Contents:
As Daniel Wanderson wrote for Security Boulevard, a CEO must consider every aspect of his/her business – and cybersecurity is one of the most important ones since anyone can become the victim of a cyber attack. At any minute, you face external threats. At any minute, you face internal threats. It’s crucial to know how to combat all of them.
Internal Threats: Definition
Internal threats are very much related to the concept of insider threat – the malicious threats that organizations face from employees, former employees, business associates or contractors. In one of my previous articles, I’ve already mentioned that these people have access to inside information related to the company’s data, computer systems, security practice, so any fraud, theft or sabotage from their part would hover over the organization’s security.
Internal threats refer to the risk posed by someone from the inside of a company who could exploit systems in order to steal data or cause any sort of damage.
Types of Internal Threats
What are the most common and dangerous types of internal threats? See below!
Unauthorized employee access
For various reasons, employees might try to obtain access to parts of a system they don’t usually work with. They might also have or obtain “administrative privileges that allow them to perform further administrative functions, such as changing the access rights of other users or deactivating network security tools. These issues can be a key point for launching further attacks”.
Accidental disclosure of data
Malicious behaviour can lead to simple incidents or cause a lot of damage, but so can accidents: company devices can be forgotten somewhere, potentially exposing sensitive information, folders might be accidentally deleted or drinks can be spilt laptops or phones at any time.
Social engineering
Although social engineering is, in itself, an external threat, it can only work if someone inside a company reveals information. To succeed with their malicious purpose, hackers might pretend to be friends or other trusted persons. They will thus request sensitive information or even offer unexpected prizes.
You can find more information on the tactics that social engineering uses in one of the articles of my colleague Miriam.
Illegal activities
It’s important to remember that, as an employer, you are responsible for pretty much anything your employees do when using your computer network — unless you can show you have taken reasonable steps to prevent this. Unfortunately, it’s not totally uncommon for employees to download pornography, or sell drugs and sexually offensive materials using the company email.
Physical theft of company devices
Especially today, with the rise of work from home policy due to the Covid-19 pandemic, employees often take their work computers out of the office. Even if they do not have malicious intentions, theft might still happen if they visit a client and bring their devices with them or attend an industry event. For this reason, it’s important to make sure that no outsider can access your company devices if they encounter one.
Moreover, hard drives containing sensitive information can be stolen or the data on it can be transferred to a USB flash drive and then deleted. Other attempts to sabotage a business can be disguised as fire, floods, power loss.
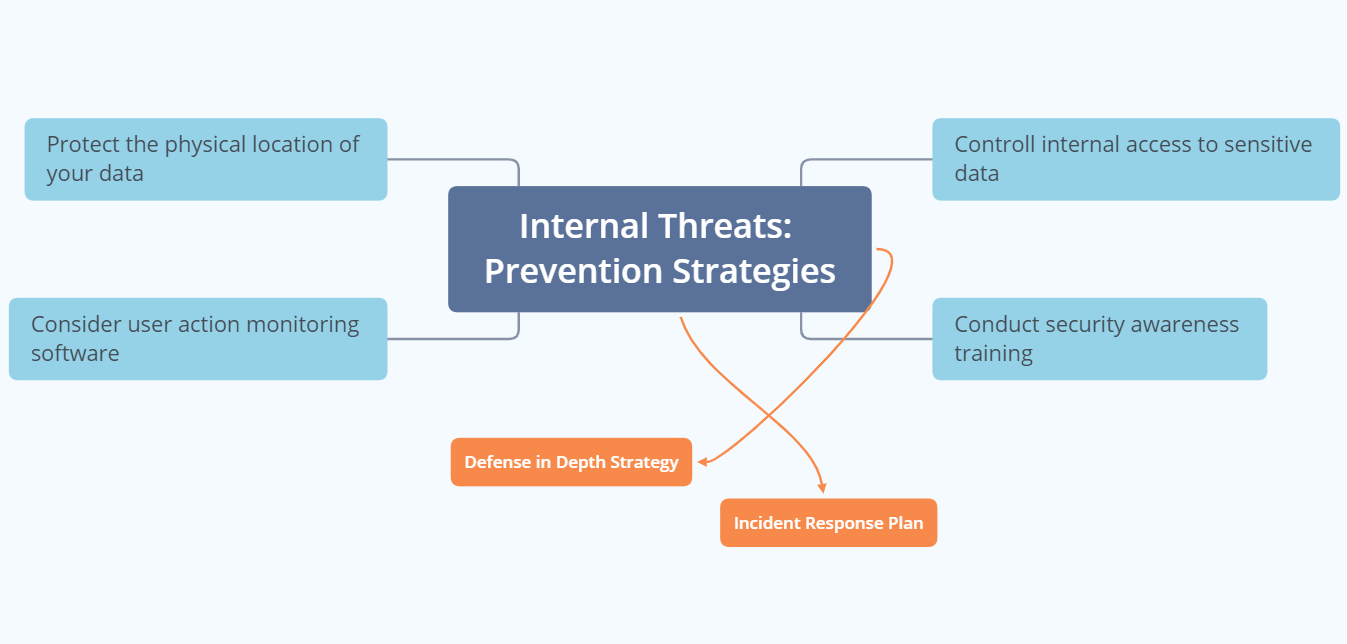
Internal Threats: Prevention
What can you do to prevent internal threats? Well, you can try the following measures:
1. Protect the physical location of your data
If you’re storing your data locally, the servers must be protected. Think about hiring a security guard or installing an efficient digital lock.
2. Consider user action monitoring software
A monitoring software will allow you to have full visibility into the actions of your system’s users, including video recordings and it will help you investigate any suspicious or malicious activity easier.
3. Controll internal access to sensitive data
This is a key step in ensuring the cybersecurity of your company. We suggest applying the principle of least privilege – “the concept refers to users not being able to access information or perform actions unless they absolutely must in order to do their jobs” – and thinking about a solution that can help you automate the process.
Our Privileged Access Management can manage user permissions easily, handle all requests and strengthen your endpoint security with truly innovative access governance, offering you full compliance and higher productivity.
Heimdal® Privileged Access
Management
4. Conduct security awareness training
IT security training and education should be a priority to any company that wants to avoid time loss, money loss, brand damage and legal actions due to cybersecurity incidents. Prevent internal security threats and careless mistakes by telling your staff about cybersecurity threats and making sure they know what to do and how to report if they notice suspicious behavior. The more your employees will know, the more they can help you keep the company safe.
All these should be a part of what is called defense in depth strategy. Also, you shouldn’t forget about developing an incident response plan. You can find more information about these concepts in two of my previous articles.
Wrapping Up
Internal threats presuppose unauthorized employee access, accidental disclosure of data, social engineering, illegal activities, physical theft of company devices. All of these aspects could lead to countless unpleasant consequences for any company.
If you’re interested in preventing cyberattacks and not responding to them, please remember that Heimdal always has your back and also that our team is here to create a cybersecurity culture to the benefit of anyone who wants to learn more about it.
If you liked this article, follow us on LinkedIn, Twitter, Facebook and YouTube, for more cybersecurity news and topics.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security









