Contents:
A new variant of the Drinik Android malware targets 18 Indian banks and shifts strategies by masquerading as the country’s official tax management application, in an attempt to obtain victims’ personal information and banking credentials.
Since 2016, Drinik has been spreading throughout India as an SMS stealer. In September 2021, however, it gained banking trojan functionality, allowing it to steal information from customers of 27 different banks.
Cyble analysts have been keeping tabs on the malware and have discovered that it has developed into a full-fledged Android banking trojan equipped with screen recording, keylogging, exploitation of Accessibility services, and the capability to launch overlay attacks.
The Malware Uses a New Strategy for Stealing Credentials
The current variant of the malware is disguised as an Android application package (APK) called ‘iAssist’, which claims to be the official tax administration tool of India’s Income Tax Department.
Upon setup, it demands access to read the user’s call history, read and write to external storage, and receive, read, and send SMS. The user is then prompted to grant permission for the app to (ab)use the Accessibility Service. If allowed, it turns off Google Play Protect and exploits it to record the screen, record keystrokes, and execute navigational gestures.
And finally, the application loads the actual Indian income tax site through WebView, a completely different strategy from its previous versions, when it used phishing pages. This time, using a keylogger, the malware steals users’ credentials by recording their typing activity.
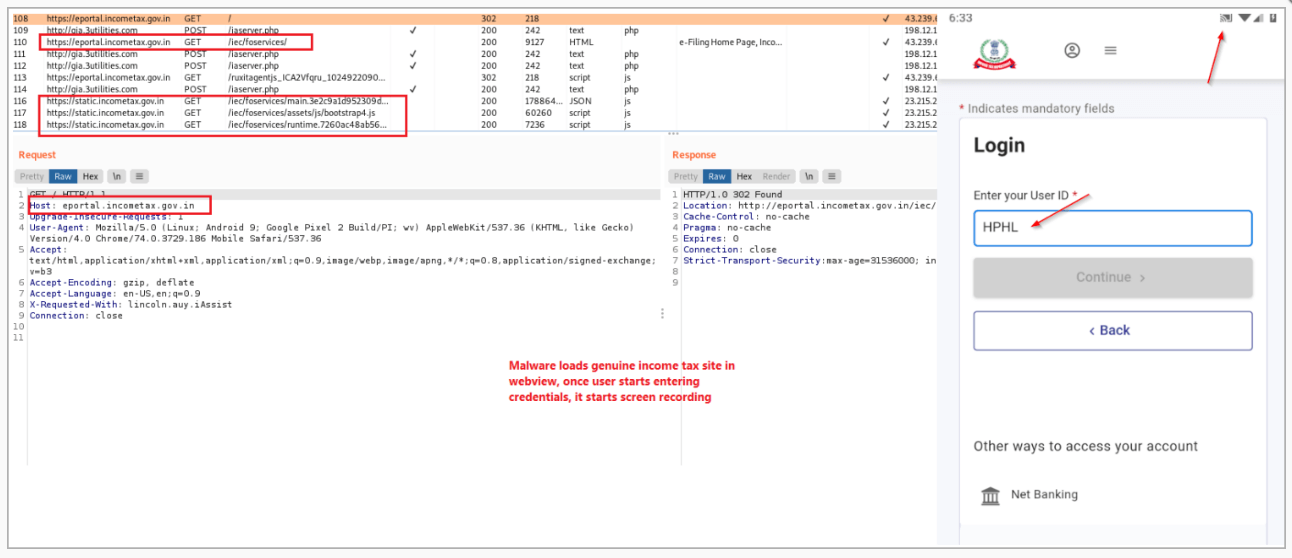
Loading the tax site & screen recording.
Drinik keeps an eye on the Accessibility Service for events related to the 18 banks’ apps, in order to find ways to attack them. One of the banks that are being targeted is the State Bank of India (SBI), which has 22,000 branches and serves 450,000,000 people.
If there is a match, the malware gathers the user’s credentials from the keylogging data and sends them to the C2 server. During this attack, Drinik takes advantage of the “CallScreeningService” to block incoming calls that could stop the login and, therefore, the process of stealing data.
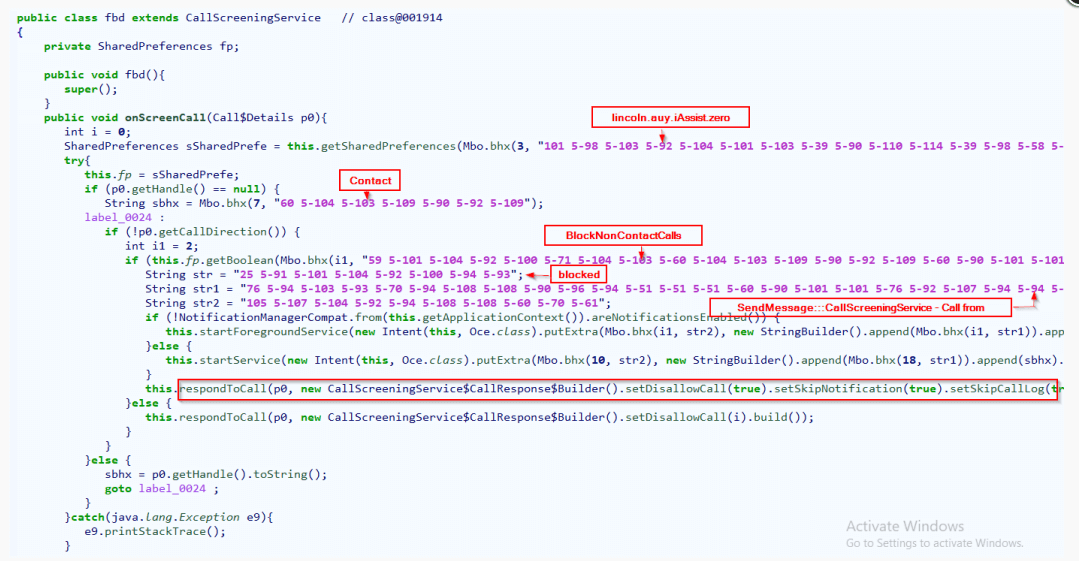
Drinik blocking incoming calls.
Drinik’s Evolution
Bleeping Computer notes that, despite Drinik’s lack of complexity compared to other banking trojans, its developers keep adding new capabilities to make it more difficult to spot.
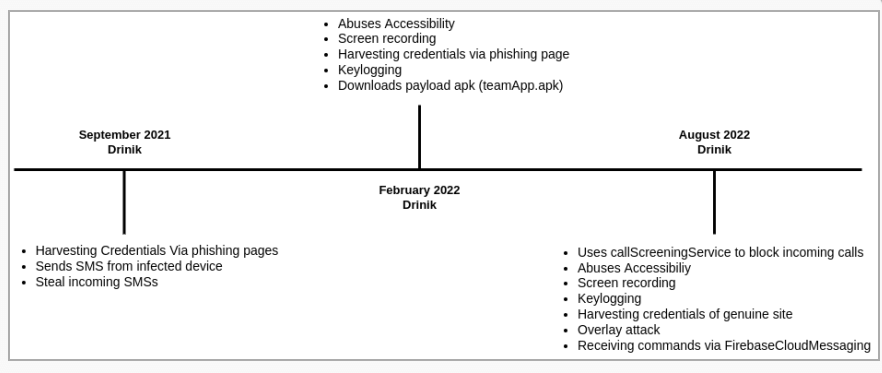
To view Cyble’s entire analysis, click here. By focusing on Indian citizens, Drinik has a large pool of prospective victims, and any successful additions to the malware could result in significant earnings for the criminals behind it.
As a general recommendation, it is best to avoid installing an APK from anywhere other than the Play Store and always use two-factor authentification, especially while accessing online banking websites.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










