Contents:
Cybersecurity researchers uncovered a new strain of ransomware named Mimic. Mimic uses Everything API, a file search tool for Windows, to search for files to encrypt.
Some of the code in Mimic is similar to that found in Conti, whose source code was leaked to a Ukrainian researcher in March 2022.
As a sophisticated malware, Mimic can eliminate shadow copies, shut down various applications and services, and identify encrypted files using Everything32[.]dll functions.
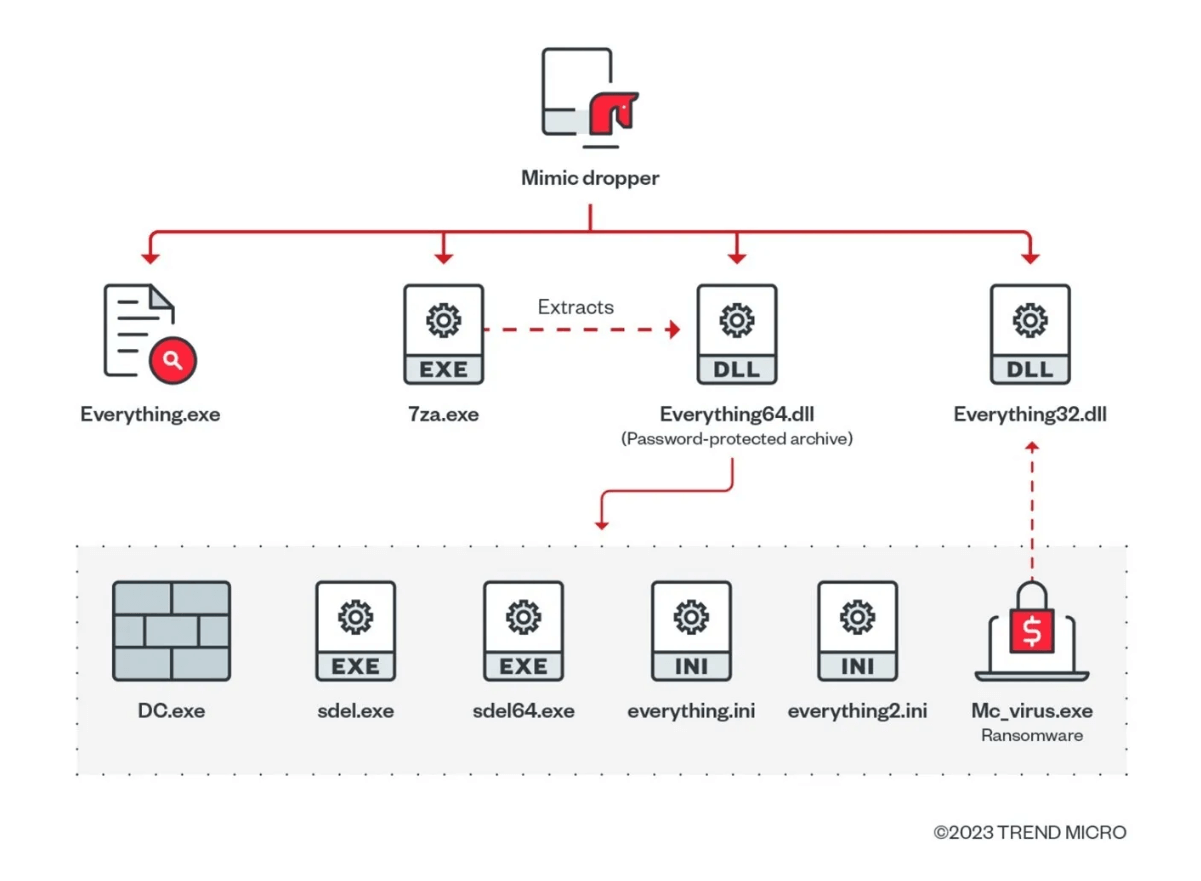
Mimic Ransomware Components
An initial stage of a Mimic ransomware attack involves the victim receiving an executable. On the target system, the executable extracts four files:
- Main payload;
- Files related to ancillary services;
- Tools to disable Windows Defender.
Using multiple processor threads to encrypt data faster, Mimic is a highly adaptable strain of ransomware that targets specific files via command-line arguments.
Below are the components that Mimic uses:
- 7za[.]exe: Legitimate 7zip file that is used to extract the payload;
- Everything[.]exe: Legitimate Everything application;
- Everything32[.]dll: Legitimate Everything application;
- Password-protected archive containing malicious payloads: Everything64[.]dll.
What Is Mimic Capable of?
The new ransomware family possesses several different capabilities seen in modern ransomware strains, such as:
- Collecting system information;
- Creating persistence via the RUN key
- Bypassing User Account Control (UAC)
- Disabling Windows Defender;
- Disabling Windows telemetry;
- Activating anti-shutdown measures;
- Activating anti-kill measures;
- Unmounting Virtual Drives;
- Terminating processes and services;
- Disabling sleep mode and shutdown of the system;
- Removing indicators;
- Inhibiting System Recovery.
Mimic ransomware shuts down processes and services to gain access to vital information to remove security barriers.
By exploiting the ‘Everything32[.], dll’ file dropped during the initial infection, mimic malware scans the infected system for specific file names and types.
Everything API allows Mimic to identify files suitable for encryption without risking locking system files that could make the system unbootable.
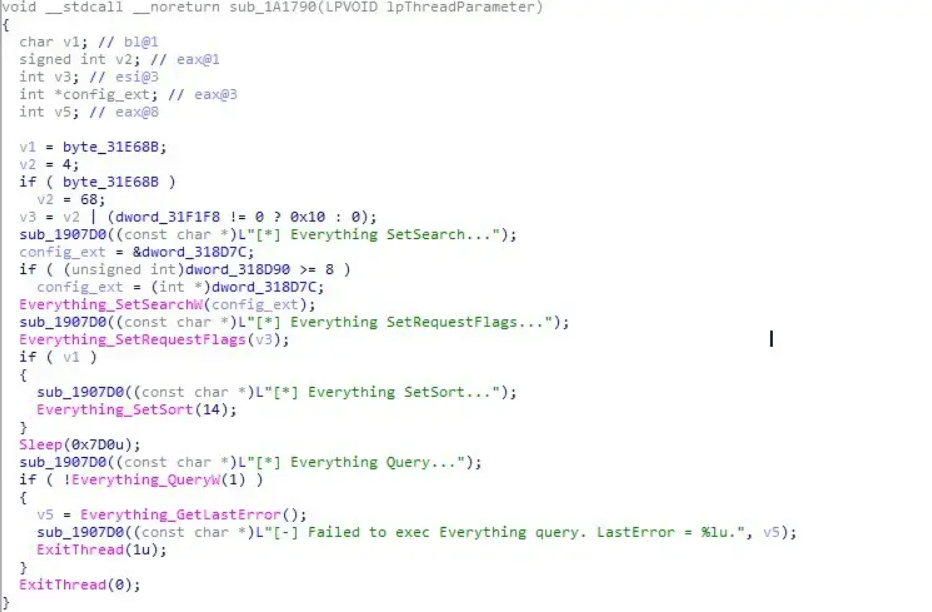
Using Mimic’s algorithm, all files are meticulously scanned, identifying those that can be encrypted while bypassing any system files that might cause the system to fail.
Below is the Mimic ransomware configuration:
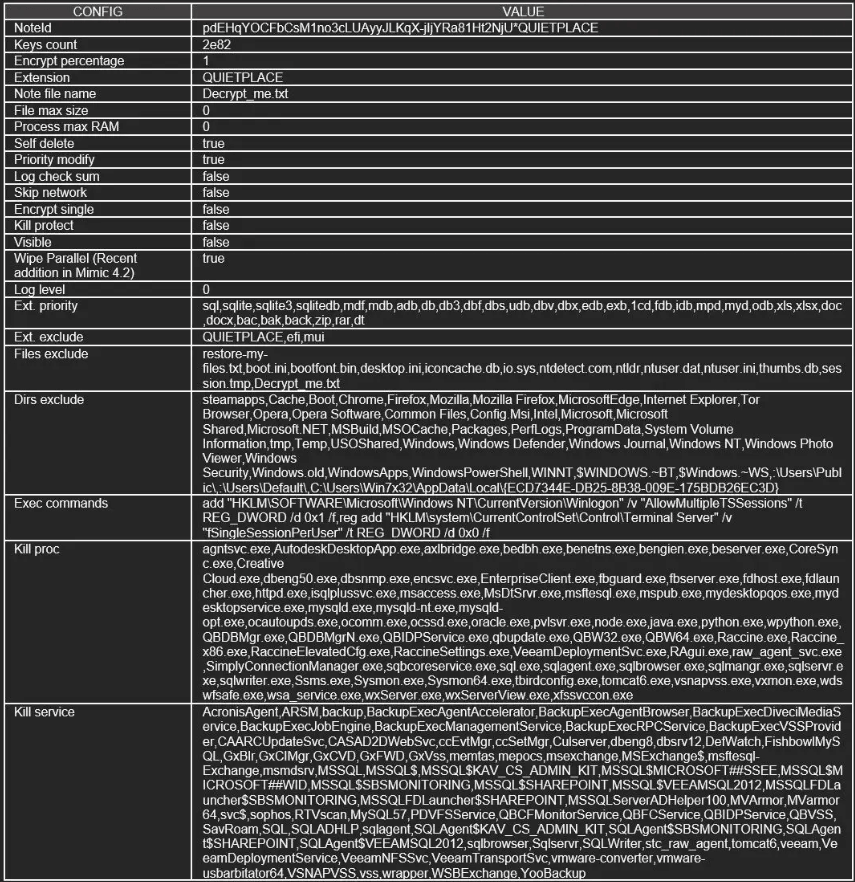
The file extension of encrypted files is “.QUIETPLACE”.
As part of the ransom note, the perpetrator demands Bitcoin payment for the safe return of the locked data, along with instructions on how to proceed.
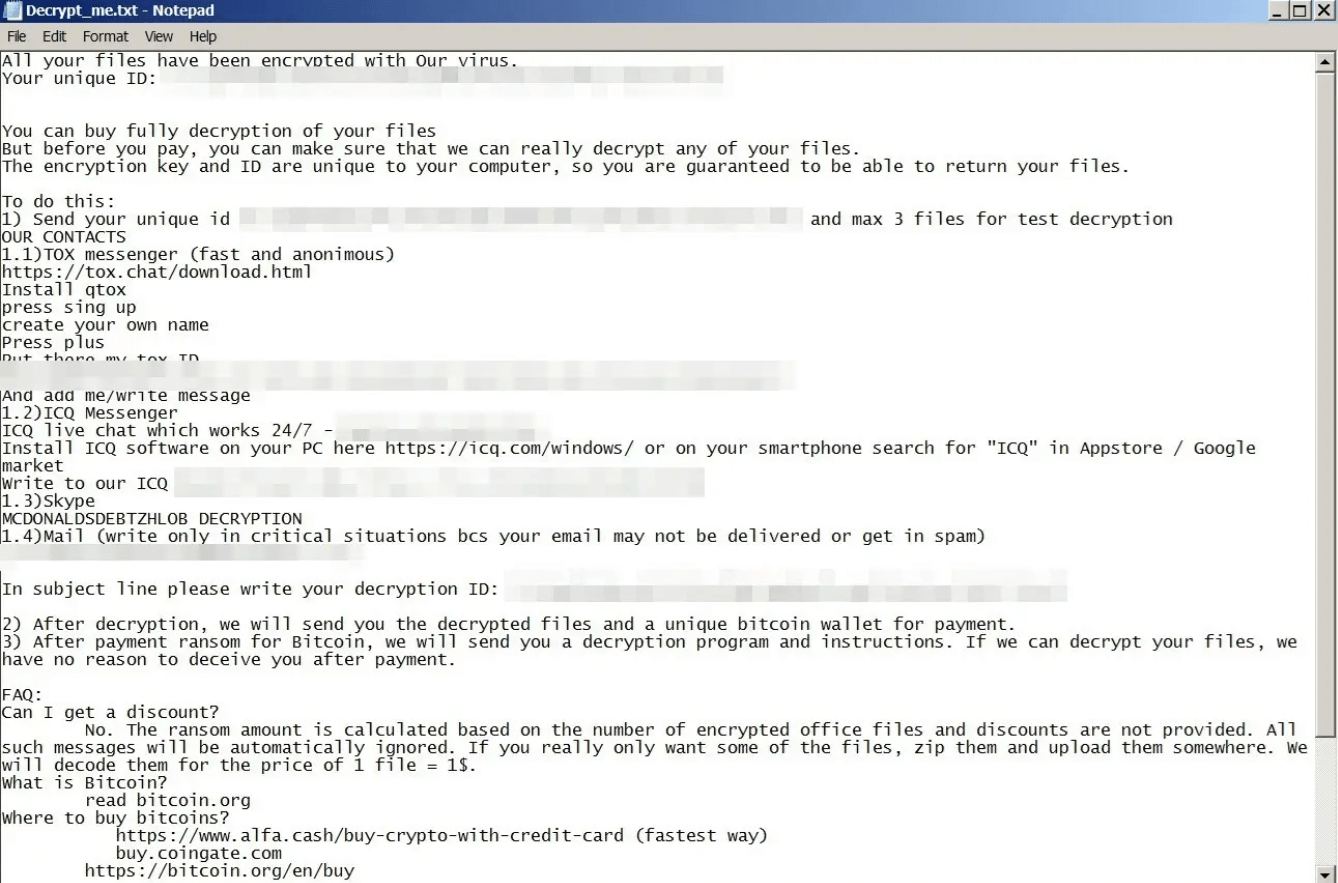
Although Mimic, a novel variant, has yet to be evaluated thoroughly in terms of its actions, it is evident from the use of Conti builder and Everything API that the creators have a high level of software development expertise and a solid understanding of their objectives by using the Conti builder and Everything API.
How Can Heimdal Help?
To combat ransomware, you can use the exceptional integrated cybersecurity suite, which includes the Ransomware Encryption Protection module, which is universally compatible with any antivirus solution and is entirely signature-free, ensuring superior detection and remediation of any ransomware, whether fileless or data-based (including the most recent ones like LockFile).

Heimdal™ Ransomware Encryption Protection
- Blocks any unauthorized encryption attempts;
- Detects ransomware regardless of signature;
- Universal compatibility with any cybersecurity solution;
- Full audit trail with stunning graphics;
If you liked this article, follow us on LinkedIn, Twitter, Facebook, YouTube, and Instagram for more cybersecurity news and topics.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security








