Contents:
Oracle’s Java had been dethroned by Adobe’s Flash in 2014 in terms of Zero Day vulnerabilities and, for a while, it seemed like Java 8 was really capable of standing up to exploits and attacks.
The CISCO Annual Security Report 2015 reads:
Cisco Security Research suggests that the decline in Java exploits can be tied partly to the fact that there were no new zero-day Java exploits disclosed and available for adversaries to take advantage of in 2014.
Comparing it to 2013, last year was a quiet one for Java, with no major security incidents to rock the boat. But 2015 tells a different story.
After a half year dominated by Flash vulnerabilities and critical Zero Days, Java is stepping into the spotlight again.
As Java vulnerabilities piled up, Oracle released a Critical Patch Update Advisory this July, containing no less than 193 new security fixes! And there was the April 2015 Critical Patch Advisory (98 security fixes) and the January 2015 Patch Advisory before that (169 security fixes).
As you can tell, the patch advisories are being released more frequently to address serious security holes in the software that millions rely on.
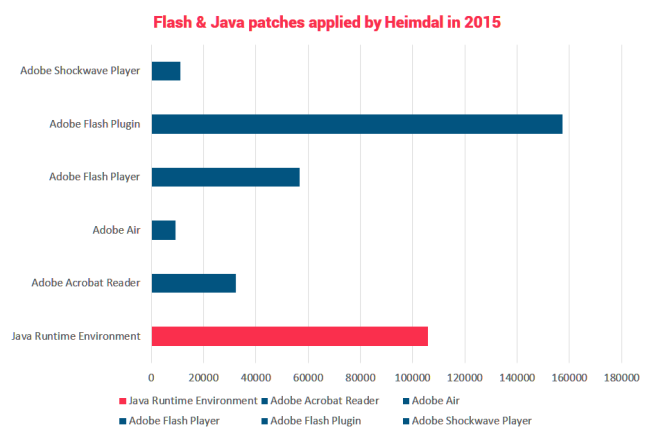
Moreover, data extracted from our own database confirms that Java is the second biggest security vulnerability that requires constant patching, after Adobe’s Flash plugin.
In 2015 alone, we’ve already deployed 105925 patches for Java Runtime Environment for our clients.
“Should I worry about this?”, you may ask.
To answer your question in a way that will really help you understand the risks, let’s look at the bigger picture for a moment.
Why Java is a “big deal”
There are at least a dozen software applications that we’ve been consistently using for years now. We install them after a fresh Windows installation, but we rarely consider if we really need them, what security risks they pose, etc.
Applications such as Java or Flash are familiar. They’re common. So they must be harmless.
After all, why would so many people choose to use software that has frequent security holes?
It’s true that, according to Oracle:
- 97% of Enterprise Desktops Run Java
- 89% of Desktops (or Computers) in the U.S. Run Java
- There are 9 Million Java Developers Worldwide
- Java is the #1 Choice for Developers
- Java is the #1 Development Platform
- 3 Billion Mobile Phones Run Java
- 100% of Blu-ray Disc Players Ship with Java
- There are 5 Billion Java Cards in Use
- 125 million TV devices run Java
- And 5 of the Top 5 Original Equipment Manufacturers Ship Java ME.
But why are these figures important?
Because when a Zero Day vulnerability hits Java, most of these users and companies are affected. It’s not just a minor glitch: it’s a threat that can endanger people’s finances and companies’ assets.
And it’s not just about Zero Days, as we’ll see next.
[Tweet “Do you know how Java can compromise your system’s security? Learn all about it.”]Understanding Java
Java is important, because it’s used in a huge variety of environments, from mobile phones, to corporate servers and supercomputers that are used in climate research, oil and gas exploration, molecular modeling and other highly complex fields.
Java is also important due to its pervasiveness. But being used by millions, on so many different platforms also means that inconsistencies, security holes and incompatibilities will arise.
Let’s try to better understand where security vulnerabilities come from.
According to Wikipedia:
There are a number of possible sources of security vulnerabilities in Java applications, some of which are common to non-Java applications and some of which are specific to the Java platform. (Note that these refer to potential sources of vulnerabilities which need to be kept in mind by security-conscious programmers: this is not intended as a list of actual vulnerabilities.)
Examples of potential sources of vulnerability common to Java and non-Java applications are:
- Vulnerabilities in the protection mechanisms provided by the hardware or operating system which the application relies upon for its security
- Vulnerabilities in native libraries, such as the C standard library, which may be used to implement the application and/or runtime
- Vulnerabilities caused purely by errors in user programs (for example improper construction of SQL queries leading to SQL injection vulnerabilities).
However, much discussion of Java security focusses on potential sources of vulnerability specific to the Java platform. These include:
- Vulnerabilities in the sandboxing mechanism which allow untrusted bytecode to circumvent the restrictions imposed by the security manager
- Vulnerabilities in the Java class library which an application relies upon for its security.
Another source for vulnerabilities is the fact that Java hasn’t released an automatic updater that doesn’t require user intervention and administrative rights. For example, Google Chrome and Flash Player have. This feature allows users to get automatic updates without being prompted to take action, making updates easier.
For lack of an automatic updates system, many users ignore Java updates and even fear installing them, because of malware that used Java updates as an infection vector in the past or similar experiences.
Just know that all these vulnerabilities are what cyber criminals thrive on.
The brief anatomy of a Java exploit
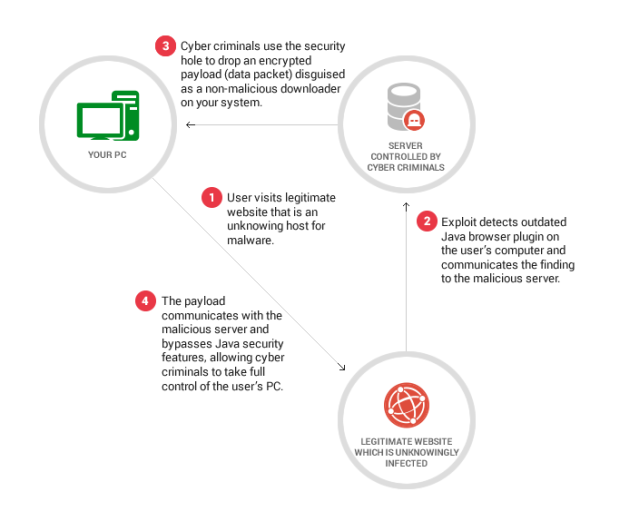
Each time you ignore an update prompt from Java, you’re putting yourself in harm’s way. That’s because cyber criminals have created and deployed fully automatic cyber attack mechanisms that work on their behalf.
First, they infect hundreds or thousands of websites with exploit kits.
Then, as you browse one of these websites (which could be a legitimate one, unknowingly hosting the exploit kit), the malicious mechanism looks for vulnerabilities in your system. So if you haven’t updated your Java plugin the last time it prompted you to do so, then you’re in danger.
Once the vulnerability is spotted, a payload will be dropped in your system, that will bypass security settings in Java and perform various actions, such as taking control of your computer, collecting confidential information (such as passwords or credit card information), etc.
Here’s a visual depiction of the process, to help you better understand it:
Without adequate protection, you’re a sure target for cyber criminals who specialize in employing exploit kits (explained below) to deliver malware attacks.
Since 2010, the Common Vulnerabilities and Exposures database has amassed 402 entries and 819 vulnerabilities for Java Runtime Environment.
In the past 5 years, Oracle has released 484 patches, but the database is not exhaustive, so the real number is probably much bigger than that.
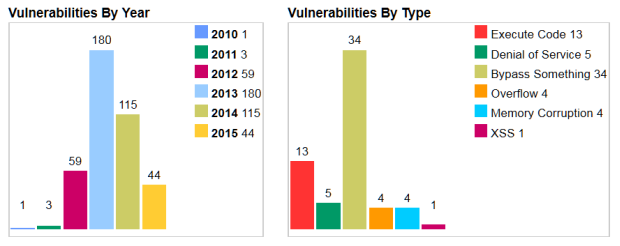
As you can see, most vulnerabilities in Java pose serious security risks, because they allow cyber criminals to execute code or bypass something (usually defense mechanisms), both situations being strong attack vectors.
And most of attacks which target Java are carried out via exploits. That why it’s important to know what they are and how they act.
[Tweet “Learn how cyber criminals use security holes in Java to infect your PC:”]Exploit kits targeting Java
As you’ve seen, 2013 was a tough year for Java. Two years ago, tech publications were asking the same question that they’re asking Adobe about Flash today:
After so many hacks, why won’t Java just go away?
But Java didn’t go away (just as Flash probably won’t), but Oracle really put its efforts into improving the product’s security.
In 2014, only 14,5% of exploits targeted Java, placing it third after Flash and Internet Explorer. That’s compared to 78% of exploits targeting the software made by Oracle in 2013 (source: Trustwave 2015).
Even from the Common Vulnerability Scoring System presented in Cisco’s 2015 Annual Security Report we can see that things improved substantially in 2014:
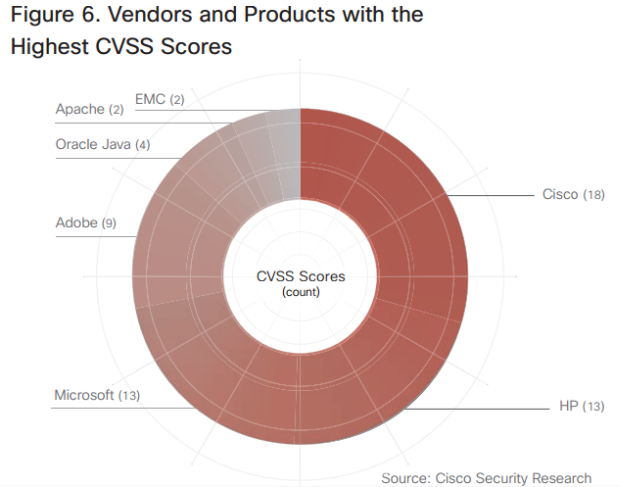
But Java is once again becoming a prime target for cyber criminals, with Zero Day vulnerabilities and security holes that offer abundant attack opportunities.
Exploit kits are an easy and relatively cheap way to take advantage of security issues, because the code is pre-written and can be bought on the black market. They also don’t require advanced technical knowledge to deploy and use.
So let’s see which exploit kits cyber criminals prefer and why when aiming to compromise Java, so you can know how to protect yourself against them.
Angler Exploit Kit
Angler is one of the most advanced exploit kits used today, because it uses a fileless dropper, which makes it impossible to detect for traditional antivirus products that scan your files for malware. Because there’s no file, the infection cannot be spotted, so you may be compromised without knowing it.
Here’s how Angler works to compromise Java, according to Trustwave 2015:
Angler also employs a JavaScript “plug-in detect” module to identify what versions of what browser plug-ins are present on a target machine. Only after verifying that the target is vulnerable will it follow with exploitation.
Magnitude Exploit Kit
At the beginning of 2014, Magnitude was generating more than $60,000 USD per week in income for cyber criminals. So you can imagine that it was pretty much the most famous exploit kit, because of its established infrastructure and big list of exploit options.
The main objective it was used for? To compromise Java.
At the height of its popularity at the beginning of 2014, Magnitude mostly relied on the exploit of three vulnerabilities: Internet Explorer (CVE-2013-2551) and Java (CVE-2012-0507 and CVE-2013-2463). Toward the end of 2014, Magnitude abandoned Java exploits entirely and instead began exploiting a flaw in Flash (CVE-2014-8439), along with the same once, CVE-2013-2551, in Internet Explorer.
Source: Trustwave 2015
Goon Exploit Kit
Goon was also on the list of exploit kits targeting Java in 2014:
As for the Goon exploit kit, Cisco Security Research points to its reputation for reliability as the likely reason for its modest but consistent popularity in 2014; it also has earned the distinction of being “the most organized” compared to other exploit kits. Originally discovered by security researchers in 2013, Goon—known also as the “Goon/Infinity exploit kit”—is a malware distribution framework that generates exploits for browser vulnerabilities pertaining to Flash, Java, or Silverlight components on Windows and Mac platforms.
Source: Cisco 2015 Annual Security Report
Sweet Orange Exploit Kit
Another trait of exploit kits is that they constantly morph to avoid being detected by traditional antivirus solutions. Here’s how the Sweet Orange exploit kit did it, according to the 2015 Cisco Annual Security Report:
The Sweet Orange exploit kit is also very dynamic; its components, ports, and payload URLs change constantly so that Sweet Orange can remain effective and avoid detection. This positions Sweet Orange as the “most likely to succeed” among exploit kits, according to Cisco Security Research.
Sweet Orange distributes a range of malware to unpatched end-user systems, and includes exploits for vulnerabilities in Adobe Flash Player, IE, and Java. Adversaries who use Sweet Orange often rely on malvertising to redirect users to websites—including legitimate sites—that host the exploit kit.
And, to make matters worse, cyber criminals are becoming increasingly skilled at evading traditional malware detection methods, such as antivirus.
Attackers have become more proficient at taking advantage of gaps in security to hide and conceal
malicious activity.
Flash malware can now interact with JavaScript to help conceal malicious activity, making it much harder to detect and analyze.
In 2014, Cisco Security Research observed growth in the use of Flash malware that interacts with JavaScript.
The exploit is shared between two different files—one Flash, one JavaScript. Sharing exploits over two different files and formats makes it more difficult for security devices to identify and block the exploit, and to analyze it with reverse engineering tools. This approach also helps adversaries to be more efficient and effective in their attacks.
For example, if the first stage of an attack is entirely in JavaScript, then the second stage, the payload transmission, would not occur until after the JavaScript executes successfully. This way, only users who can run the malicious file receive the payload.
Source: Cisco 2015 Annual Security Report
So there is definitely no shortage of exploit kits and other malicious tactics that take advantage of Java vulnerabilities. But because the 2015 Java patches were less than perfect, Zero Day vulnerabilities have started to show up more often. And that’s a serious issue, just like in the case of Adobe Flash.
Recent Java Zero Day vulnerabilities
Zero Day vulnerabilities are especially dangerous, because they expose security holes that are unknown to software vendors. In this context, cyber criminals have the advantage of speed and flexibility, so, before the vendor can patch the issue, multiple attacks targeting that security flaw are already launched.
If they don’t employ adequate security measures, users are caught in the middle and often become victims of cyber crime.
Java Zero Days are feared. They make headlines and they’re the sort of stories that friends share among themselves to make sure the news reaches everyone. There’s even a website that will tell you how many days have passed since the last known Java Zero Day exploit.
For example, on July 11, TrendMicro found that an APT (Advanced Persistent Threat) group was exploiting a Zero Day vulnerability in Java to compromise its targets, usually institutions in the West, such as NATO or the EU, but also other targets in the US.
The vulnerability was confirmed in JavaJRE verison 1.8.0.45 and it was used to install a backdoor on vulnerable systems. In the first stage, the exploit ran code in memory, which installed a dropper that connected to a series of domains which downloaded the main component. That main component bound the machine into a botnet, later employed in spear phishing attacks.
This particular cyber attack campaign targeted both Windows and Linux installations, and distributed malware via email with a web link that the victim was lured into clicking.
Four days later, on July 15, Oracle released a solid quarterly update to patch this issue. But imagine how many victims cyber criminals could have affected in this time-frame – yet another reason to be concerned about cyber security and your online protection.
So how do you protect yourself from cyber threats targeting Java?
There are a few sound rules that can keep you safe from cyber attacks, exploit kits that spread malware and the vulnerabilities that can compromise your PC.
1. Software updates – just do them! Do them fast, manually or automatically, in the evening or in the morning, at work or at home. But seriously, just click on them. Having the latest patches installed is vital, as you’ve seen, and can save you a ton of trouble!
2. Use a strong antivirus. It may not be able to protect you from all threats, but it’s important to have one installed, so it can catch infections before they spread and wreak havoc.
3. Use a security tool that can block advanced malware. You need a first line of defense, a product that will scan your traffic for threats and block malicious websites and infected banners before they can infiltrate your system. Look for options, do a bit of research and invest – it’s definitely worth to have peace of mind when surfing the web.
4. Secure your browsers! There are many security and privacy options in your browser that you can use to increase your protection. And this guide we created will help you seriously enhance your defenses.
[Tweet “These 5 simple tips can protect you against Java exploits!”]
5. Educate yourself on cyber security issues. Just taking the time to teach yourself about cyber security can be a fantastic asset! By understanding key concepts in the field, you can learn how to keep away from threats, how to choose the best security products for your PC and how to limit your exposure to malicious actions. Our Cyber Security for Beginners course might just do the trick.
Friendly reminder: these rules are useful to follow even if you don’t use Java or Flash. They’re not the only pieces of software that can expose you to cyber attacks.
And there’s always option number 6: to just uninstall Java altogether.
Could you live without Java?
Martin Brinkmann experimented with this and he lived to tell, so it’s not impossible and not even a huge hassle.
If you feel that you can do this, just hit uninstall and get rid of one more security risk. It’s important to keep your computer clean and running well, to get rid of old software you don’t use anymore, so a bit of summer cleaning can’t hurt.
Conclusion
As the numbers show, Java is still one of the 8 most vulnerable software apps exposing your computer to cyber attacks.
Will it be able to bounce back as it did in 2014 or will the situation get worse?
We couldn’t tell, but what we do recommend is to keep an eye on the situation, if you choose to continue to use Java.
Also, it’s wise, both for home users and especially for companies, to employ an automatic patching solution that can take care of delivering both feature and security patches as soon as they’re available, automatically and silently.
This can be especially useful, since it will cut down on the time you spend managing your software and it will also increase your security level substantially.
Have you ever been in a situation where malware targeted a Java vulnerability and compromised your system? Share you experience below.

INSTALL IT, FORGET IT AND BE PROTECTED
Download Heimdal™ FREE









 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security








