Contents:
A cyberattack on Royal Mail, the UK’s largest mail delivery service, has been linked to LockBit ransomware.
The Royal Mail announced yesterday that it has been experiencing severe disruption to international export services as a result of a cyber incident.
Royal Mail did not provide details about the cyberattack but said it works with external cybersecurity experts and has informed UK regulators and law enforcement. This attack used the LockBit ransomware encryptor.
A Little Background on LockBit Ransomware
In contrast to other types of ransomware, LockBit targets businesses and government entities mainly through malicious email attachments, lack of adequate email security, and cascading file system infections.
As of September 2019, LockBit has been used in major worldwide attacks. It was referred to as the “.abcd virus” due to its file extension when encrypting a victim’s files.
LockBit attacks have targeted organizations in the United States, China, India, Indonesia, and Ukraine, as well as European countries (France, the UK, and Germany).
Viable targets feel hindered by the disruption and have enough funds to pay a heavy sum. The relocation of these attacks can result in sprawling attacks against large companies, from healthcare to financial institutions.
You can read more about the Lockbit ransomware group here, where we’ve covered the subject in more detail.
The Telegraph first reported that the attack on Royal Mail was a ransomware attack by LockBit, or at least someone using their encryption software.
Ransomware encrypted devices used for international shipping and caused ransom notes to be printed on customs docket printers, according to The Telegraph.
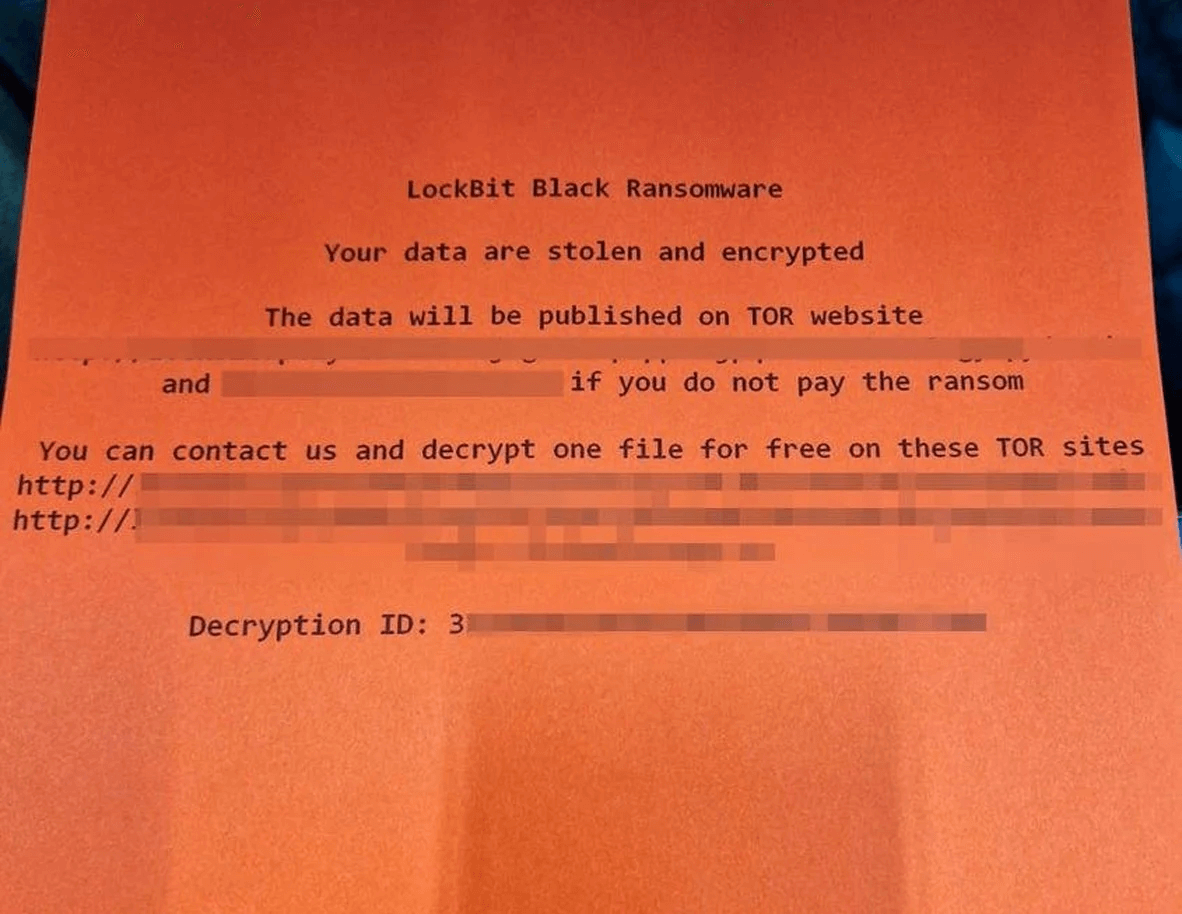
LockBit Black Ransomware, which includes code and features from the now-shutdown BlackMatter ransomware gang, created the ransom note.
There are links to the LockBit ransomware’s Tor data leak and negotiation sites and a decryption ID is required to chat with the threat actors.
Researchers and journalists are still determining whether the ransomware gang deleted the ID after news of the circulating ransom notes or moved negotiations to a new ID to avoid scrutiny.
LockBitSupport, the public-facing representative of the ransomware operation, told BleepingComputer that they did not attack Royal Mail and blamed other threat actors for using their leaked builder.
A leak of the LockBit 3.0 ransomware builder on Twitter allowed other threat actors to launch ransomware operations using LockBit.
Royal Mail’s ransom notes included links to LockBit’s Tor negotiation and data leak sites rather than the other threat actors who are allegedly using the builder, according to LockBitSupp.
As there is no way to contact the actual attackers, if LockBitSupp is telling the truth and other threat actors used the leaked constructor in the attack, this was likely a destructive attack rather than one for personal gain.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










