Contents:
On 4 October 2022 U.S. Government announced a data breach at a U.S. organization in the Defense Industrial Base (DIB) sector.
The infection lasted approximately ten months before being identified, with the initial access taking place in January 2021.
The origin of the attackers is unknown at the moment, but several advanced persistent threat groups (APT) were probably involved in the attack using the victim’s Microsoft Exchange Server.
DIB organizations provide military weapons system studies, innovation, design, manufacturing, distribution, and maintenance, as well as all necessary components and parts.
Details About the Malware
The Cybersecurity and Infrastructure Agency (CISA), the Federal Bureau of Investigation (FBI), and the National Security Agency (NSA) issued a joint report containing details from the incident response activity that took place between November 2021 and January 2022.
“The hackers combined custom malware called CovalentStealer, the open-source Impacket collection of Python classes, the HyperBro remote access trojan (RAT), and well over a dozen ChinaChopper webshell samples”, according to BleepingComputer.
Cybercriminals also targeted the ProxyLogon collection of four Microsoft Exchange Server vulnerabilities. This happened around the time Microsoft issued an emergency security update to address them.
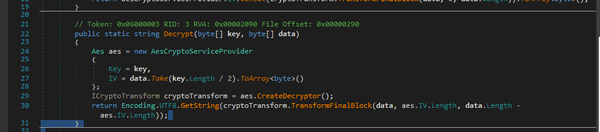
In a separate report, CISA provides technical analysis for CovalentStealer noting that the malware relies on code from two publicly available utilities, ClientUploader and the PowerShell script Export-MFT, to upload compressed files and to extract the Master File Table (MFT) of a local storage volume.
CovalentStealer also contains resources for encrypting and decrypting the uploaded data, and configuration files, and to secure communications.
Another CISA report contains details about HyperBro RAT. A trojan that can upload/download files to/from the infected system, do logging keystrokes, execute commands on the infected device, and bypass User Account Control to function with full admin privileges.
The Timeline of the Attack
The breach happened in mid-January 2021, with the hackers gaining access to the Exchange Server of the targeted company. Four hours later they used an admin account to access the Exchange Web Services (EWS) API, gaining visibility to client application messages.
In February 2021 attackers accessed the network once more using the same admin account through a VPN. This time they used Windows Command Shell to carry out recognition activities
The actors used Command Shell to learn about the organization’s environment and to collect sensitive data, including sensitive contract-related information from shared drives, for eventual exfiltration. The actors manually collected files using the command-line tool, WinRAR. These files were split into approximately 3MB chunks located on the Microsoft Exchange server within the CU2\he\debug directory.
In March 2021 ProxyLogon vulnerabilities were used to install 17 China Chopper webshells on the Exchange Server. And in April 2022 the hackers began the lateral movement on the network using Impacket to temper with network protocols.
Impacket allowed them to compromise an account with larger privileges, gaining remote access from multiple external IP addresses to the Exchange server through Outlook Web Access (OWA).
Between July and October 2022 cybercriminals uploaded data to a Microsoft OneDrive location using a custom-built CovalentStealer implanted deep in the infected network.
How to Detect Data Breach
The joint report from CISA, FBI, and NSA contains also a set of recommendations so organizations will detect “persistent, long-term access in compromised enterprise environments”:
- monitor logs to identify connections from unusual VPSs and VPNs
- monitor for suspicious account use such as inappropriate or unauthorized use of administrator accounts, service accounts, or third-party accounts
- monitor for the installation of unauthorized software
- monitor for suspicious and known malicious command-line use
- investigate unauthorized changes to user accounts
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security