Contents:
It has been over a year since the Cloudstar ransomware attack, and Stephen Millstein, the CEO of Certified Title Corporation, still feels “something like PTSD” whenever he recalls what happened.
In the cyber attack on the cloud storage provider, Millstein’s title firm, Certified Title Corporation, founded in 1994, was among hundreds of firms impacted. According to Millstein, they housed the entirety of our business essentially.
I have compared it to waking up without credit cards, passports, IDs, or cell phones. How do you reestablish yourself when you have nothing to build on?
Millstein and Certified Title Corporation had been with Cloudstar for ten years at the time of the attack. The digital storage provider housed all Certified Title’s data and the company’s subscription to ResWare, its preferred closing software.
According to the American Land Title Association, Cloudstar operated six data centers in the United States at the time of the attack, serving over 42,000 users. As a result, hundreds of title companies and lenders could not conduct transactions or close loans due to the attack.
This attack served as a wake-up call to Milstein and many others in the title industry that even encrypted cloud storage providers were vulnerable.
“We got a phone call Friday morning around 10 telling us they were having a ransomware problem, but they did not offer any real details,” Millstein said. The word ransomware wasn’t familiar to me in the sense that it affected me; I had heard about it on the news, but this was the first time I had ever experienced it. So at first, I didn’t think much of it, thinking things would be fine by Monday.”
Millstein realized his mistake over the weekend. Ultimately, they got their data back from Cloudstar, but it took months.
Let’s dig deeper into how it all started.
How Did the Cloudstar Ransomware Attack Happen
A cloud hosting service provider based in Jacksonville, Florida, Cloudstar provides a wide range of IT security and consulting services and cloud backup services for businesses. Law firms, title companies, mortgage companies, and healthcare providers are some of the industries in which Cloudstar specializes.
On Friday, July 16, 2021, Cloudstar was the victim of a highly sophisticated ransomware attack.
As a result of the nature of this attack, their systems were unavailable at this time, and although they worked around the clock, they did not know when the plans would be restored. However, some support services, Office 365 mail services, and email security services are still available through Cloudstar.
Cloudstar has hired Tetra Defense to assist in its recovery efforts, and law enforcement has been notified. Moreover, all of their customers were informed and committed to helping them through this and working in the industry’s best interest. Negotiations with the threat actor were also ongoing.
Cloudstar confirmed on July 18, 2021, that the incident was related to a ransomware attack. Cloudstar worked to restore its systems over the following months. However, whether any consumer data was available to the hackers orchestrating the attack remains to be seen.
In a letter to its customers, Cloudstar still needs to explain the impact of the ransomware attack or how it affected their data.
However, due to the data breach, several Cloudstar customers have written letters explaining how it exposed their sensitive and personal information to unauthorized access.
By infiltrating networks with malware, ransomware criminals destroy companies’ data, crippling them. Only when victims pay up do they receive the decoder key. The costs of such attacks add up. Some experts say hackers collected $412 million in ransom payments last year.
A Comprehensive Look Into What Is Causing Data Breaches
In most cases, data breaches result from stolen or weak credentials. If malicious criminals have your username and password combination, they can gain access to your network.
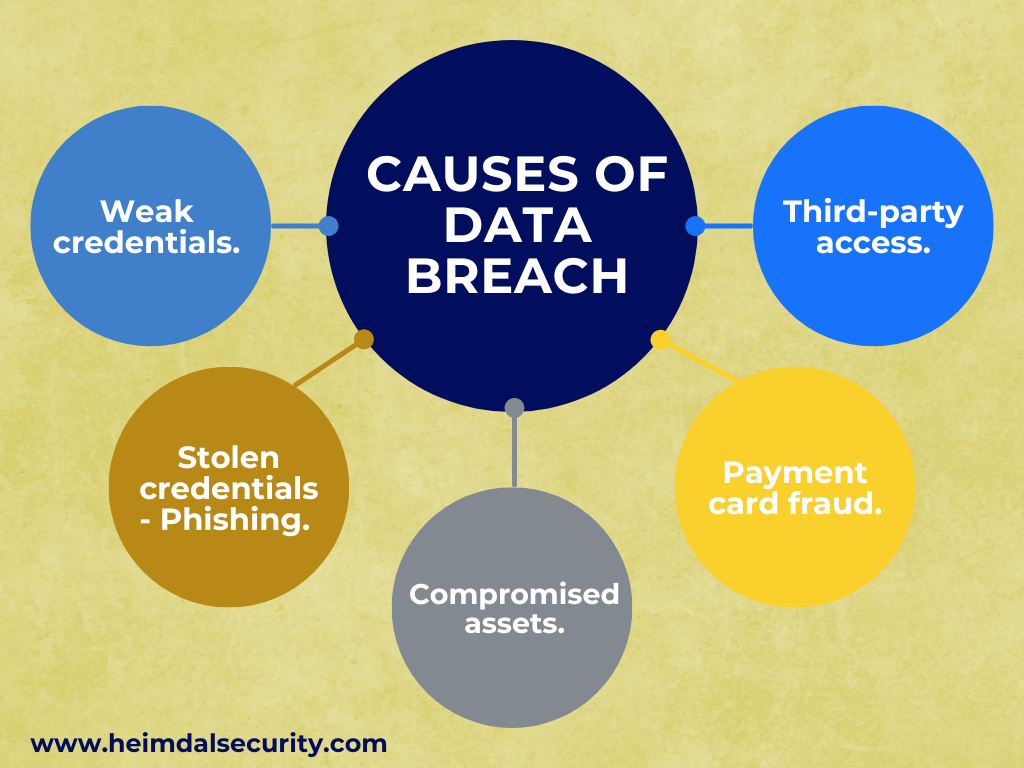
Cybercriminals can use brute force attacks to gain access to email, websites, bank accounts, and other PII or financial data sources because most people reuse passwords.
Once cybercriminals gain access to a computer network, they can access and remove any data stored on the compromised servers. Data breach victims can usually identify which files were accessed in most cases. Still, they may be unable to determine which files the hacker accessed or if any data was removed.
Having your sensitive information compromised in a data breach does not necessarily mean it will be used for criminal purposes. Still, it does put it in the hands of an unauthorized individual.
As a result, individuals who receive Cloudstar data breach notifications should be vigilant in monitoring for signs of unauthorized activity and take the situation seriously.
Data breaches cause victims also to suffer emotional distress and credit damage, and they may even end up with a criminal record. Taking immediate action is the best way to prevent the worst consequences of a data breach.
Cloudstar Data Breach: What Are Consumers’ Remedies?
Cloudstar customers assumed that their privacy concerns would be taken seriously when doing business with the company.
Of course, consumers would think twice before giving a company access to their information if they knew it wouldn’t be secure.
In light of this, data breaches like this raise questions about the adequacy of a company’s data security measures.
Any organization that accepts and stores consumer data also agrees with a legal obligation to ensure the information remains private when it does so. Consumers can pursue civil data breach claims against organizations that fail to protect their information under US data breach laws.
As a result of the Cloudstar data breach, the investigation is still in its infancy. Currently, no evidence suggests Cloudstar is legally responsible for the breach. However, that could change as more information about the breach and its causes becomes available.
How to Respond When You Receive a Data Breach Notification
You might receive a notification letter about a data breach if your information was compromised in the recent breach. Although this isn’t a time to panic, you should take steps to protect yourself from identity theft and other fraudulent activity.
Here are some essential steps you can take:
- Identify What Information Was Compromised: As soon as you learn about a data breach, you first need to review the data breach letter carefully. The letter will let you know the information accessible to the unauthorized party. Keep a copy of the letter and keep it for your records. A data breach lawyer can assist you if you need assistance understanding the letter or how to protect yourself.
- Limit Future Access to Your Accounts: It’s best to err on caution, so once you ascertain what data was affected, it’s time to take action. Change all passwords and security questions for any online account, including banking, credit card, shopping accounts, and anything else with personal info. Additionally, update your social media profiles’ passwords and take advantage of multi-factor authentication when you can.
- Protect Your Credit and Your Financial Accounts: Companies often provide affected parties with free credit monitoring services after a data breach. Signing up for free credit monitoring offers some significant protections. It doesn’t impact your rights to pursue a data breach lawsuit against the company if they were legally responsible for the breach. You should contact a credit bureau to request a copy of your credit report—even if you do not notice any signs of fraud or unauthorized activity. Adding a fraud alert to your account will provide you with additional protection.
- Consider Implementing a Credit Freeze: A credit freeze is an effective way to protect your credit report. Freezing your accounts restricts access, yet you can still temporarily unlock them if needed. It may seem excessive, but it’s worth the effort; the ITRC has reported that a credit freeze is the most effective step for preventing a new credit/financial account from being opened without permission. Yet few individuals (only 3%) affected by data breaches choose this option.
- Regularly Monitor Your Credit Report and Financial Accounts: In the wake of a data breach, you need to continue to monitor your credit report and financial accounts. You should regularly check your credit report and all financial account statements to detect any signs of unauthorized activity or fraud. Report the breach of your information to your banks and credit card companies.
Wrap Up
Undoubtedly, this was an incredibly difficult time for Cloudstar but, more importantly, for their customers.
Given the ongoing nature of the ransomware pandemic and the online disruption it causes, experts predict that ransomware and other types of cybersecurity crimes, both commercial and personal, will continue to rise. Cloudstar, one of the title industry’s primary cloud providers, is still vulnerable following the ransomware attack that disrupted its services.

Heimdal™ Ransomware Encryption Protection
- Blocks any unauthorized encryption attempts;
- Detects ransomware regardless of signature;
- Universal compatibility with any cybersecurity solution;
- Full audit trail with stunning graphics;
How Can Heimdal® Protect You From Ransomware?
Heimdal ® offers Ransomware Encryption Protection as part of its outstanding integrated cybersecurity suite, which is universally compatible with any antivirus solution and 100% signature-free, allowing superior detection and remediation of all types of ransomware.
Furthermore, Heimdal ® Patch & Asset Management, keeps hundreds of thousands of enterprise endpoints secure and up to date. Because of our quick response and implementation times, we keep our data updated at a much higher rate than industry benchmarks, but it still yields fascinating insights.
See for yourself by booking a demo!
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










