Contents:
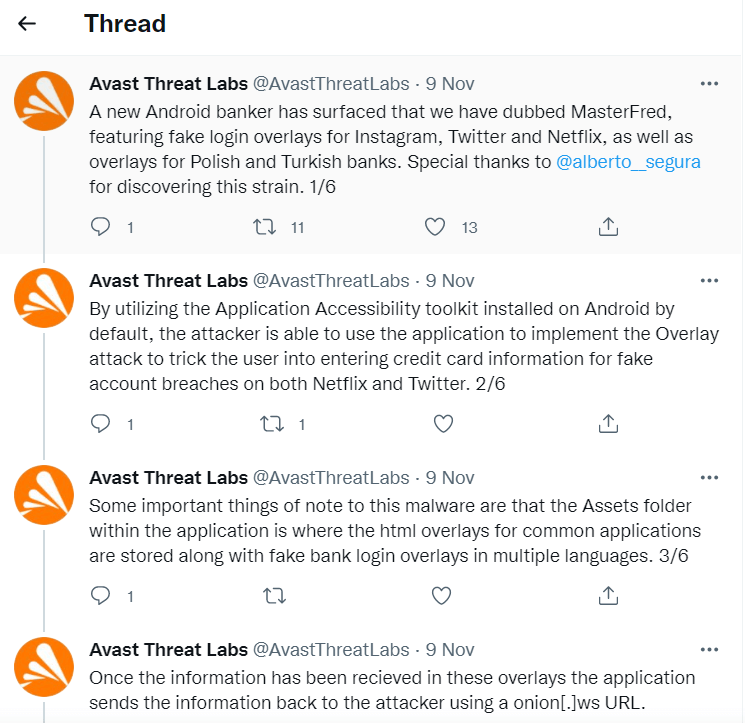
A new malware has emerged on the threat landscape scene. Dubbed MasterFred malware, this is designed as an Android trojan that makes use of false login overlays to target not only Netflix, Instagram, and Twitter users, but also bank customers. The hackers’ goal is to steal credit card information.
How Does MasterFred Malware Work?
According to BleepingComputer publication, MasterFred malware stands out through some specific characteristics:
- First thing first, the malware is distributed to Android devices;
- Some applications through which this kind of malware propagates also bundle the HTML overlays;
- Through these overlays, basically, false login forms are displayed in order to perform financial data theft from the users;
- Another particularity is that the onion.ws dark web gateway, also known as Tor2Web proxy is used by MasterFred, being effective in the stolen data delivery to Tor network servers belonging to operators that control this malware;
- It seems that third-party stores also represent delivery channels for this malware and there was reportedly also found one app in Google Play associated with the malware under discussion, according to Avast researchers.
We can say that at least one application was delivered via Google play. We believe that it has been removed already.
More exactly, cybercriminals use false Android applications resembling Netflix, Instagram, or Twitter and incorporate MasterFred inside them. A user will then try to create an account that will further require a username, password, and financial info.
Avast researchers analyzed this malware and how the cybercriminals implement the overlay attack by using the default Application Accessibility on Android.
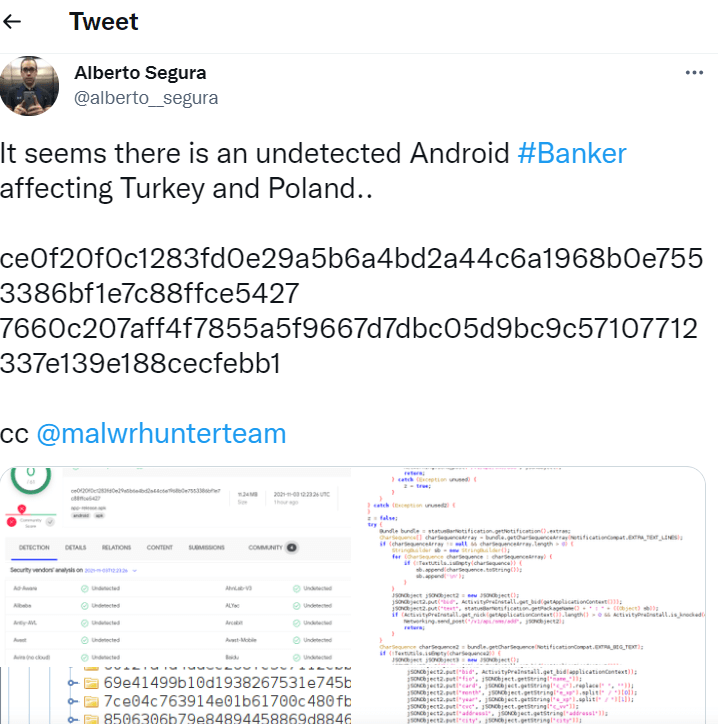
In the same Twitter thread, there are also Indicators of Compromise (IOC). Among others, one can find there, CC server domains and sample hashes of MasterFred malware.
The MasterFred Malware: Some Background
As the same publication mentioned above says, the submission to Virus Total of the first sample of the malware took place in June 2021. Then Alberto Segura, a malware analyst, has recently submitted another sample, showing how MasterFred targeted Poland and Turkey Android users.
How Can Heimdal™ Help You?
Heimdal™ is always updated and keeps pace with the latest cybersecurity trends, a quality that perfectly illustrates its products too. Our awarded Threat Prevention Endpoint solution uses Machine Learning, cybercrime intelligence, and artificial intelligence capabilities to help you prevent future threats with 96 % accuracy on your endpoints, a very efficient cyber threat hunting solution that makes malicious URLs, processes, and attacker’s origins no longer anonymous.
Did you enjoy this article? Follow us on LinkedIn, Twitter, Facebook, Youtube, or Instagram to keep up to date with everything we post!


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










