can still see the trusted domain.
- The redirect URLs from the message are configured by means of a service that is legitimate, that’s why the tactic is successful.
- The full URL has at the end the attacker’s domain, for instance: .xyz, .club, or .shop, using domains that are top level. The hacker’s domain is there in plain sight.
- The threat actors’ domains, however, are viewed as a parameter, so the security solution won’t detect it as they usually detect primary URLs, not parameters.
- When users click on the link, a landing page opens where they have to pass a reCAPTCHA verification that makes things seem veridical. This is an evasion technique used to avoid dynamic scanning.
- After the verification is complete, a fake landing page appears that seems to be the original one from Microsoft O365 for instance. Users are required to enter their password, while the user name is already populated for more trustworthiness.
- By entering the password, an error message is displayed, and they have to reenter their password. This way, threat actors know the users entered the correct password. At this moment, credentials are compromised.
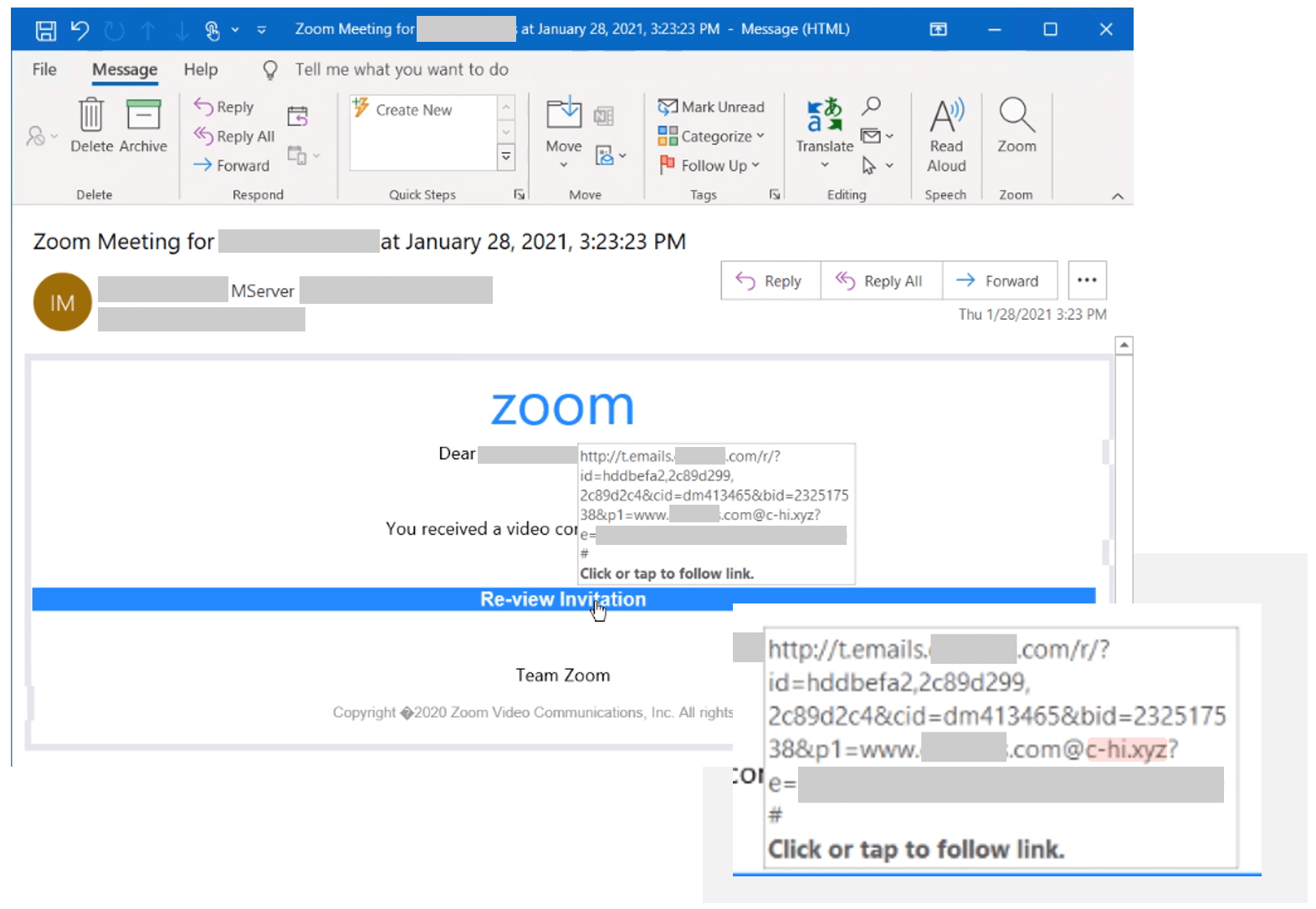
The Email Pattern
According to Microsoft’s post on the topic, most e-mail messages follow a specific pattern:
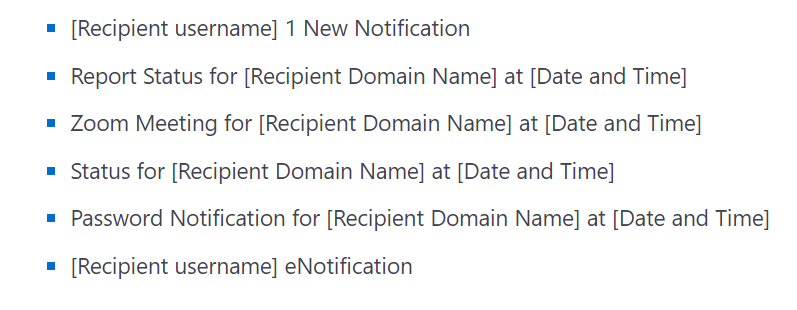
As Microsoft declared, they have found 350 unique phishing domains that show the efforts, including financial ones, of the cybercriminals to make this open redirect phishing campaign successful. The social engineering tactics combined with evasion techniques like using legitimate services to generate the open redirects, keeping inside the full URL the entire trusted domain’s link, or using reCAPTCHA check make this open redirects phishing campaign powerful.
Attackers combine these links with social engineering baits that impersonate well-known productivity tools and services to lure users into clicking. (..) Doing so leads to a series of redirections — including a CAPTCHA verification page that adds a sense of legitimacy and attempts to evade some automated analysis systems — before taking the user to a fake sign-in page. This ultimately leads to credential compromise, which opens the user and their organization to other attacks.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










