Contents:
U.S. federal agencies NSA, CISA, and the FBI revealed the top security vulnerabilities most targeted by threat actors backed by the People’s Republic of China (PRC) with the intention to compromise government and critical infrastructure networks.
NSA, CISA, and FBI continue to assess PRC state-sponsored cyber activities as being one of the largest and most dynamic threats to U.S. government and civilian networks.
Further Context
The joint Cybersecurity Advisory (CSA) claims Chinese-sponsored hackers are targeting U.S. and its allies, as well as tech companies with the clear intent to gain access to sensitive networks and steal intellectual property. The report is meant to inform about trends and persistent tactics, techniques, and procedures.
According to BleepingComputer, the advisory also contains recommended mitigations for each of the security flaws most exploited by threat actors, as well as detection methods and vulnerable technologies to help defenders spot and block incoming attack attempts.
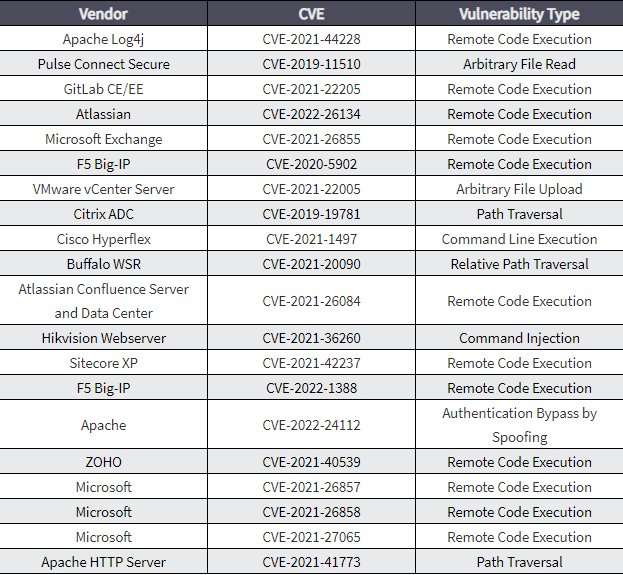
Top CVEs most used by Chinese state-sponsored cyber actors since 2020 –Source
Recommended Actions
The CSA further advises the U.S. government and its allies, along with all critical infrastructure and private sector organizations, a series of mitigation measures to defend against cyberattacks.
- Patch systems and equipment promptly and diligently – in order to prevent remote code execution or denial-of-service on externally facing equipment, with the recommendation to use a patch management program that will enable a patching cycle.
- Enhanced monitoring of network traffic, email, and endpoint systems.
- Protection capabilities to stop malicious activity such as anti-virus software and other endpoint protection to automatically detect and prevent malicious files from executing.
- Move toward the Zero Trust security model and monitoring the logs for suspicious activity.
Ever since 2020, Chinese-backed threat actors have been exploiting vulnerabilities, which have been made public in a previously released advisory.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, YouTube, and Instagram for more cybersecurity news and topics.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security







