Contents:
The LockBit ransomware gang has resumed using encryptors based on other operations, switching to one based on the Conti ransomware‘s leaked source code.
Since its inception, the LockBit operation has gone through several iterations of its encryptor, beginning with a custom one and progressing to LockBit 3.0 (aka LockBit Black), which is based on the source code of the BlackMatter gang.
This week, cybersecurity collective VX-Underground first reported that the ransomware gang is now using a new encryptor called ‘LockBit Green,’ based on the now-disbanded Conti gang’s leaked source code.
The Conti ransomware gang was forced to shut down following a string of embarrassing data breaches caused by the leak of 170,000 internal messages and the source code for their encryptor.
Soon after the source code was made public, other hacking groups began using it to develop their encryptors, some of which were used against Russian companies.
LockBit Green: A Look Under the Hood
Since the announcement of LockBit Green, researchers have discovered samples of the new encryptor circulating on VirusTotal and other malware-sharing websites.
After LockBit Red and LockBit Black, this is the third version of the ransomware created by the notorious gang. Affiliates of the Lockbit RaaS can obtain LockBit Green by using the LockBit portal’s builder feature.
The VX-Underground researchers confirmed the release of the new version:
Lockbit ransomware group has informed us they have acquired a 3rd ransomware variant.
– Lockbit Red
– Lockbit Black
– Lockbit GreenThey also have modified their ESXI ransomware variant.
Yes, they actually wrote “TLP:RED” in the image. pic.twitter.com/Oacbl2ZJk7
— vx-underground (@vxunderground) January 27, 2023
The operators have modified their ESXI ransomware variant, according to the researchers who analyzed the new version.
According to Antonio Cocomazzi, a senior threat intelligence researcher at SentinelOne, the new variant significantly overlaps the Conti ransomware, the source code for which was leaked months ago.
I analyzed the sample and found that it has significant overlap (89% similarity) with the Conti Ransomware, specifically its v3 version, which leaked the source code several months ago. In addition, the command line flags for LockBit Green are identical to those of Conti v3, making it a derivative of the source code.
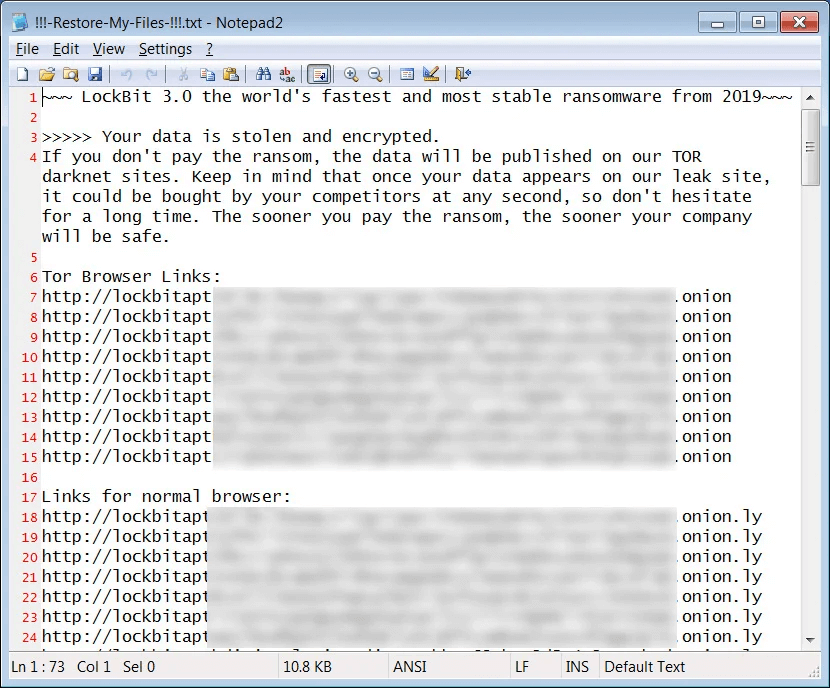
LockBit has modified only a tiny part of the source code, including the ransom note, which is identical to that used by LockBit Black.
Ransom note filename changed to “!!!-Restore-My-Files-!!!.txt”. As shown below, the ransom notes have been modified to use the LockBit 3.0 ransom note format rather than Conti’s.
With the source code for other malware, operators can create their version, improve it, and speed up the development process.
By reusing and adapting the source code of reputable competitors, such as Conti, #RaaS maintainers can maximize their release speed to attract new affiliates.
Researchers from Prodaft shared Indicators of Compromise for Lockbit Green along with the Yara rule for detecting its patterns.
While it’s still determined why LockBit is using a new Conti-based encryptor when their previous one is still operational, PRODAFT may have the answer.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, YouTube, and Instagram for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










