Contents:
A recently discovered malware called LilithBot is linked to the Eternity group, Zscaler researchers claim.
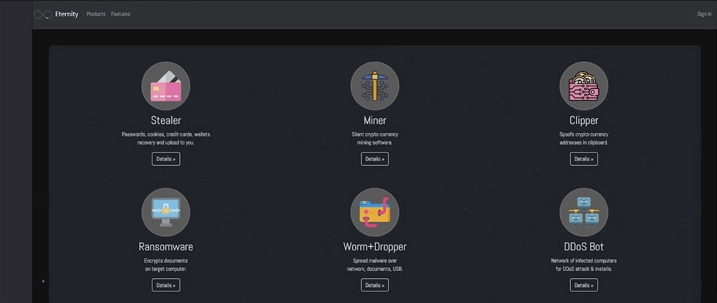
Earlier this year, Eternity Project came up on a Telegram channel advertising a toolkit which included a stealer, miner, clipper, ransomware, worm spreader, and a DDoS bot.
The threat actor behind the Eternity malware-as-a-service (MaaS) has expanded its arsenal and now there is another threat to put Internet users at risk.
The Latest Addition, LilithBot
Among the other “services” provided, the list now also contains LilithBot. The multifunctional malware bot is sold on a yearly subscription basis to other cybercriminals in exchange for cryptocurrency payment.
The group has been continuously enhancing the malware, adding improvements such as anti-debug and anti-VM checks.
According to Zscaler, once the threat actor registers the user on its botnet, all the gathered information, such as browser history, cookies, pictures, and screenshots, is compresses into a ZIP archive (“report.zip”) and exfiltrated to a remote server using the Tor network. Also, the malware seems to be using fake certificates to bypass detections.
Telegram as a Marketplace for Cybercriminals
With a Telegram channel with around 500 subscribers, the Eternity Project appears to be actively expanding. The channel provides cybercriminals with updates and instructions, as well as customer support. Furthermore, the group has been linked to the Russian “Jester Group,” which has been active since at least January 2022.
As BleepingComputer explained, a loose approach to moderating content and a free cross-platform instant messaging service, turn Telegram into the perfect place for hackers to run their business without having to resort to the dark web markets. The considerable number of users also means a wider audience of interested buyers for the stolen data.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, YouTube, and Instagram for more cybersecurity news and topics.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security







