Contents:
A new custom-made malware, the Screenshotter, surveils the victims before stealing data. The threat actor called TA886 is utilizing this malware to target users from the United States and Germany.
Researchers first spotted the campaign in October 2022, but its activity increased in 2023.
How Screenshotter Malware Works
TA886 has created this malware to be able to evaluate the victims before further intrusion, Proofpoint researchers explain. The threat actor proceeds to data exfiltration only if the attack can bring enough money.
The targeted user receives a phishing email with malicious macros. The email may contain a malicious Microsoft Publisher (.pub) attachment, a link to .pub files with macros, or an infected PDF that downloads JavaScript files.
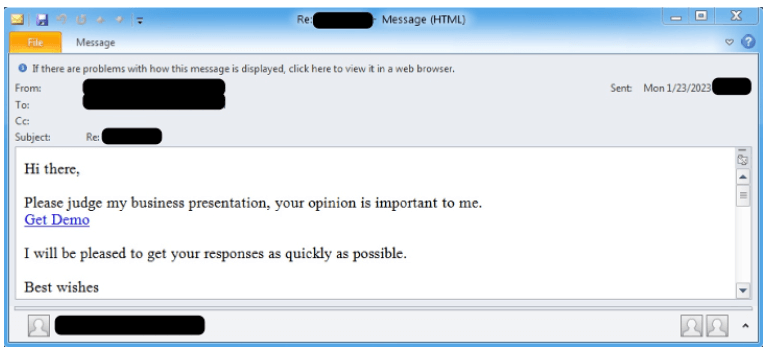
The victim triggers the attacks by clicking on the links. And the goal of this email is to download and execute the Screenshotter malware. Then the customized malware takes JPG screenshots from the infected device and sends them to its creator.
After manually evaluating the screenshots, the attacker can take two actions. He can demand more JPGs from the malware, or he can drop additional custom payloads.
TA886 uses Rhadamanthys to steal data. This malware family can also steal cryptocurrency wallets, credentials, and cookies, FTP clients, Steam accounts, Telegram and Discord accounts, VPN configurations, and email clients.
The TA886 Threat Actor
It seems that TA886 may be a Russian threat actor. This is based on the hours when he is active, sending commands to the malware, and the presence of Russian language variable names and comments in code lines.
Proofpoint has attempted to find overlaps and similarities with past reports describing similar TTPs (techniques, tactics, and procedures), but it could not make any definitive connections.
In conclusion, Active Directory profiling employed by Screenshotter is very concerning. As this can be used by malicious actors to compromise all domain-joined hosts.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, YouTube, and Instagram for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security









