Contents:
The “RapperBot” malware group has been rapidly expanding since mid-June 2022.
Researchers discovered new samples of RapperBot malware used to build a botnet capable of carrying Distributed Denial of Service (DDoS) attacks against game servers.
Despite many similarities to the original Mirai source code, this group differs from other IoT malware attacks in that it can brute force credentials and connect to SSH servers rather than Telnet, which was how Mirai implemented it.
The Discovery of RapperBot
FortiGuard Labs discovered IoT malware samples with SSH-related strings in June 2022, which was unusual in other IoT threat campaigns. Furthermore, the size of the code referencing these strings compared to the code used for DDoS attacks, which typically comprises most of the code in other variants.
Further investigation revealed that this malware group, dubbed “RapperBot,” is intended to serve primarily as an SSH brute-forcer with limited DDoS capabilities. It targets ARM, MIPS, SPARC, and x86 architectures, typical of most IoT malware.
RapperBot is known to solely force SSH servers configured to accept password authentication, as the network security firm first documented in August 2022.
The malware, named after an embedded URL to a YouTube rap music video in an earlier iteration, is said to have accumulated a large assortment of compromised SSH servers, with over 3,500 unique IP addresses used to scan and force their way into the servers.
Did RapperBot Level Up Their ‘Game’?
As it turns out, the campaign is less like RapperBot and more like an older campaign that appeared in February and then mysteriously vanished in the middle of April.
The newly formed malware is heavily influenced by the Mirai botnet, the source code leaked in October 2016, resulting in the emergence of several variants.
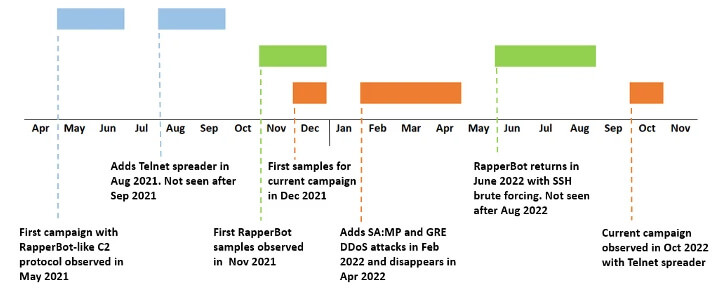
This list of hard-coded plaintext credentials, which are default credentials associated with IoT devices, is embedded into the binary rather than being retrieved from a command-and-control (C2) server, as was observed in artifacts discovered after July 2022.
RapperBot’s previously reported campaign was restricted to generic DoS methods against TCP and UDP services. This campaign includes DoS attacks on the GRE protocol (possibly using Mirai source code) and the UDP protocol used by the Grand Theft Auto: San Andreas MultiPlayer (SA: MP) mod.
The following are the DoS attack commands that this botnet supports:
- 0x00: Generic UDP flood
- 0x01: TCP SYN flood
- 0x02: TCP ACK flood
- 0x03: TCP STOMP flood
- 0x04: UDP SA: MP flood targeting game servers running GTA San Andreas: Multi Player (SA: MP)
- 0x05: GRE Ethernet flood
- 0x06: GRE IP flood
- 0x07: Generic TCP flood
These specific commands, combined with the lack of HTTP-related DDoS attacks, indicate that this campaign primarily aims at game server DDoS.
According to the hardcoded prompt messages in the malware, most targeted devices are IoT devices such as routers and DVRs.
This campaign targets older devices with the Qualcomm MDM9625 chipset, such as LTE modems. Despite having the same credentials in the list embedded in the binary, it attempts to gain root access to these devices using a default password.
What Do The Two RapperBot Campaigns Have in Common?
The fact that samples from both campaigns use the same C2 protocol, combined with the absence of this campaign during the RapperBot campaign, which ran from June to August 2022, and its recent reappearance, suggests that this is more than a coincidence.
- In both campaigns, the C2 commands and corresponding IDs are identical.
- Both campaigns demonstrate some effort in optimizing the brute forcing implementation. In addition, the code for the brute forcing implementation is far more structured than typical IoT malware, which copies and pastes code with minor changes.
- RapperBot also supported Mirai’s widespread TCP STOMP attack. However, because the source code for both Mirai and Satori is publicly available, this is a weak link between the campaigns.
Conclusion
Based on fundamental commonalities between this new campaign and the previously reported RapperBot campaign, it is almost sure that they are operated by the same threat actor or by different threat actors with access to a privately shared base source code.
Unlike the previous RapperBot campaign, this one has a clear goal: to compromise as many IoT devices as possible to build a DDoS botnet.
Although this new campaign differs significantly from previous campaigns, the solution remains the same: create strong passwords for all internet-connected devices.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, YouTube, and Instagram for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










