Contents:
Cybersecurity researchers uncovered a new, highly-advanced information stealer, dubbed SYS01 stealer, that has been deployed in attacks on critical government infrastructure employees, manufacturing companies, and other industries since November 2022.
Morphisec researchers discovered similarities between the SYS01 stealer and another information-stealing malware called S1deload.
We have seen SYS01 stealer attacking critical government infrastructure employees, manufacturing companies, and other industries. (…) The threat actors behind the campaign are targeting Facebook business accounts by using Google ads and fake Facebook profiles that promote things like games, adult content, cracked software, etc. to lure victims into downloading a malicious file. The attack is designed to steal sensitive information, including login data, cookies, and Facebook ad and business account information.
According to the researchers, the campaign was identified in May 2022 and was linked to the Ducktail operation by Zscaler researchers. The DUCKTAIL campaign was originally investigated by WithSecure researchers in July 2022, and it targeted individuals and organizations using Facebook’s Business and Advertising platforms.
Infection Chain
When the ZIP file is opened, a loader is executed, which is frequently in the shape of a legitimate C# application. The application is vulnerable to DLL side-loading, a technique used to load a malicious DLL when the legitimate app is run.
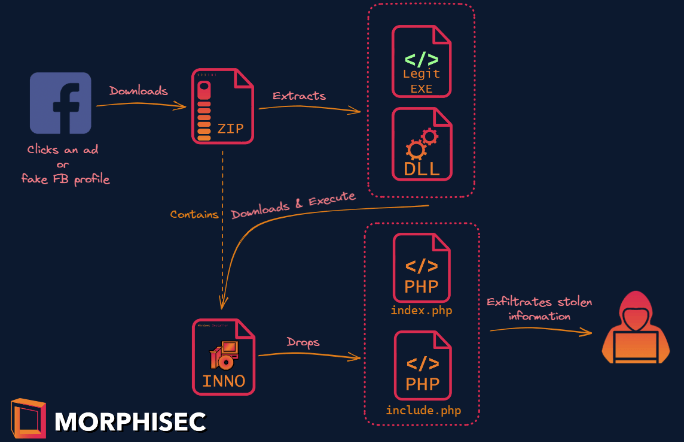
The researchers observed malicious actors leveraging Western Digital’s WDSyncService.exe and Garmin’s ElevatedInstaller.exe, two legitimate programs, to side-load the malicious payload.
Finally, the PHP-based SYS01stealer malware can steal browser cookies and abuse authenticated Facebook sessions to access the victim’s account and steal information. The purpose is to gain control of the victims’ Facebook Business accounts.
The malware scans the machine for common browsers, such as Google Chrome, Microsoft Edge, Brave Browser, and Firefox, in order to collect Facebook session cookies from victims. It extracts all stored cookies, including any Facebook session cookies, from each browser it finds, explains Security Affairs.
The malware also collects information from the victim’s personal Facebook account, such as the victim’s name, email address, date of birth, and user ID, as well as additional information such as 2FA codes, user agents, IP address, and geolocation.
The malware can also upload files from the infected system to the C2 server and execute commands sent by the C&C. The malicious code also includes an update mechanism.
The researchers recommend implementing a zero-trust policy and limiting users’ abilities to download and install programs. Additionally, because SYS01 stealer is based on a social engineering campaign, it’s critical to instruct users on the techniques adversaries use so they can recognize them.
Morphisec’s full report on the info stealer is available here.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, and YouTube for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










