Contents:
Dubbed “MosaicLoader”, this new malware gets its name from its sophisticated internal structure tuned to prevent reverse engineering and avoid analysis.
Bitdefender researchers revealed today that their attention was caught up by processes that add local exclusions in Windows Defender for specific file names (prun.exe, appsetup.exe, etc.), that all reside in the same folder, called \PublicGaming\. Their investigation showed that this malware is a downloader that can deliver any payload to the infected system.
What’s more, the researchers revealed that MosaicLoader operators employed several tactics to obstruct their malware analysis efforts and to increase the malware’s success rate:
- Mimicking file information that is similar to legitimate software
- Code obfuscation with small chunks and shuffled execution order
- Payload delivery mechanism infecting the victim with several malware strains
How Does It Work?
Attacks involving MosaicLoader rely on an established tactic of malware delivery called search engine optimization (SEO) poisoning.
SEO poisoning is an old-school attack technique in which threat actors create malicious websites and utilize search engine optimization (SEO) strategies to make them appear prominently in search results. These websites are usually associated with words that large numbers of individuals use in searches at any given point in time, including holiday phrases, news items, and popular videos.
In this case, cybercriminals bought ad slots in search engine results to push malicious links as top results when users search for terms related to pirated software.
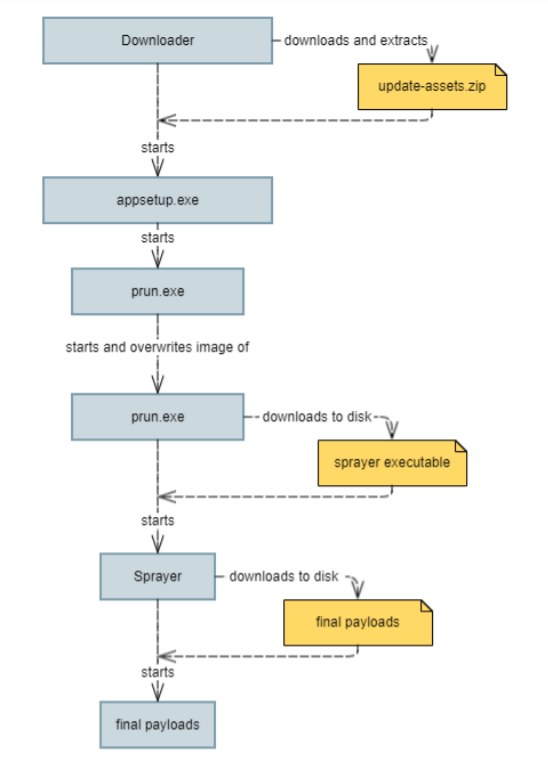
Execution flow
If the infection is successful, the first Delphi-based dropper (mimicking a software installer) acts as an entry point, fetching and adding the next stage payload from the remote server. To thwart antivirus scans, local exclusion in Windows Defender Two executable files are downloaded.
The dropper downloads update-assets.zip from the C2 server (checkblanco[.]xyz in our run) into the %TEMP% folder. The .zip file contains the two files required for the second stage, appsetup.exe, and prun.exe. Then, the dropper extracts these files to C:\Program Files (x86)\PublicGaming\ and launches several instances of Powershell to add exclusions from Windows Defender for the folder and the specific file names.
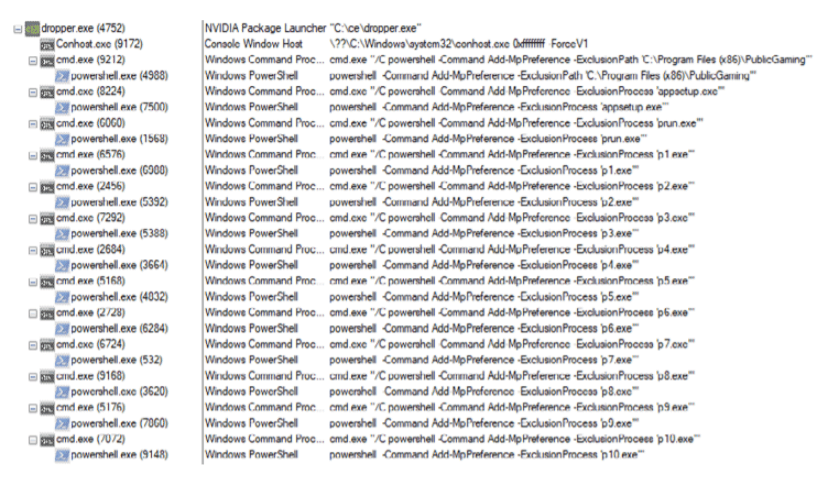
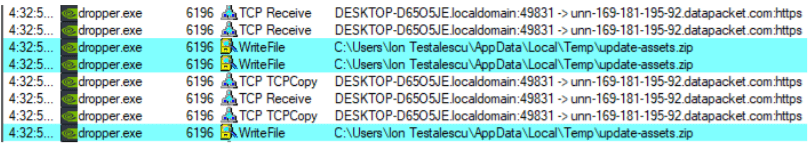
Since MosaicLoader has a wide range of features, multiple evolutions of advanced malware, including both public and customized malware, have been exploited by attackers to adopt compromised systems into botnets. According to the researchers, the malware sprayer can deliver Facebook cookie stealers on the system that might exfiltrate login data, resulting in complete account takeovers, posts that can harm the reputation of businesses or persons, or posts that spread malware. Other significantly dangerous malware delivered through MosaicLoader are the Remote Access Trojans. They can log keypresses on the system, record audio from the microphone and images from the webcam, capture screenshots, etc. With this private information, attackers can take over accounts, steal digital identities and attempt to blackmail victims.
The researchers added that the campaign has no specific target countries or organizations, but due to the nature of the infection source, they expect most of the infected systems to be personal computers.
Recommendations
The best way to defend against MosaicLoader is to avoid downloading cracked software from any source. Besides being against the law, cybercriminals look to target and exploit users searching for illegal software.
Make sure you always check the source domain of every download to check that the files are legitimate and to keep your antimalware and other security solutions up to date.
New types of malware are designed to evade traditional file-based antivirus detection. For this reason, you will need to install a more robust piece of software that can keep up with and protect your organization against evolved threats.
Our Heimdal™ Next-Gen Antivirus & MDM is a next-generation antivirus solution with four state-of-the-art malware detection layers and live process monitoring. In addition to this, it runs in the background without slowing the machines in your network down, which is always a plus.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security