Contents:
The ‘Eternity Project,’ a new malware-as-a-service, allows cybercriminals to buy a malware toolkit that can be “personalized” with various modules depending on the type of cyberattack being carried out.
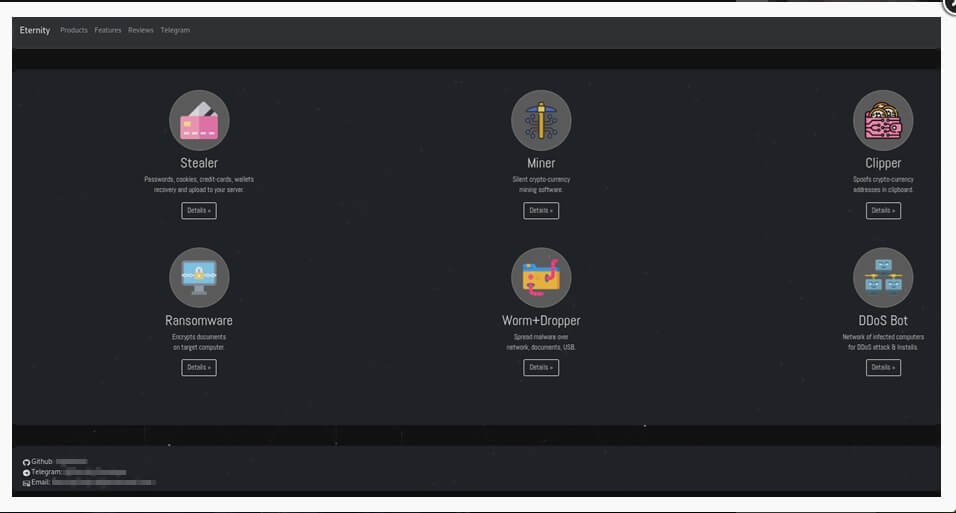
According to BleepingComputer, an info-stealer, a coin miner, a clipper, a ransomware program, a worm spreader, and, soon, a DDoS (distributed denial of service) bot are all part of the malware toolkit. They are also available separately.
The creators advertise all of the “goodies” on a dedicated Telegram channel with over 500 members, where they publish release notes for updates, usage instructions, and feature recommendations.
The malware kit buyers can use the Telegram Bot to automatically build the binary after choosing which characteristics they want to activate and paying for them in cryptocurrency.
What’s to Know About the Advertised Tools?
Let’s start with the info-stealer. This tool is available for the price of $260 per year and can steal passwords, financial information, tokens, cookies, and autofill data from more than twenty web browsers.
It also targets ten password managers, VPN users, messengers, and gaming customers, and it can exfiltrate data from cryptocurrency extensions or even cold wallets.
Then, we have the coin miner. This module, which costs $90/year, includes features such as task manager hiding, auto-restart when killed, and startup launch persistence.
Malicious actors can buy the clipper for $110. This utility searches the clipboard for cryptocurrency wallet addresses and replaces them with wallets controlled by the operator.
The threat actors charge $390 for the Eternity Worm, which can spread on its own via USB drivers, local network shares, local files, cloud drives, Python projects (via the interpreter), Discord, and Telegram accounts.
The last module, the Eternity ransomware module, is the most expensive, costing $490. It targets files, pictures, and databases and supports offline encryption using a combination of AES and RSA.
Surprisingly, the ransomware tool provides an option to set a timer that, when reached, renders the files fully unrecoverable. This way, the victim is pressured into paying the ransom demand more rapidly.
As per BleepingComputer, while the researchers who discovered the malware-as-a-service have yet to analyze all of the software components, they have seen samples of the malware spreading and being used in the wild, and all user comments on Telegram indicate that this is being a significant threat.
Even if it doesn’t appear to be dangerous right now, the malware’s additional modules, customer support, automated building, and specific instructions on how to use it make it a powerful tool in the hands of unskilled cybercriminals and a serious threat to online users.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










