Contents:
A new, sophisticated malware toolkit called Decoy Dog was discovered after cybersecurity researchers analyzed more than 70 billion DNS records belonging to enterprise networks.
To avoid detection, Decoy Dog uses stealthy methods like strategic domain aging and DNS query dribbling, in which a steady stream of queries is sent to the command-and-control (C2) domains.
The malware was discovered in early April 2023 after anomalous DNS beaconing activity, and the researchers claim that the malware’s unusual characteristics allowed them to map additional domains used in the attack infrastructure.
Decoy Dog is a cohesive toolkit with a number of highly unusual characteristics that make it uniquely identifiable, particularly when examining its domains on a DNS level.
However, Decoy Dog’s actual use in the wild is “very rare,” with the DNS signature matching less than 0.0000027% of the 370 million active domains on the internet.
Pupy RAT, the Primary Malware Component
One of the main components of the toolkit is Pupy RAT, an open source trojan that is delivered through DNS tunneling, a method that uses DNS queries and responses as a C2 for dropping payloads in a stealthy manner.
Although there is no evidence linking Earth Berberoka (aka GamblingPuppet), a Chinese nation-state actor, to this campaign, his name has been previously associated with the use of the cross-platform Pupy RAT, explains THN.
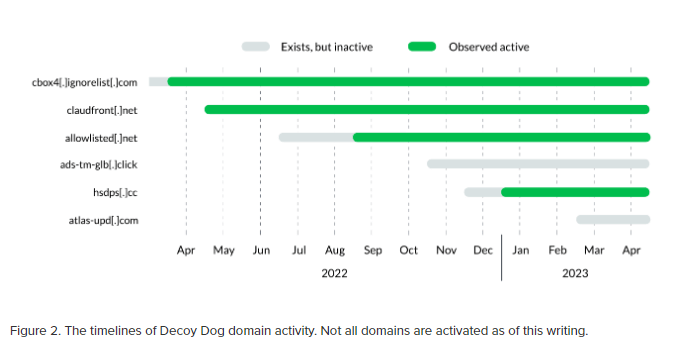
Three different infrastructure configurations have been detected to date, suggesting that the Decoy Dog operation had been running for at least a year before its discovery.
In addition, Decoy Dog domains have been observed to exhibit some peculiar DNS beaconing behavior, including making periodic but infrequent DNS requests.
Decoy Dog domains can be grouped together based on their shared registrars, name servers, IPs, and dynamic DNS providers. Given the other commonalities between Decoy Dog domains, this is indicative of either one threat actor gradually evolving their tactics, or multiple threat actors deploying the same toolkit on different infrastructure.
The complete technical analysis published by Infoblox is available here.
Check out the following if you want to learn more about DNS security, DNS filtering, and DNS best practices.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, and YouTube for more cybersecurity news and topics.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security








