Contents:
Mustang Panda, a threat actor reportedly related to China, has been waging a harmful campaign with a new version of the Korplug malware known as Hodur and custom loaders for a period of at least eight months, according to security specialists.
Who Is Mustang Panda and What Is Korplug Malware?
Mustang Panda, also known as TA416, was reported to support China-aligned purposes and has recently been linked to phishing and espionage activities aimed at European diplomats.
Korplug is a proprietary virus used widely, but not solely, by this threat actor. It was initially uncovered in a 2020 investigation that looked into Chinese threat actors’ activities against Australian targets.
How Does the Mustang Panda Hacking Campaign Work?
ESET researchers published a report on how this Mustang Panda hacking campaign unfolds. Mustang Panda employs phishing lures with counterfeit papers to target European embassies, ISPs (Internet Service Providers), and research institutes in the most recent known campaign, as experts from ESET underline.
As of March 2022, this campaign is still ongoing and goes back to at least August 2021. Known victims include research entities, internet service providers, and European diplomatic missions. The compromise chain includes decoy documents that are frequently updated and relate to events in Europe. The campaign uses a custom loader to execute a new Korplug variant. Every stage of the deployment process utilizes anti-analysis techniques and control-flow obfuscation, which sets it apart from other campaigns.
The hackers have updated their lures numerous times since August 2021, when the campaign is thought to have begun, the most recent ones being issues relating to Russia’s invasion of Ukraine, COVID-19 travel restrictions, or European Union Council’s website’ documents, as BleepingComputer publication explains.
Mustang Panda Is Enhancing Its Toolset
The targeting goal of Mustang Panda has not changed over the years. However, when speaking of renewing lures and enhancing toolset, it seems that this threat actor is working on some improvements in that direction.
ESET claims to have sampled sophisticated custom loaders as well as new versions of Korplug that still use DLL side-loading. However, what’s noticed to have changed is the level of obfuscation and the anti-analysis methods across the infection chain.
To bypass detection, the malicious module and the encrypted Korplug payload are downloaded together with a decoy document and a legitimate executable, and their execution is put together for DLL side-loading purposes.
In the researchers’ report, Korplug’s loading chain was depicted:
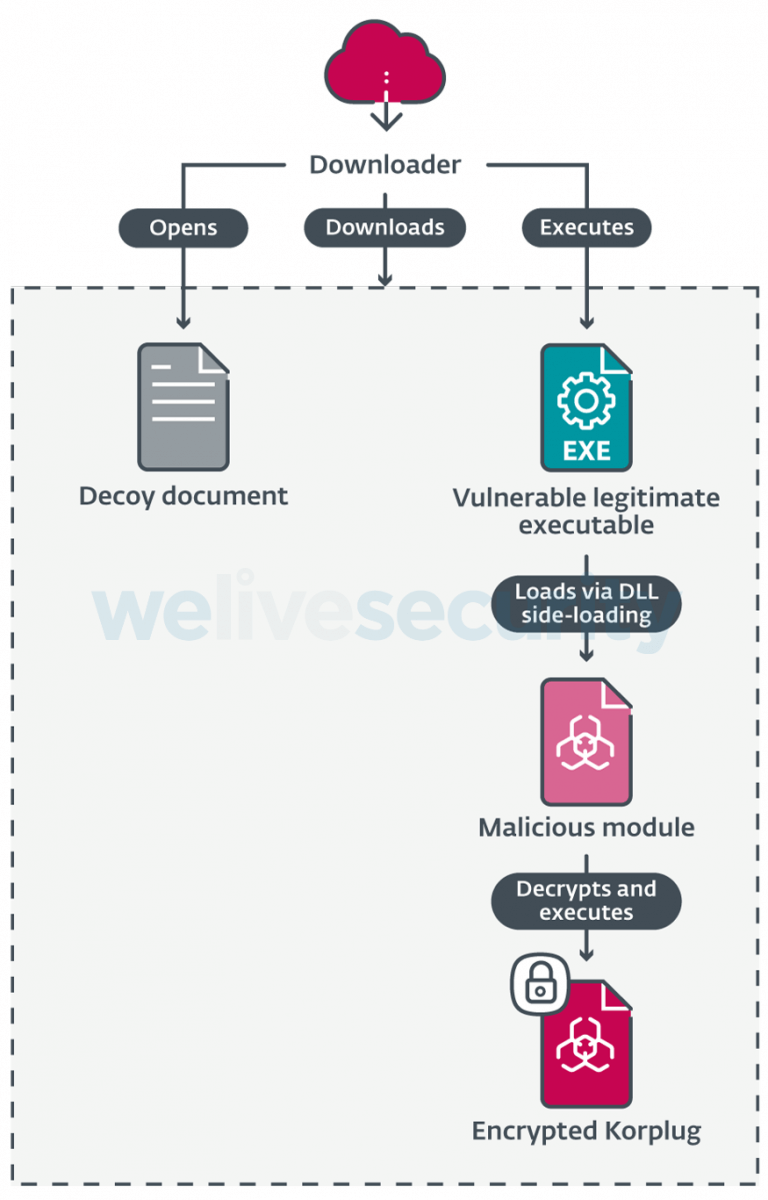
What is the side-loading custom DLL loader employing is a digitally-signed genuine executable, in this case, a SmadAV file. Besides, a known flaw is also exploited.
The various functions that the loader exports show a bogus nature, however, out of all these, one stands out and it’s precisely the one that loads the new Korplug variation.
Which Countries Are Impacted?
As the experts mention in their report, the following countries are impacted by this Mustang Panda hacking campaign.

New Backdoor Version Emerging
Korplug is a remote access trojan (RAT) whose functionality has yet to be properly investigated, possibly due to the large number of versions made by each APT that uses it.
Korplug’s variant THOR, a PlugX version uncovered by Unit 42 researchers last year, shows close similarity to the one utilized by Mustang Panda in the campaign under discussion.
Korplug payloads are decrypted in memory, and only the encrypted version is written to disk. All strings are likewise encrypted, and Windows API function calls are obfuscated, with anti-execution protections in place.
How does the threat actor achieve persistence? By creating a new registry entry for “Software\Microsoft\Windows\CurrentVersion\Run”, and marking the newly formed malware component directories as “hidden” and “system.”
The updated version’s changes can be found under Korplug’s RAT section, where the writers have improved it with more commands and functionality.
The commands supported by the first handler of the specific Korplug variant are Ping, GetSystemInfo, ListenThread, ResetConnection, Uninstall, and Stop.
The second handler receives a distinct range being described as more advanced.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security