Contents:
Researchers discovered a new MacOS info-stealer that extracts documents, cookies, and login data from infected devices.
MacStealer uses Telegram as a command-and-control platform to exploit MacOS machines from Catalina (10.15) and up to Ventura (13.2). It is delivered on the dark web as a malware-as-a-service (MaaS), at a fairly low cost – $100 only.
At the moment, MacStealer is a work in progress. Its creators claim they will also add features to exfiltrate data from Apple’s Safari browser and the Notes app.
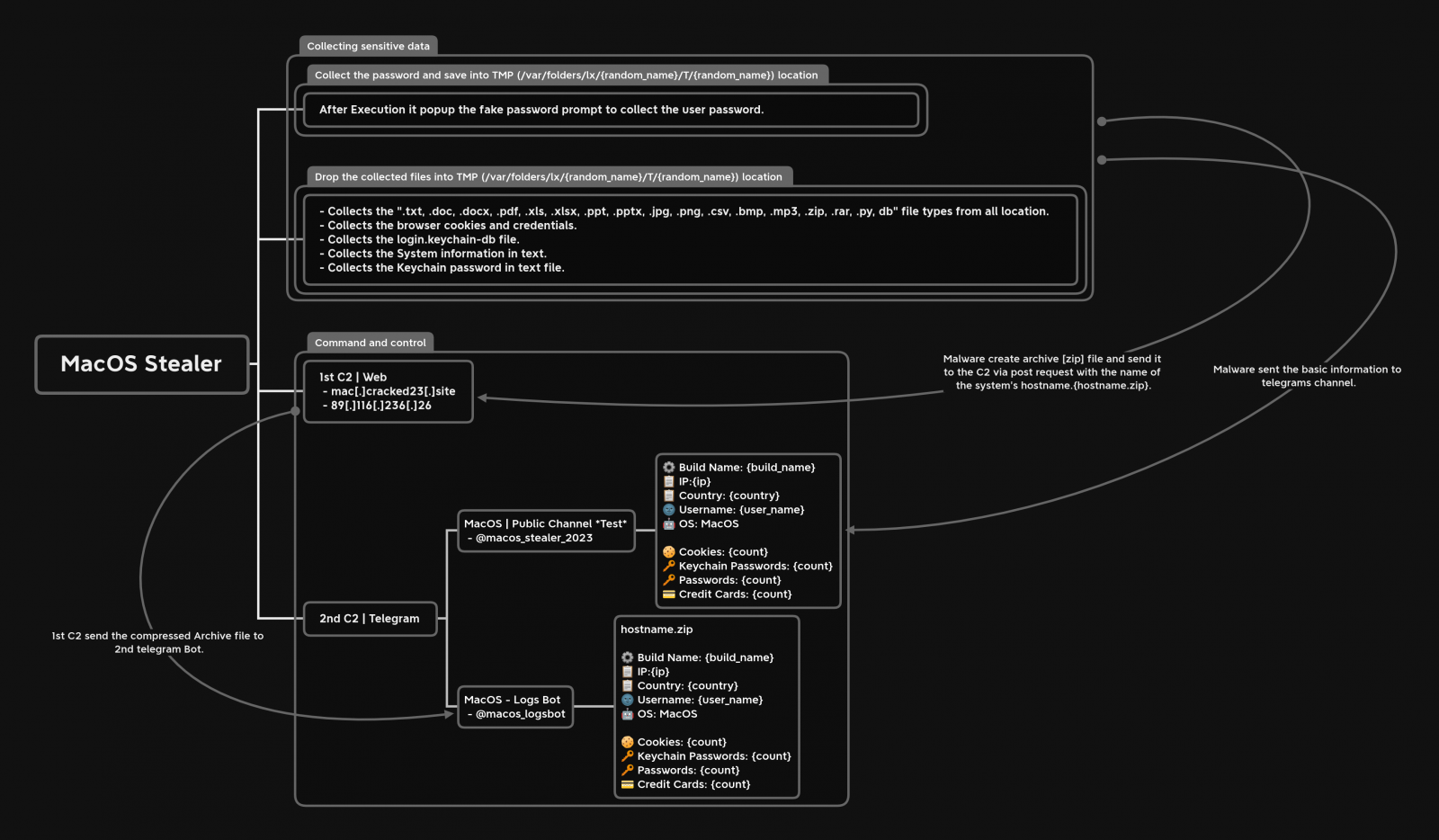
How Does MacStealer Work?
Threat actors trick the victim to execute the MacStealer, under the appearance of an unsigned DMG file, on their device. Then a fake password prompt pops up on the screen, pretending to seek access to the System Settings app. If enabled, the malware further collects passwords from the infected device.
The malware then exfiltrates the other types of data, stores them in a ZIP file, and sends the packet to the command-and-control servers.
At the same time, MacStealer sends some basic information to a pre-configured Telegram channel, allowing the operator to be quickly notified when new data is stolen and download the ZIP file.
What Kind of Data Is at Risk?
According to the threat actors that created it, MacStealer can now extract iCloud Keychain data, passwords, and credit card information. The malware gathers data from browsers like Google Chrome, Mozilla Firefox, and Brave. But the list of sensitive information that it can extract from an infected MacOS machine is much longer:
- Passwords, cookies, and credit card details that come directly from the browsers.
- Various format files: TXT, DOC, DOCX, PDF, XLS, XLSX, PPT, PPTX, JPG, PNG, CSV, BMP, MP3, ZIP, RAR, PY.
- Keychain database (Base64 encoded).
- System information.
- Keychain password information.
How to Protect Your MacOS Device from MacStealer?
As most MaaS target Windows machines, macOS can also fall victim to such attacks. So, cybersecurity specialists recommend users follow a basic set of best practices to protect their endpoints:
- Never download files from fishy websites.
- Keep your OS and security software up to date. Never miss a patch! Automated patch management solutions are also available for macOS, so go ahead and try one.
- Don`t click links that come from unknown sources.
- Don`t download files from unexpected, suspicious emails. You could be the victim of a phishing attack.
And if you liked this article, follow us on LinkedIn, Twitter, Facebook, and YouTube for more cybersecurity news and topics.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security







