Contents:
We found evidence of a new Microsoft Phishing Campaign which is targeting Office365 users in particular, but general computer users with a Microsoft account as well. The most troubling aspect of this new campaign is its next degree of complexity.
Even if the tech behind the phishing is not exactly advanced itself, the fact that the attackers are using multiple attack vectors is enough to give pause. From the data we have gathered, we are sad to realize that this new Microsoft phishing campaign is a very solid attack. Everyone who uses a Microsoft account, especially in a business context, should be on their guard.

Heimdal® Email Security
- Completely secure your infrastructure against email-delivered threats;
- Deep content scanning for malicious attachments and links;
- Block Phishing and man-in-the-email attacks;
- Complete email-based reporting for compliance & auditing requirements;
How this New Microsoft Phishing Campaign Works
Like all phishing campaigns, the aim of these scammers is to get you to enter your credentials in one of their own pages. These phishing pages are masquerading as official Microsoft and OneDrive pages.
The incentive for users to enter their credentials is retrieving an important work-related document. The form may vary, but it’s something that either references an older conversation (‘Here is the intelligence report we discussed…’) or money (‘Here is your invoice…’). For most people, the drive to open such attachments is quite strong.
Links to The Phishing Domains (Sometimes) Come from Compromised LinkedIn Accounts
This is what makes this newest Microsoft phishing campaign so dangerous: it relies on compromised accounts to spread the message. It’s not just shots fired into the dark.
The first step seems to be hacking into someone’s account and then using it to further spread the malicious message. This lends more credibility to the phishing invitation when it arrives in the inbox of the next targets.
Just like in Business Email Compromise (BEC) attacks, the victim believes they are communicating with an acquaintance or a colleague, someone they trust. Someone in our company received this message on LinkedIn, from another person they knew in real life and trusted:
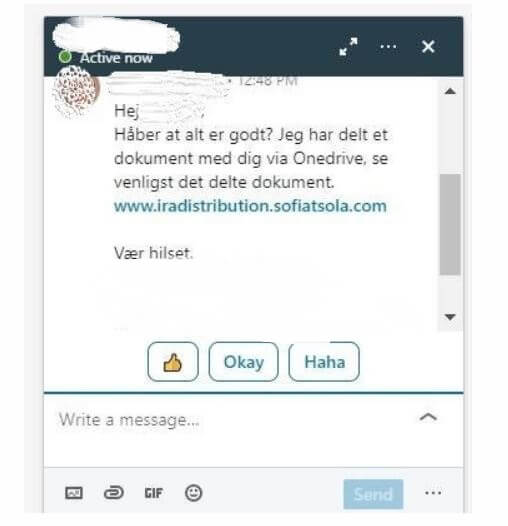
The Next Steps in the Microsoft Phishing Campaign
Once the user clicks on the malicious attachment in the Microsoft phishing campaign, they will be redirected to a seemingly legit OneDrive portal.
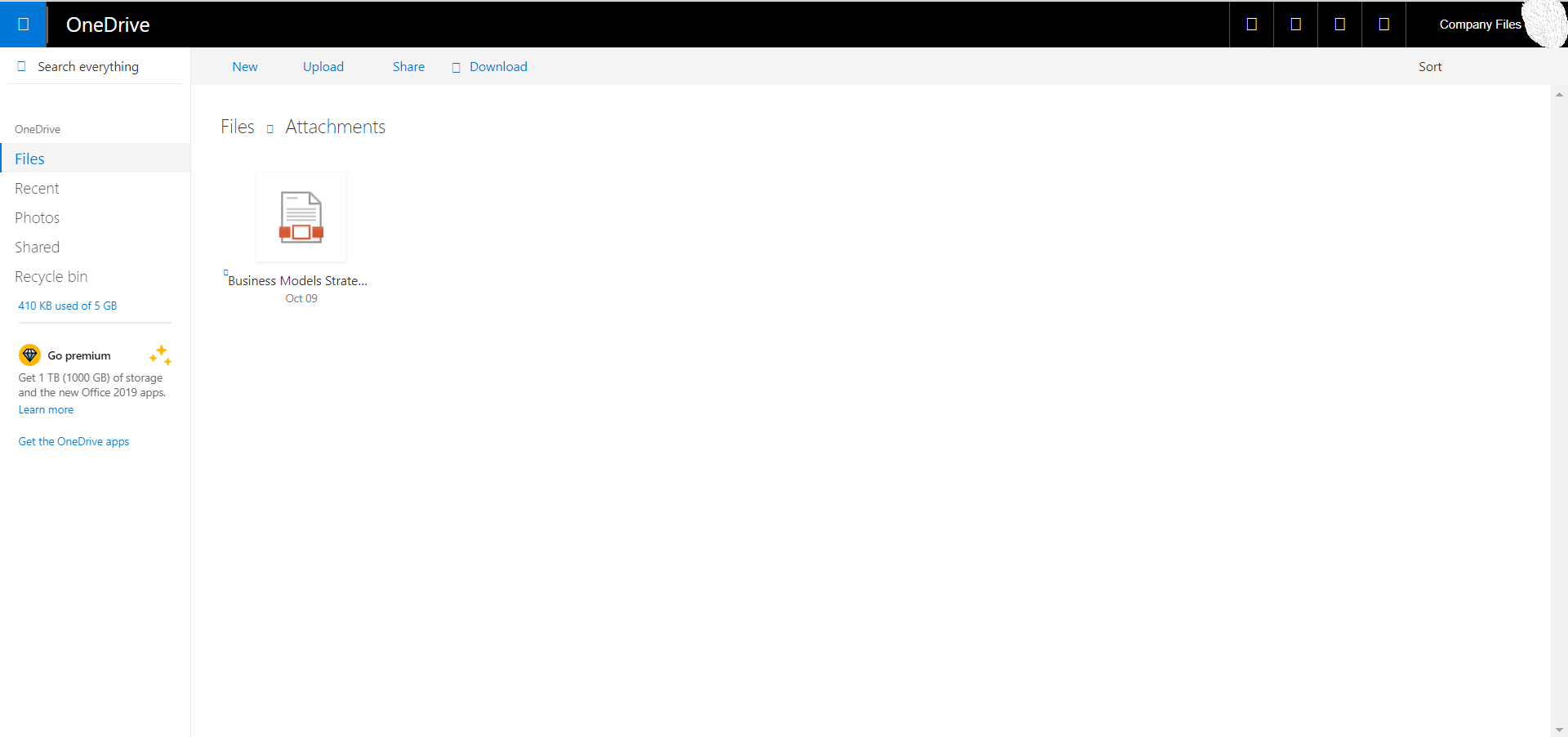
After clicking the attachment, the user will then be redirected to a fake Microsoft Office365 portal where they will be asked for their credentials.
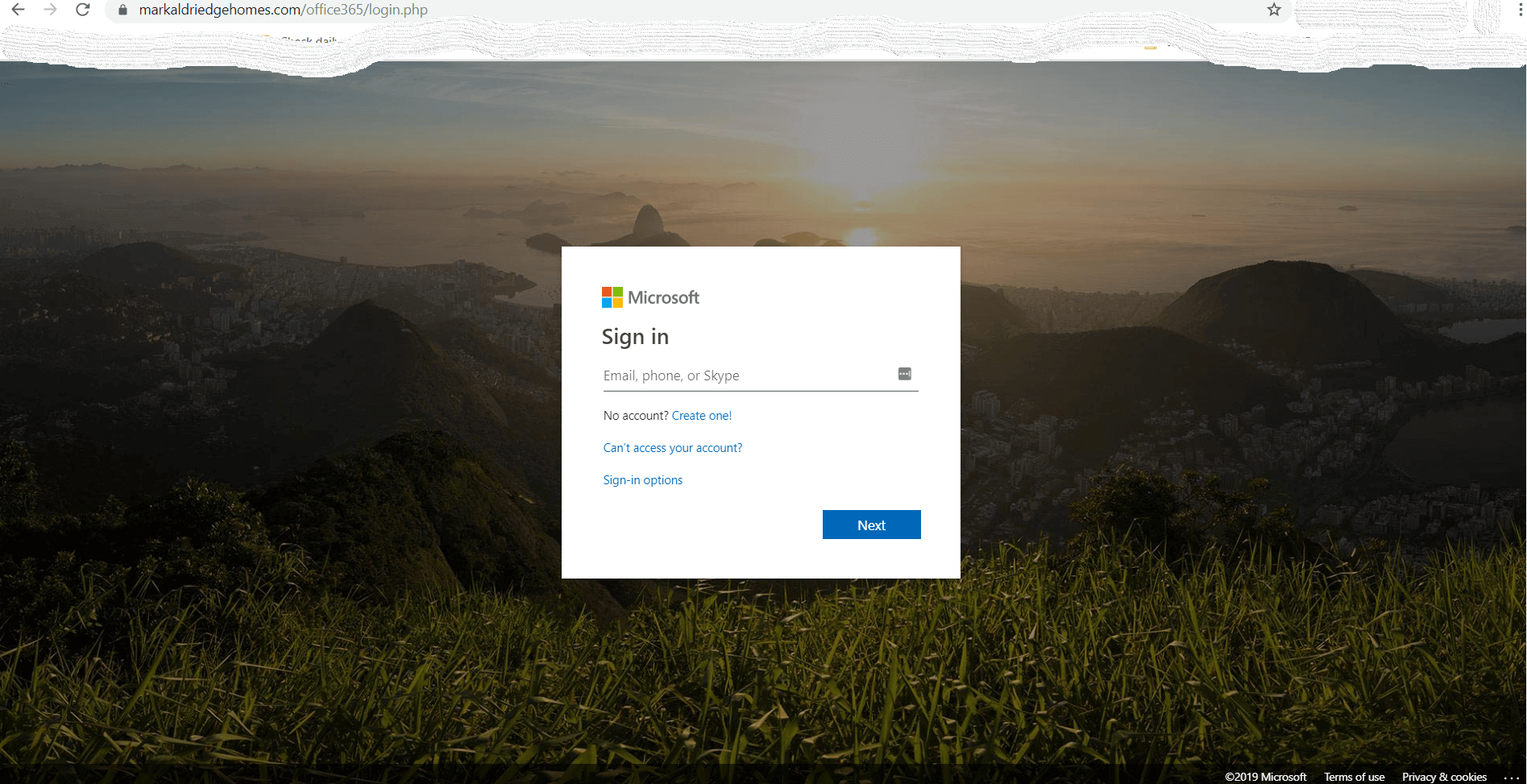
If you look at the web address of the page, it’s clearly not what it should be.
Who’s Behind the Wave of Attacks
We identified two domains behind this Microsoft phishing campaign so far, but more will probably spring up in the following weeks.
The first domain, iradistribution.sofiatsola.com has all the information blocked or modified to show that it is blocked by GDPR. This is a move done to hide all info about what entity registered it, where they are based and so on. Until the block can come off due to malicious activity, the hackers have enough time to do their worst. The IP address of this domain is 67.222.38.76 but the rest of the info is hidden.
VirusTotal has not identified it as malicious yet. According to its registry data, the domain was first created 15 years ago and modified 5 months ago. This indicates that the phishing campaign has been around for a while.
The second domain, markaldriedgehomes.com has all the info still detectable. The IP addresses they use are 45.60.98.93 and 69.89.31.241. The domain is handled from a US Texas address by an admin with the email dc75a9c3ee070d94s@YAHOO.COM.
VirusTotal does mark this one as suspicious but the domain is still not blocked by most cybersecurity solutions yet. Just like the first domain, and hardly a coincidence, this one has also been updated 5 months ago.
Note of caution: The fact that the attackers are combining several tactics in a concentrated attack is disconcerting. Considering that they first compromised the accounts of real people and then used them as a launcher for the next wave of attacks, we advise full caution.
If you get any kind of message which requires a sign in for downloading something, make sure you check and double-check the domain name and the authenticity of the request. Even if the message doesn’t look like these examples above.
How to Stay Safe from this Microsoft Phishing Campaign and Similar Threats
#1. Learn more about phishing and spear phishing
Keep yourself up to date with the tactics of scammers, so you know how to recognize it when it happens to you.
Spear phishing should be something to be especially mindful of. Spear phishing is the very targeted phishing scam driven at the head of an enterprise or anyone in an executive position. Such a campaign is carefully planned out and tailored to maximize the chances of the person falling for it.
Read our complete guide on spear-phishing to learn how it works and how to stay safe.
While you’re at it, you might also be interested in this guide on social engineering. Phishing is just one of the ways hackers can get to you by abusing human nature and our desire to trust. Learn the rest of the tricks to be mindful of by brushing up on your social engineering knowledge.
#2. Have a strong DNS traffic filtering solution
Of course, vigilance is not enough. You also need to have a strong DNS filtering solution that can help identify fake websites’ domain name servers.
As long as you have that protecting your endpoints and you continue to be wary of sharing your credentials easily, nothing will disrupt you. Stay safe!


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










